I’d like to take the time to go through the steps on how a rogue DHCP server works. The more you know about man-in-the-middle attacks, the better you will be at uncovering the infections. Scott wrote a blog a few weeks ago that went into some more detail about detecting a rogue DHCP server and symptoms that you may be infected. I want to hit on how that activity works.
The Scenario:
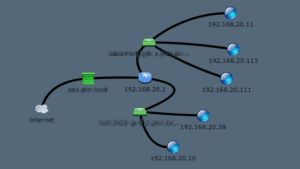
In this scenario, I want to show you how a rogue DHCP server on your network will interrupt the normal DHCP server, and offer a new gateway and IP address to the requesting PC. The image above is of my test lab network. My IP is 192.168.20.113 and our legal DHCP server, 192.168.20.1, uses a range of 192.168.20.1 through 192.168.20.130. When a device requires a new IP address there are four parts to the conversation; DHCP discover, DHCP offer, DHCP request, and DHCP acknowledge.
For today, I will be one of those employees that does not check the link I’m about to click on, while surfing the web on my lunch break. After I click on the wrong link and pull down some malicious malware, the hacker that placed that malware will soon be able to see all the traffic to or from my device on the network. This gives the hacker a way into your private documents, violating privacy and security policies that are put in place to keep that information safe.
How the Rogue DHCP Server Gains Access:
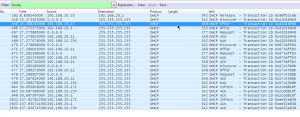
This rogue server is going to sit and wait for a PC to release there IP and put in a request for a new one from the legal DHCP server. The malware sitting on 192.168.20.11 sees the DHCP discover flag and is first to respond with a DHCP offer. The PC that made the request receives the new IP (192.168.20.171) from the rogue DHCP server and sends back the DHCP request with its MAC address to the rogue server. The rogue server then sends the DHCP acknowledge; this makes the rogue server the default gateway for the PC. The rogue DHCP server can now see any packet to or from that PC, and start looking for passwords, confidential documents, or even a way to spread other malware laterally. The two images below are of the PC’s IP and gateway before the release, and after receiving a new IP from the rogue DHCP server.
BEFORE:
AFTER:
Detecting a Rogue DHCP Server:
One of the benefits of collecting NetFlow and IPFIX data from all of your network devices, is that you will have the story of every conversation that traverses your network; helping you find the infections, to limit the effect of man-in-the-middle attacks and other malware. Using the same filters that Scott was describing, we can see the conversation from the rogue DHCP server reaching out to the PC.