If you’re an avid follower of our blogs, then you know that network threat detection using NetFlow analytics is a valuable enhancement to network monitoring. So then, integrating NetFlow and SIEM solutions takes network security to the next level, combining the ultimate threat detection solution with your existing Security information and event management solution.
Isn’t a SIEM enough?
So, you say, I already have network security monitoring in place with my SIEM solution. Why do I need more?
With NetFlow, security monitoring easily becomes cyber security monitoring, detecting DDoS attacks, malware outbreaks, data exfiltration, and much more.
This NetFlow cyber security monitoring is based on network traffic algorithms – pattern matching on specific traffic patterns indicative of malicious behavior. The algorithms are constantly searching for the patterns indicating threats, then generating alarms based on those violations. In addition to the generation of alarms, alerts can also be sent in the form of syslogs or snmptraps, which is where your SIEM solution comes into play.
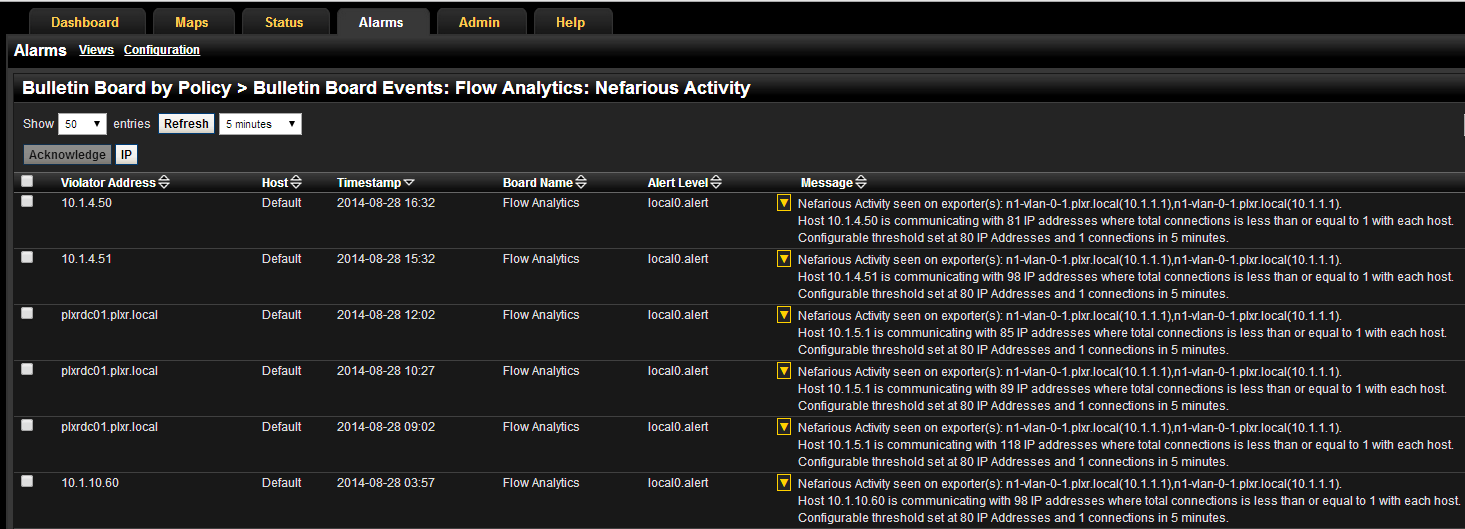
Your SIEM is already gathering large amounts of log data from many different sources (network devices, servers, applications, databases, etc.).
Adding the cyber threat alarms generated from the NetFlow threat detection algorithms to this log collection provides more focused data to include in the data aggregation. Also, you now have more finely tuned logs to correlate with the logs coming from the other sources on your network that you are already collecting from. Lastly, adding the cyber security threat alarms to your SIEM provides the ability to centralize your alerting/notification methods and log retention compliance requirements.
NetFlow integration
Cyber security threat detection is provided by NetFlow. Log collection and management is provided by the SIEM. Combined, they create a very powerful incident response solution suitable for the Enterprise network you have.
Taking it further, it’s not just cyber threats that NetFlow analyzing can provide. Cyber threats are the current big ticket items in network threat detection, including threats such as malware command and control servers, botnets, port scans – but it doesn’t stop there.
In addition to those network threats, you can also detect malicious or unwanted traffic unique to your environment. For example, let’s look at higher education. They may need to know if there is any unauthorized access to their grade servers by students. Creating a custom algorithm that would filter out all allowed traffic to the server and then alarming on any other traffic would quickly provide a list of potential culprits.
That information, in log format, could then be forwarded on to your SIEM, to correlate with other logs collected and also utilize the existing notification structure, and stay within the required data retention of the logs.
If this totally fascinates you and you’d like to see how you can integrate network threat detection via NetFlow with your existing SIEM, please give us a call.




