To understand DNS poisoning, think of a road trip gone wrong.
I don’t know about you, but I refuse to pay $90 to update my GPS map, even though this gets me into sticky situations sometimes. Once, I was trying to get to Portsmouth, for example, and the GPS told me to take a certain exit. But what the GPS didn’t realize, due to its outdated information, was that the exit was wrong. I ended up infuriated, driving much farther than Portsmouth.
Something similar can actually happen on your network. You’re trying to access a certain website, but your ISP’s DNS cache sends you somewhere else entirely—even to a malicious site.
A quick rundown of DNS
We as humans find it easier to remember words than numbers, but computers prefer numbers. So when you type a domain into your browser’s address bar, some sort of translation needs to happen. If you type in “google.com,” your computer will send this information to a Domain Name System (DNS) server. The DNS server searches and, hopefully, responds with an IP address (or several) that your computer can now read in order to access “google.com.”
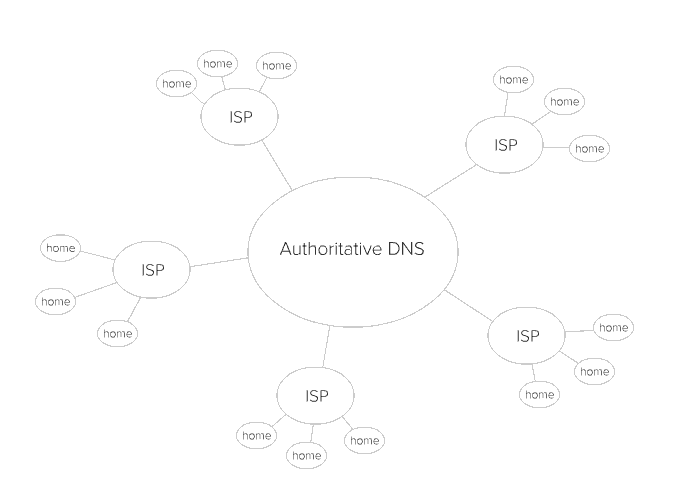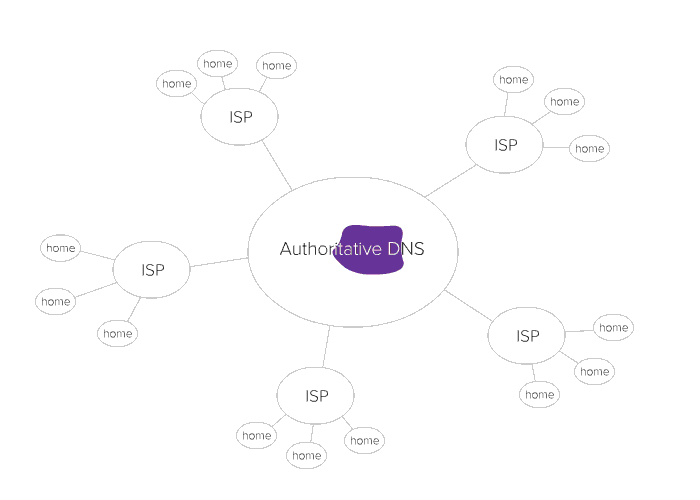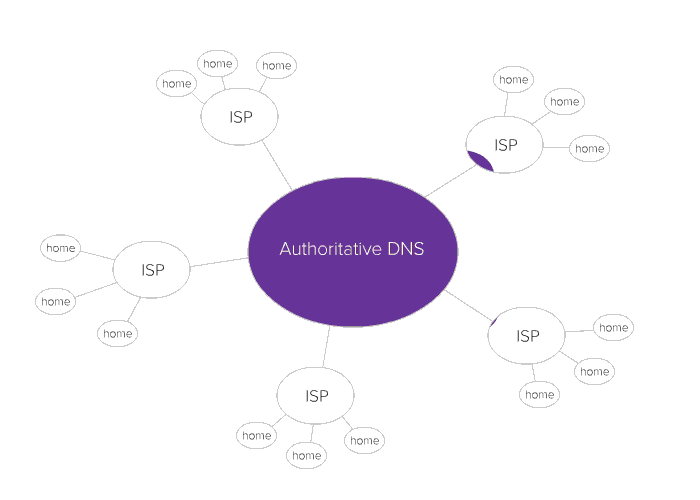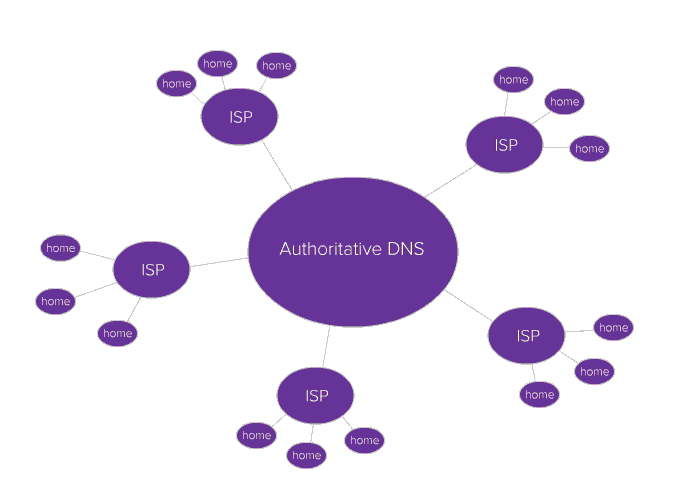
Repeating this process every single time you go to a webpage is inefficient, so there are a couple of ways this is sped up. First, there are multiple DNS servers for your computer to contact. Your router is essentially a DNS server, and your ISP runs its own servers, as well. There are also authoritative servers, which have been configured by an original source.
Second, your routers and the ISP DNS servers will cache information—basically, it remembers the search results. The next time you try to access the same website, the DNS server can respond without performing the search again. Your router caches information from your ISP servers, which in turn cache information from other ISP servers. Keep this in mind!
What is DNS poisoning?
As you can see, DNS servers play a key part in our everyday internet usage. But they have vulnerabilities that hackers can exploit in order to take over DNS servers. When the hacker has control of the DNS server, they can change the cache information; this is DNS poisoning, and there are major implications. The hacker could control where you go when you try to access YouTube, for example, even sending you to a page that immediately runs a script that downloads malware onto your machine. So instead of the cute cat videos you wanted, you’ve got a major malware infection.
Now remember that DNS servers access the caches of other DNS servers. This is how DNS poisoning spreads, and potentially on a huge scale.
DNS poisoning in action
The largest instance of DNS poisoning involved the Great Firewall of China in 2010. The Firewall works partially on the DNS level, redirecting blocked sites like Twitter, Facebook, and YouTube to Chinese servers. In a way, this is an example of lawful DNS poisoning.
But in 2010, an ISP outside of China accidentally made its DNS servers fetch incorrect information from Chinese DNS servers and then cached the information. Anyone using those DNS servers were suddenly unable to access Twitter, Facebook, and YouTube. The DNS poisoning spread globally; even DNS servers in the US were affected.
Mitigation
DNS poisoning is tricky; right now, there isn’t a reliable way to determine whether DNS responses have been tampered with. But a solution is on the horizon: Domain Name System Security Extensions (DNSSEC). In essence, DNSSEC will incorporate verification where there isn’t any currently. Organizations will be able to sign their DNS records using public-key cryptography. This means that your computer will be able to tell whether a DNS record is trustworthy.
In the meantime, don’t expect to be able to stay 100% free of infection. You should always have visibility into your network so that you can proactively watch for signs of malware.