Cyber threats, hackers, Botnets, malware, phishing, spam! You have most likely heard all of these buzzwords in the media or possibly read about some of them in our blogs. They are all different sides of the same coin and being able to ascertain the possible threats within your network is becoming a crucial part of your daily routine. By using DNS sinkholes and flow data, you can get more information about what is going on.
So what are DNS sinkholes? This is a question I receive quite often up in support and it has quickly become one of my favorite ways to flag a possible threat quickly. For you geology fans, this might not be the blog for you.
A DNS sinkhole, also known as black hole DNS or IP sinkhole, works by passing out spoofed information to prevent or control traffic designated for a certain domain or IP. For example, a user is looking up www.example.com which is normally 127.0.0.1; the sinkhole receives this request and instead redirects it to 127.1.1.1, which denies the client a connection to the target host.
The technique of sinkholing has been around for a while and has been used to stop malicious activities such as the Conficker, GameOver Zeus and Cryptolocker Botnets. When a user’s system is infected, it will attempt to reach out to its command and control server. If this command and control has been sinkholed, the system will not be able to pull down the payload. This was a major blow against the Botnets of old and it became an easy red flag to look for when dealing with malware.
But if my users are getting redirected and aren’t actually reaching these bad domains, why worry? Let’s put on that blackhat for a second and look at it from the other point of view. If you want to get your malware out and your payloads in place, would you host everything you have on one server with one IP or domain name, or would you spread out the load so that if one branch dies, the tree continues to grow?
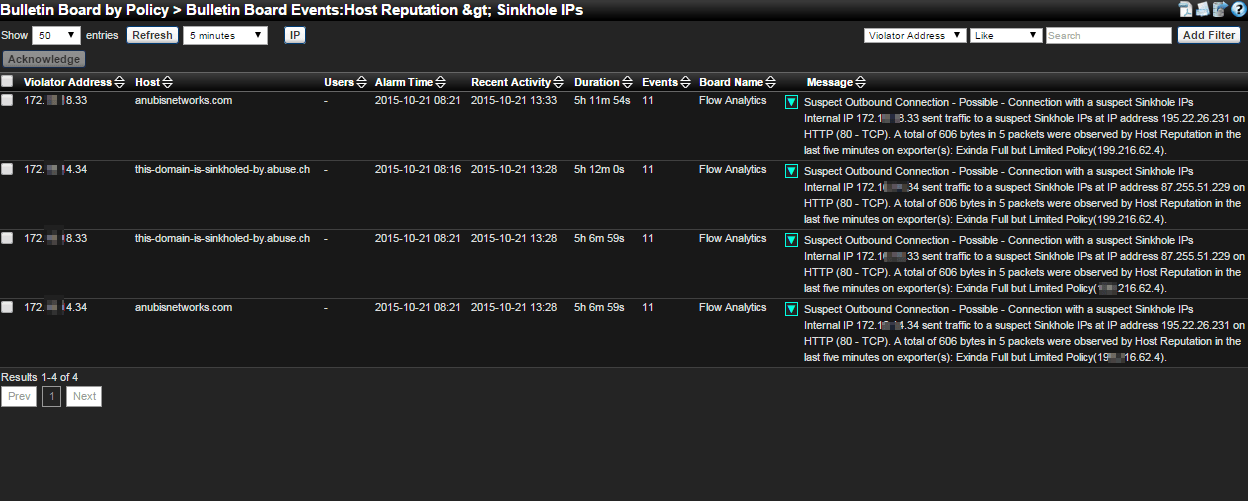
By using NetFlow exports, a network admin can see the broken branch and then start searching for other signs that a compromise has occurred.
These alarms will let them know where the problem occurred, when it occurred, who was causing it and what they were attempting to reach out to. This is all extremely valuable information when dealing with a possible breach. Was this a one-time incident? Or is it being caused by a piece of malicious software sitting on the network and constantly streaming out?
With the right flow collector you will now be able to answer these questions and put your mind to ease. To get started tracking down cyber threats using flow data, check out our free 14-day trial of Scrutinizer.