The Magnitude of the Cyber Threat Problem
Earlier this year, CNN stated that 39 Billion was stolen on-line in 2011. This Fall, Symantec calculated that the total cost of cyber crime in 2012 will reach 110 Billion. As Dmitri pointed out, every company has been compromised in some way. Advanced Persistent Threats are expected to continue increasing as shown below.
Over 50% of APTs Target:
|
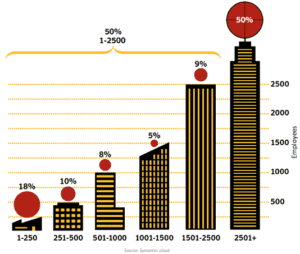 |
Source: Symantec
NOTE: This is part 2 of a 3 part blog on Internet Threat Defense Solutions. You should begin with Part 1.
What is the largest online threat source? One in five online adults (21%) has been a victim of either social or mobile cybercrime (BYOD) and 15% of social network users reported someone hacked into their profile and pretended to be them.
How APTs Penetrate Best Security Efforts
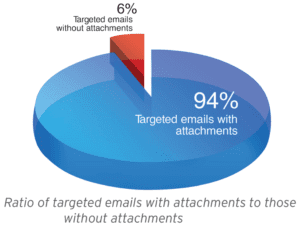
Trend Micro found that 91% of targeted attacks involve spear-phishing emails, reinforcing the belief that spear phishing is a primary means by which APT attackers infiltrate target networks. Using this type of attack, a target recipient is lured to either download a seemingly harmless file attachment or to click a link to a malware- or an exploit-laden site. The file, often a vulnerability exploit, installs a malware in a compromised computer. The malware then accesses a malicious command-and-control (C&C) server to await instructions from a remote user. At the same time, it usually drops a decoy document that will open when the malware or exploit runs to hide malicious activity.
 |
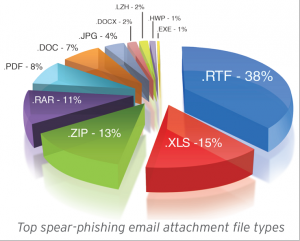 |
According to Trend Micro, Spear phishing remains the most favored vector for instigating targeted attacks. Why? Because users continue to fall prey to spear-phishing emails, causing substantial damage to their respective organizations. Spear-phishing email attachments are difficult to spot from normal document attachments passed on from user to user each day in a corporate environment, increasing the likelihood of successful computer infection.
Detecting Malware and APTs
According to a paper published by MANDIANT, only 24% of all the APT malware was detected by traditional anti-virus and anti-malware programs that most organizations use. The APT malware hides in plain sight and avoids detection by using common network ports, process injection and Windows service persistence. Every piece of APT malware initiated only outbound network connections. No sample listened for inbound connections. Unless an enterprise network is specifically monitoring outbound network traffic for APT-related anomalies, it will not identify the APT malware beaconing attempts.
“We expect Cyber Criminals will continue to use this method and as a result, in 2013, we are likely to see significantly more targeted attacks and targeted malware.”
Jagdish Mahapatra, Managing Director, McAfee
The APT intruders exfiltrate data in myriad ways, but MANDIANT has witnessed them using the same tactics at a number of victim organizations. The most common techniques are:
- The use of “staging servers” to aggregate the data they intend to steal.
- Encryption and compression of the data they steal.
- Deleting the compressed files they exfiltrated from the “staging server”.
The staging servers are usually identified when a compression utility, such as RAR, is found on the system. A forensic review of the system can result in the recovery of many compressed RAR files. However, these RAR files may have originated from another system accessed by the intruder in the network.
APT malware often communicates through the use of HTTP request headers within GET and POST requests and most proxy servers will assume the traffic is legitimate. Other times they use chat protocols which offer the attackers command shells and file transfer abilities to and from the infected machine. Also, the attackers typically operate late in the night (U.S. time) between the hours of 10 p.m. and 4 a.m. These times correlate to daytime in China.
MANDIANT also stated in the above paper that detecting an APT is incredibly difficult and many organizations are not prepared to effectively identify that they have been compromised. In most cases, initial notification of an APT intrusion originated from a third-party, primarily law enforcement. The primary reason organizations fail to identify the APT is that most of their security devices examine inbound traffic at the perimeter. Most organizations rely solely on antivirus solutions to provide host-based monitoring. In addition, implementing the ability to monitor internal to internal communications on a network is costly and challenging.

