The tactics used to infiltrate a company with the goal of deploying malware and stealing data are becoming more sophisticated. With these changes the methods used to exfiltrate the data are also evolving. What is your company doing to watch for it?
If you have a system that keeps antivirus up to date, so what. Antivirus “is dead,” says Brian Dye, Symantec’s senior vice president for information security. Most of today’s infections are spread by sending infected emails to targeted individuals. Sometimes they even use reputable forums such as Linkedin to reach professionals that trust the source of the email.
Lesson 1: What do you have to monitor for internal (I.e. non Internet bound) scanning?
In some cases like ransomware, the attacks wait until a certain amount of computers are showing signs of infection before they receive instructions from the command and control (C&C) center to execute, hold the computer hostage until money is transferred to a pay pal account. Or the machine could be hosting a bot that will perform dirty deeds such as participate in a DDoS attack, download additional malware or scan directory services for other computers the malware can reach out to. Other times malware will use classic network enumeration tools for scanning. The scanning is done in an effort to spread the infection laterally within the organization. But, how do they get their instructions while on your network? Answer: They beacon.
Lesson 2: What do you have that is monitoring outbound connections that your firewall won’t check?
Sure your next generation firewall will do a decent job at stopping Internet sourced incoming connections but, it generally lets internally sourced outbound connections pass right on by. A PC infected with malware that beacons will send out a message every so often (e.g. 10 minutes) to see if the marching orders have been posted yet. Since the person responsible for the infected PC already authenticated it onto the network, the malware takes advantage of that and sends out low and slow beacons or messages back to the C&C server on the Internet. The messages effectively state “I made it inside, what do you want me to do?”.
Lesson 3: Are you comparing flows to an IP Host Reputation list?
Many C&C servers have already been identified. These lists of C&C servers and other bad hosts are available as a subscription service called host reputation. By constantly comparing the host reputation list to the IP addresses found in flows in and out of the network, a good percentage of infections can be identified.
Lesson 4: Do you have a Data Loss Prevention Tool – are you monitoring for low and slow data leakage?
Are you concerned about low and slow thefts of your companies intellectual property?
According to NetworkWorld, during a time when Coca cola was trying to aquire China Huiyuan Juice, state funded hackers penetrated the Coca Cola network when the deputy president of Coca-Cola’s Pacific Group, Paul Etchells, clicked on a malicious link in a targeted email. The hackers installed a keystroke logger, which captured everything the executive typed. Once in control of the computer, the hackers installed various other programs, gaining access to the company’s corporate network and using Etchells’s machine as a staging point to store and download data taken from other computers.
Point of sale thefts from major retail organizations are particularly damaging because they often hurt the reputation of the retailer by creating fear among its valuable customer base. How does it happen?
The traffic created by some point of sale infections is often times compressed, encrypted and on typical TCP/UDP ports. The uploads to the Internet could be made during regular business hours by a host who again, won’t have any problems making connections right past even the latest next generation firewall. To catch this type of theft, your cyber threat detection system must consider behaviors over time else, false positives could be excessive. Baselines are key: is a host uploading more data to the Internet then they are receiving and does this event happen more than X times per day? Enterprise visibility is key for this to work and flows found in either NetFlow or IPFIX contain what is needed to re-enforce the Data Loss Prevent effort.
Lesson 5: How are you dealing with false positives?
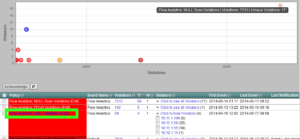
Last month I flew to Washington, DC to give a presentation at the Pentagon. One of the people in the room asked “is your solution going to create false positives?”. My answer was yes, and here is how we are going to deal with them. Obvious exceptions are entered into the logic of each algorithm. Hosts involved with the most suspicious activities are posted high and to the right in the threat heat map shown below.
Above, each host is plotted based on the number of unique algorithms violated as well as the total amount of violations across all algorithms.
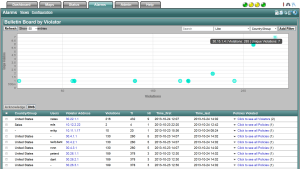
The 2nd way we rise above false positives is through the use of a Threat Index ™. The idea behind the Threat Index: it will rise for an individual host each time it participates in a behavior that is suspicious. Depending on the type of behavior (e.g. scanning the network), the event may increase the index by a higher value than others (e.g. receiving an ICMP redirect). If the Threat Index of a host hits a threshold, a notification can be triggered.
Keep in mind that the Threat Index is a moving value because individual events age out over time. For this reason, an IP address must reach the Threat Index threshold within a configurable window of say 14 days because the same events that increased the value are also aging out and as a result, the index can also be reduced.
If you like this post, please tweet it.