Our malware detection team plays particularly close attention to DNS traffic because a lot of serious exfiltration occurs as the result of DNS abuse. Since most traffic to the DNS can’t be blocked without potentially crippling Internet activity, we watch for behaviors that are outside the pattern of normal activities.
Many bad actors know this and leverage the DNS protocol to exfiltrate sensitive information out of the company. DNS can also be used by Botnets to communicate with Command and Control servers. For this reason, not only do we have to check the reputation of the fully qualified domains (FQDN) being visited by our end users but, we also have to watch for excessive DNS requests, NXDomains, FQDNs with weird patterns and a host of other anomalies.
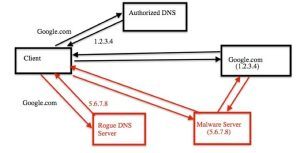
Recently there was an update made to the DNS Unlocker malware which is used to change the DNS server settings used by clients. This malware is particularly dangerous because once a client starts using the rogue DNS, it can redirect client Internet connections through a server containing malware and thereby infect the client with even more garbage.
Explained another way: if a device is infected with DNS Unlocker Malware and browsing the web, it may be directed to a malware serving site, which in turn could inject exploits into the session, change the ads that are being served, or may block the infected device from certain sites. In some cases, Anti-virus may receive a DNS failure when attempting to “call home” to download the latest anti-virus data. Essentially, the rogue DNS site can send the client device to where ever the bad actors want (below in red) and not where the end user wants to go.
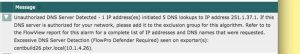
In order to combat the DNS Unlocker Malware, we released Flow Pro Defender16.7 which identifies all IP addresses that are acting as DNS servers for your workstations. By placing the authorized DNS servers in the exclusion group for the DNS Server Detection algorithm, an alarm will be generated whenever an unauthorized DNS Server is detected. Below is the information displayed in Scrutinizer’s Alarm tab.
Running this algorithm 7×24 is very important especially with the latest update to DNS Unlocker. Read this paragraph from the Crouching Tiger, Hidden DNS article:
“Here is the kicker: The DNS Unlocker PUA will set its victims’ static DNS configurations in such a way that the TCP/IPv4 Control Panel will display that you are obtaining your DNS automatically. In fact, the command ipconfig /all from the command line will also indicate you are using DHCP, but you will see the statically set DNS addresses.”
If you suspect that you may have machines infected with the DNS Unlocker Malware, reach out to our team.