In an effort to protect national interests, many nations design and build warfare weapons to protect their assets and possible future plans. As part of this effort, they also need to make sure that they protect the blue prints of the economic plans, destructive weapons, discussions, etc. to ensure they don’t end up in the wrong hands. This has proven to be difficult especially in the case of the cyber weapons produced by the NSA.
The specialists at ANT, which presumably stands for Advanced or Access Network Technology, could be described as master carpenters for the NSA’s department for Tailored Access Operations (TAO). In cases where TAO’s usual hacking and data-skimming methods don’t suffice, ANT workers step in with their special tools, penetrating networking equipment, monitoring mobile phones and computers and diverting or even modifying data. Such “implants,” as they are referred to in NSA parlance, have played a considerable role in the intelligence agency’s ability to establish a global covert network that operates alongside the Internet. source
At the same time we are trying to protect ourselves from the malware like the above, we also have the vendors whom we are supposed to be able to trust, that we have to be concerned about. Companies such as Microsoft, Google, and Facebook and most other large software companies are forcing us to agree to their end user license agreements (EULA) before letting us use their software. The EULA often lays out that the vendor can take information from our computers, TVs, hand held devices and IoT which can include contacts, calendars, key strokes, voice recordings, phone call details, other software package information, GPS location, etc. For some, this is horrifying news. What’s worse is that there seems to be no laws protecting the consumer from these vendors. Many of us are unaware of this big data heist because most people don’t read the EULA. Maybe it’s time we start but, would it stop us from agreeing to the terms?
Microsoft Windows 10 takes information related to contacts, the calendar, text and touch input (I.e. a key stroke logger ?), location information and more. Depending on the version installed, Plantronics constantly uploads to their cloud storage, information pertaining to the username, the computer host name, IP address, call accepted events, call ended events, call duration, etc. It is all listed on the Plantronics web site. Source
After considering the thefts caused by the miss use of spyware produced by the NSA and the wide spread practice of vendors we trust taking our information, one could argue that the taking of corporate data without our awareness has reached a pivot point. It is entirely possible that the volume of data taken by friendly organizations has outpaced the combined thefts by miscreants.
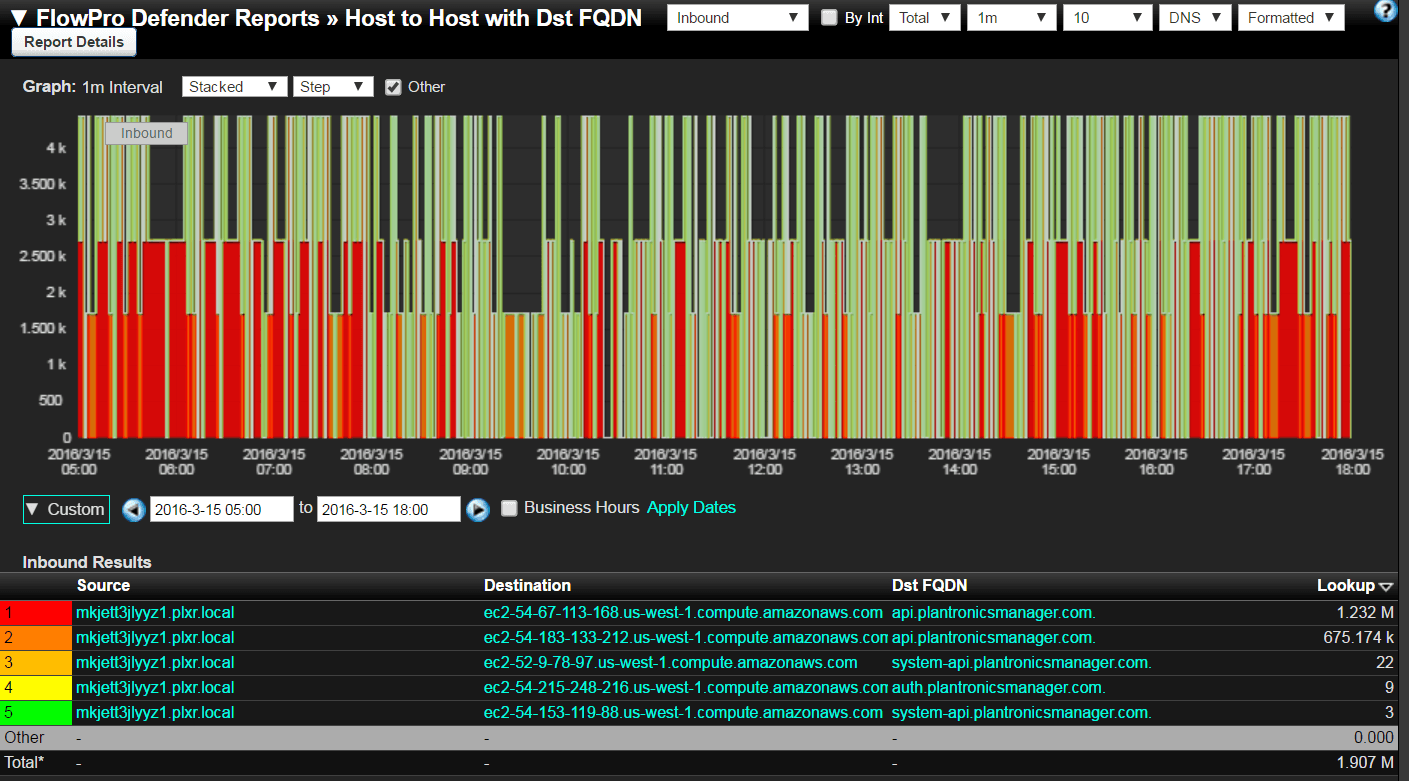
One of the best ways to get a handle on this big data heist in your organization is to implement Network Traffic Analytics (NTA). By monitoring NetFlow and IPFIX created by business applications we can uncover these devious behaviors. A good Network Traffic Analytics solution will correlate flows with meta data such as that from the DNS to provide more context (FQDN or Fully Qualified Domain Name) behind the traffic pattern as shown below after monitoring Plantronics headset software.
To learn more about the above, download our white paper “How Companies You Trust are Stealing from You”.

