Ask a Question, Get an Answer: Meet the New AI Assistant in Plixer One 19.7
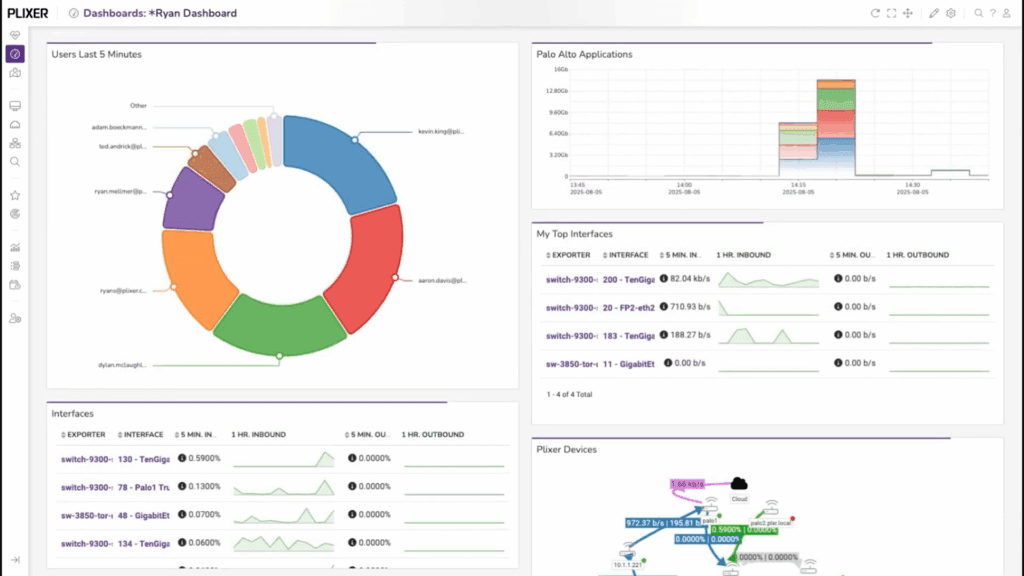
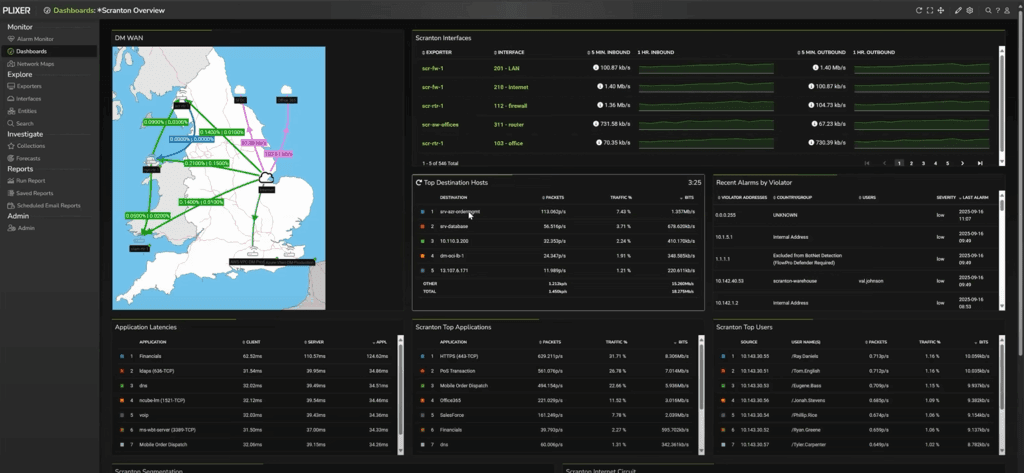
The 19.7 release of Plixer One introduces the Plixer AI Assistant, a new way to interact with your network and security data. Now in the Plixer One UI, you can ask questions in plain language, like “Show me top talkers for the last 24 hours,” or “Is there any Telnet traffic ...
Continue Reading