Many devices that are placed on the corporate networks can fly under the radar of the IT departments watchful eye. These devices include smart phones, wireless access points, tablets, home laptops and other types of computer hardware. In some cases, employees make VPN connections from non-corporate owned computers and leave them connected for days or even weeks. All of these devices take up corporate resources and put the company at greater risk for malware and electronic theft. What can be done?
First Strategy
One strategy involves disabling ports at the access switch that are not in use. This is a decent strategy except that it requires well maintained documentation as to what is plugged in and where. Keep in mind that users jump around and don’t always tell the helpdesk. This strategy also can lengthen some trouble shoots when the tech wants to plug a user into another port down at the wiring closet for quick testing. It becomes different if the spare ports have all been disabled. This strategy also doesn’t work for wireless devices. For these reasons, this “lock down” strategy can cause excessive administrative overhead, doesn’t address wireless users and it also doesn’t identify software applications.
Second Strategy
A second strategy involves authenticating a specific MAC address onto the network. This strategy is useful in wireless environments where the same device authenticates once and is able to roam around and gain network access via other wireless access points because its MAC address never changes. However, each newly added device requires a call to the helpdesk with knowledge of that devices MAC address. Again, this strategy causes excessive administrative overhead and it doesn’t identify software applications.
Third Strategy
A third strategy called identity services is sometimes implemented which uses radius authentication, Cisco ISE, Mobile IAM or 802.1x. In this technology, the switch communicates with the authentication server to validate users onto the network. The 802.1x architecture requires a client to be installed on the devices that need to authenticate. It is tough to implement because some devices can’t authenticate. To deal with this, you have to exclude ranges of IP addresses or mac addresses from the 802.1x authentication. Don’t forget to exclude the printers. And the IP phones. And the IP cameras. And the temperature probes. And the UPS devices. And the other devices that don’t support 802.1x. And again, it doesn’t identify software applications.
Fourth Strategy
A fourth strategy is an amalgamation of security efforts:
- Domain Authentication where end users must enter a username and password to gain access to internal resources (e.g. servers)
- Single sign on at the firewall where end users enter a username and password to gain access to the Internet
- Inbound VPN authentication where remote users must enter a username and password to get to the corporate network over the Internet
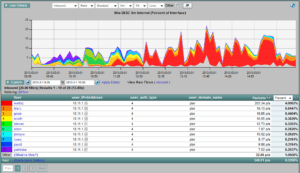
All of the above strategies can be used to export details about the username via NetFlow or IPFIX to a flow collector. Since all traffic is tied to a username, we can then do a better job of application identification. The report below ties IP addresses to authenticated usernames.
Introducing DPI to Identify Applications
All Cisco routers and nearly all major firewalls export either NetFlow or IPFIX. They also perform Deep Packet Inspection (DPI) to identify layer 7 applications such as Facebook, BitTorrent, Skype, Salesforce, etc. When reporting on flow data, applications such as Skype can be clicked on and the usernames involved with the Skype application are listed. NetFlow and IPFIX allow organizations to better identify and manage software and hardware in their environments. By knowing who authenticated the device as well as the applications it is running, we can determine if the device needs to be on the corporate network and who is responsible for it.
Download our whitepaper: Flow based Approaches in Network Management to learn more.