One of the cool things about my position as a Solution Engineer, is that I often work with customers who show me NetFlow configuration options on vendor devices that I didn’t know support NetFlow as a monitoring protocol.
Today I am going to take a look at the NetFlow option offered on the Sophos Cyberoam network security appliance, and how security forensics using NetFlow adds to the overall enterprise threat defense solution.
Sophos Cyberoam is a unified threat management appliance that provides protection against a variety of threats such as unauthorized access, network attacks, malicious code, blended threats, content-based attacks, spyware and phishing. Administrators also gain secure remote access, redundant WAN connectivity and availability, data leakage protection and advanced networking features.
Cyberoam offers advanced network security features to deliver business continuity, faster uptimes, higher network throughput, rapid network growth, meeting the security and regulatory compliance requirements through the following capabilities:
- High Availability with stateful failover
- Dynamic routing
- Multiple VLAN zones to create work-profile based groups across distributed locations
- Virtual host capability, enabling secure hosting of services inside the LAN and DMZ
Because running multiple security processes across multiple locations can be costly and resource-intensive, the centralized, multi-layered approach offered by Sophos Cyberoam is a welcome solution for small businesses as well as the distributed enterprise.
Take advantage of these Security Forensics using NetFlow
NetFlow is a feature that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow a network administrator can determine things such as the source and destination of traffic, class of service, and the causes of congestion (if any).
In today’s networks, using NetFlow for network security and incident response by monitoring communication behaviors is becoming more prevalent. By collecting flows representing all of the conversations traversing the network, you gain visibility into suspect conversations coming in and out of your network as well as moving laterally inside. When the signatures in the IDS/IPS fail to catch malware, NetFlow and IPFIX can recognize enough odd behaviors to protect against cyber attacks. Collecting flows from all of the firewalls, routers, and switches on your network essentially turns each device into a security probe and provides a great additional security layer to your network intrusion prevention solution.
Let’s take a look at the NetFlow configuration
You must be logged on to the Web Admin Console as an administrator with Read-Write permission for relevant features.
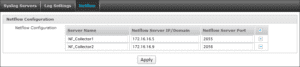
Step 1: Configure NetFlow Collectors
Go to Logs & Reports > Configuration > Netflow and specify Collector Name, IP/Domain and Port, as shown below.
The default port for NetFlow Collector is 2055.
Click Apply to add collectors.
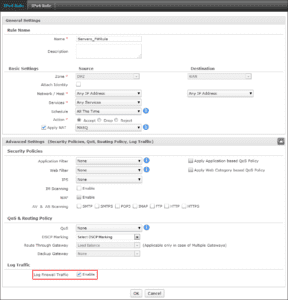
Step 2: Enable Traffic Logging from Firewall Rule
Go to Firewall > Rule > Rule and click the required Rule. Enable Log Firewall Traffic and click OK.
Currently the Cyberoam NetFlow export is version 5 only, and includes field elements that offer all of the traditional TopN (applications, talkers, and conversations) type of reporting. We have seen many of the next generation firewall vendors export unique vendor flow elements in their flow templates. Hopefully future plans include taking full advantage of the NetFlow/IPFIX protocol to export more of the network intrusion prevention data in their flow exports.
Is this the type of network visibility that you would like to take advantage of? Let us show you how you can leverage NetFlow to detect advanced persistent threats and provide a total security solution.