The Domain Name System (DNS) is used to resolve human-readable hostnames like www.plixer.com into machine-readable IP addresses like 67.225.210.22. DNS also provides other information about domain names, such as mail services (as mx records) and can be used to provide domain ownership validation for various services (e.g. Google Apps). While this is an important, if not the most important, part of the Internet, it can be used to propagate malicious behavior. A colleague of mine wrote an article on DNS Exfiltration over DNS earlier this year. Today, I would like cover this topic further by showing you how to detect DNS data breaches using DNS and NetFlow.
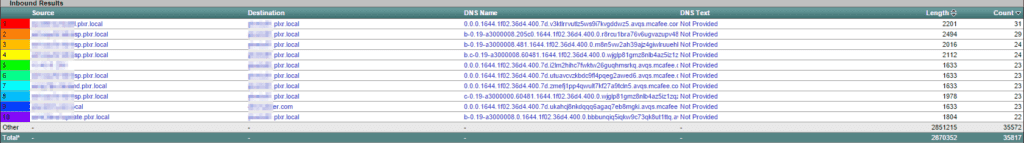
FQDN
Security companies like McAfee and Dell Security (formerly SonicWALL) want their antivirus software to send messages back to the company to improve their products and learn more about their customers. To circumvent the firewall and other security measures, these companies hide their messages in long, cryptic fully qualified domain name (FQDN) requests. Since the internal DNS server can’t resolve the request, it forwards the request to the authoritative DNS server for the second-level domain (e.g. mcafee.com, sonicwall.com, etc.). When this happens, the DNS server, ideally, sends back an NXDOMAIN message; this lets the requester know that the domain doesn’t exist. The owner of the domain to which the request was already sent, however, has the details in the FQDN, be they legitimate or illegal.
DNS TXT
Another way that vendors can pass information through the firewall is via DNS TXT messages. A host on the internal network sends a DNS TXT message that makes it all the way back to the authoritative DNS. As with FQDN, the message is logged for future use and the contents could contain anything kept on the sender’s computer, including confidential data and passwords from a keystroke logger. Furthermore, DNS TXT allows the server on the Internet to send the details back to the host on the inside of your network. Since this type of DNS traffic is transparent to many firewalls, many malware variants take advantage of it. In the case of command and control servers, a response from DNS TXT could indicate new IP addresses/domains that the malware should connect to when making its next phone-home.
Detecting DNS Data Breaches
So now that you know the types of breaches that can be done through DNS, how do you actually detect them? Using advanced flow algorithms and monitoring your DNS traffic with FlowPro Defender, you’ll be provided with a clear indication concerning the activity on your network. For example, if you see even a single DNS TXT transmission, you can be almost certain that something malicious is happening on your network (assuming none of your own applications are using DNS TXT; Google Apps, for example, used DNS TXT for domain verification. Other applications may do this, too). Additionally, strange and long FQDN strings are also a good indicator of malicious behavior. Remember, though, some services like McAfee and Dell SonicWALL use these tactics to retrieve valid/non-illegal data from its customers, so you may want to whitelist the applications that you use before worrying yourself about these activities.
To learn more about DNS and how it can be used to detect data breaches, read our Monitoring DNS Traffic blog.