We’ve all come across spoofed emails at some point, and they are a real threat to the security and safety of our organizations and its employees. In this article, I’d like to explore what email spoofing is, how you can detect rogue emails on your network, and how you can take steps to safeguard your domain against spoofing attempts.
What is email spoofing?
“To spoof” literally means “to deceive.” Likewise, a spoofing email’s goal is to deceive the recipient. In most cases, bad actors craft these emails to look like a valid email from a familiar organization. Lifewire has a good article that shows some examples of what phishing and spoofed emails can look like.
There are many reasons for email spoofing. The most common, though, is that the spoofer wants access to passwords and/or login names for your accounts. If you click on a link in a spoofed email, you could become infected with a key logger that will gather password and login data, or the hyperlinked website may prompt you for credentials immediately. As a result, they will gain access to your accounts.
A spoofed email will have altered properties, which disguise who the real sender is. Such properties may include:
- FROM name/address
- RETURN-PATH address
- SOURCE IP address
- X-ORIGIN address
- REPLY-TO name/address
It’s possible to change many of these properties in basic programs like Microsoft Outlook, Gmail, Mozilla Thunderbird, etc. With that in mind, it is important to carefully scrutinize any email that you receive, because it may not be from whom you think.
How can organizations and governments help end spoofed emails?
Last month, Elaine C. Duke, the acting secretary over the United States Department of Homeland Security (DHS), released Binding Operational Directive (BOD-18-01) to improve operational security for federal agencies. This move comes after many congressional leaders urged action by the DHS (as reported by The Hill.com).
“Sen. Ron Wyden (D-Ore.) made the request in a letter to a top official at the National Protection and Programs Directorate (NPPD), the DHS office in charge of securing cyber and physical infrastructure.” In his letter, Senator Wyden writes “to ask [Jeanette Manfra] to take immediate steps to ensure that hackers cannot send emails that impersonate federal agencies.”
The directive requires agencies to take immediate action and submit their plan to implement Domain-based Message Authentication, Reporting and Conformance (DMARC) for better email authentication. The goal is to drastically reduce email spoofing. According to the directive, “Setting a DMARC policy of ‘reject’ provides the strongest protection against spoofed email, ensuring that unauthenticated messages are rejected at the mail server, even before delivery. Additionally, reports provide a mechanism for an agency to become aware of the source an apparent forgery, information that they would not normally receive otherwise.”
This video below provides a very good overview of what DMARC is and how you can use it to help prevent unauthorized emails from domains that implement the technology. In addition, there are more resources available at https://dmarc.org/resources/.
How can organizations detect email coming from internal systems?
Even with systems in place like DMARC, spoofed email can still reach your inbox. The problem is that they can come from within the organization. This happens when policies allow email traffic to come from internal machines that send from the same public IP as those defined in SPF. Furthermore, depending on your DMARC policy, this may be allowed even without appropriate DKIM records in place.
With this in mind, organizations need to monitor where email traffic is coming from. Email traffic coming from client machines, rather than your internal server, is an issue worth investigating.
Using NetFlow, IPFIX, or other metadata from your existing infrastructure, you can see where you have rogue SMTP traffic. By proactively monitoring your email communications, you can quickly identify any internal email traffic that shouldn’t leave in your name.
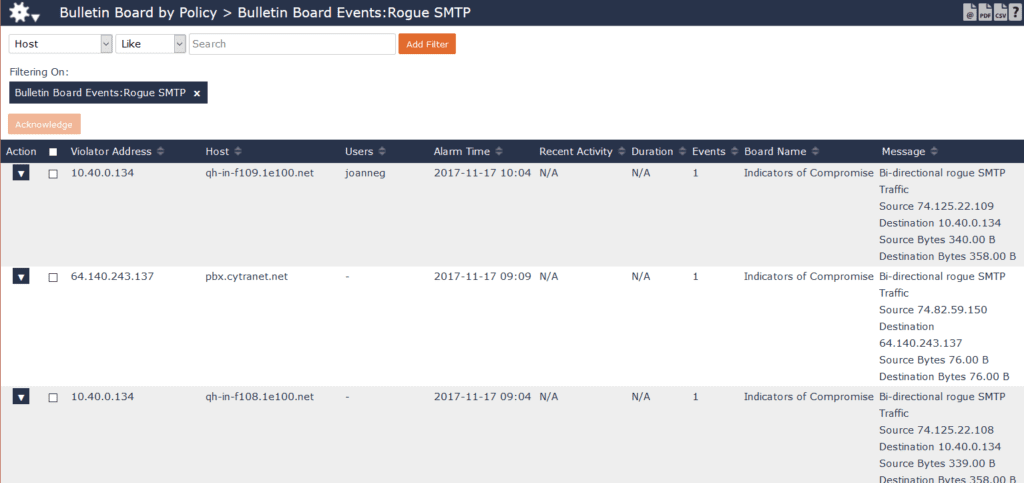
As more organizations implement DMARC, we near the end of the high volume of spoofed email that clogs our inboxes. To see where you have rogue internal email communications on your network, download Scrutinizer Free Edition today.

