When it comes to networks, organizations are overwhelmed with the amount of data that traverses them. Even with all this data, though, it can be extremely difficult to uncover unwanted or malicious behaviors. Gigamon appliances export unique information that can be used to provide contextual insight into the network for both networking and security professionals alike. In this article, I’d like to explore what a Gigamon and Plixer joint solution would look like to bring better value to the heaps of network data you already have.
One of the many problems that organizations face is determining what the network traffic actually is. With the growth of content delivery networks (CDNs), many web services and applications are relying on platforms like Akamai Technologies, Amazon AWS, or Google Cloud Platform to deliver their products and services. As such, the hostname for these services doesn’t match the actual services that were requested. This makes it difficult to understand how the network is being used.
By leveraging your existing network along with Gigamon’s enhanced metadata exports, you can get the information you’re looking for to determine the actual URL that was requested. Let’s dig a bit deeper into this, so you can see how it works in Scrutinizer.
Pivot from your network to Gigamon
In this example, I will be looking at a report from our lab’s Cisco 3850.
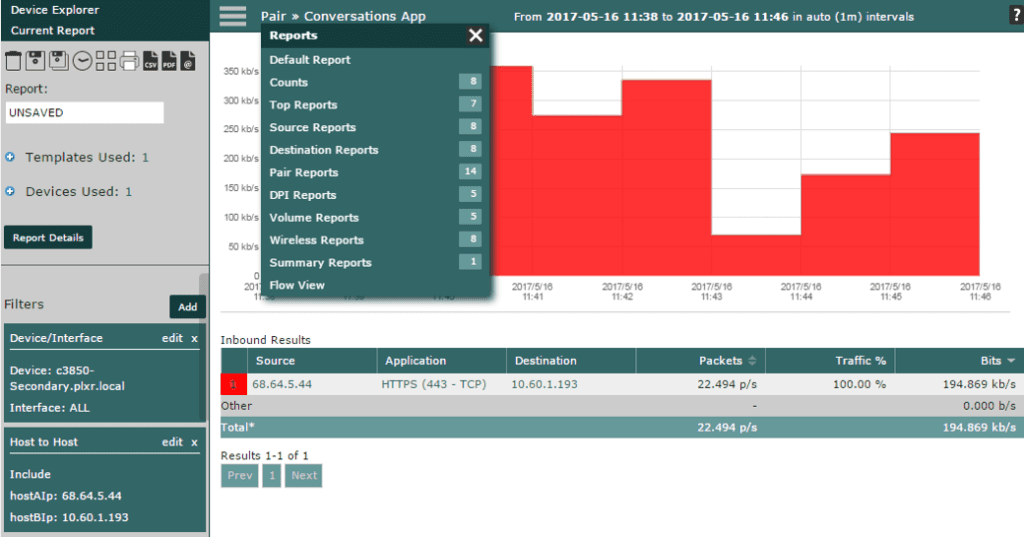
If you take a look at the report above, you can see that I’ve selected the IP address 68.64.5.44 as hostAIp, and I’ve selected 10.60.1.193 as hostBIp within the Host to Host filters. I’ve done this because this is the specific conversation from which I want to gather more information. You can also see that I’ve done this from the Cisco 3850.
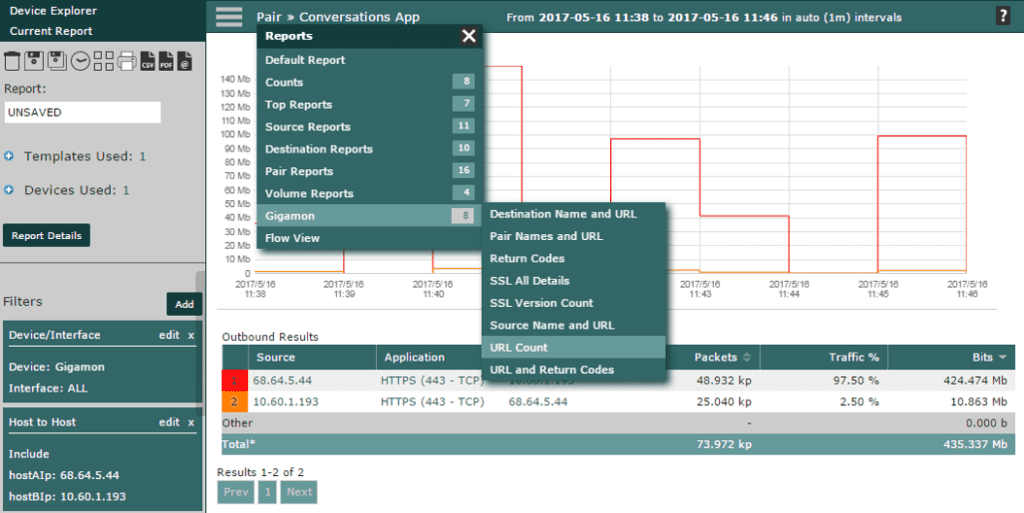
Now that we have our report built, we can change the device/interface to our Gigamon appliance. Notice that the filter has not changed in the report above, only the Device. From this report, we can choose a new report to run that will provide additional information related to the conversation. In this case, we will select the Gigamon report for URL count.
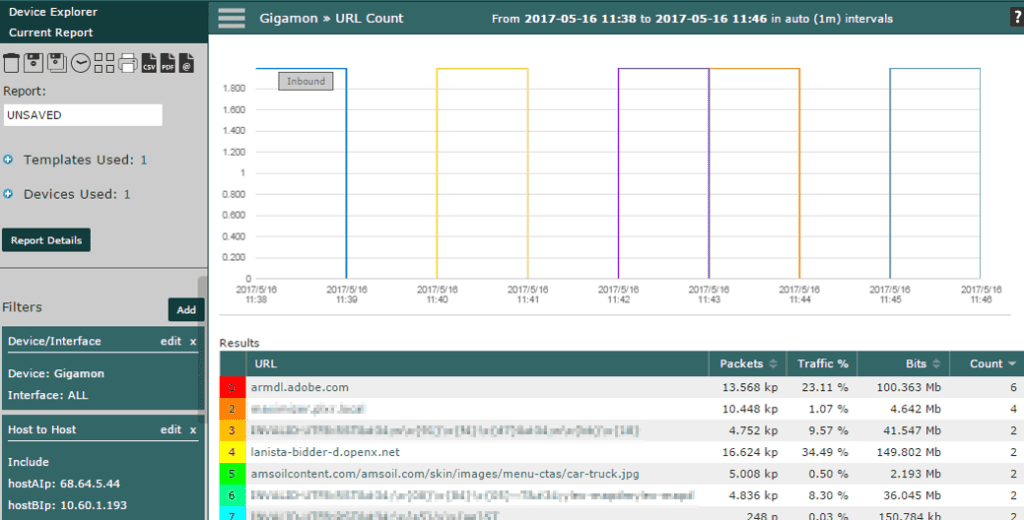
We now have information relating specifically to the conversation. In this specific report, we can see that armdl.adobe.com had the highest number of connections (6). We now have more information that we can use to understand that this specific connection was related to updates from the Adobe servers. Assuming that this specific internal IP is connected to a machine that has Adobe products, it makes complete sense that this took place. Prior to having this information, we would have needed to go to the machine directly to see which services were running and to where they were connecting.
As you could see from the second report screen capture, there are other Gigamon reports that could be leveraged to gain even more context to this connection. If you are using your Gigamon appliance’s real-time SSL decryption functionality, you will gain even more insight by looking into the encrypted traffic on your network, which will provide URL data for sites that connect over HTTPS.
I hope I’ve been able to provide you with the details you need to get the most out of your Gigamon devices. If you want to learn more, visit our Gigamon Partner’s page for more information.