Once in a while, I perform a cleanup of my personal computer that involves removing unnecessary and unwanted applications. It’s a huge headache, because I have to read dozens of names I don’t recognize and somehow distinguish between the crucial processes and the ones I can throw out. I’ve seen many people going through a similar confusion because they find out that their computer is constantly connecting to Akamai Technologies—a name not everyone is familiar with.
Using our Scrutinizer traffic analyzer, I ran a quick traffic report to see where our users’ traffic is heading:
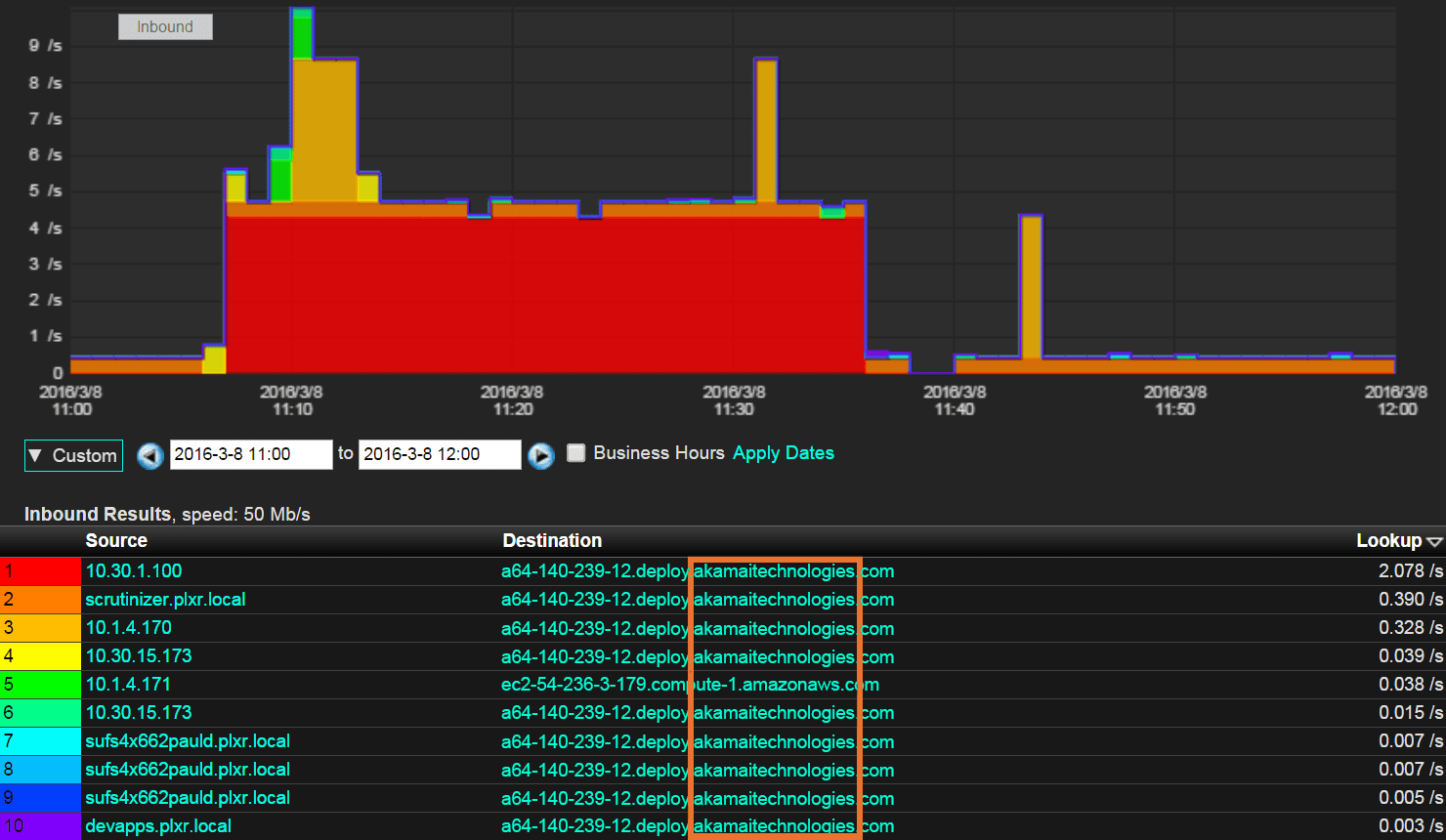
Almost everyone is connecting to Akamai Technologies! It’s no wonder that people instinctively think that Akamai is involved with malware.
Connecting to Akamai isn’t bad
Actually, Akamai is a content delivery network (CDN) and cloud services provider. Other companies use their services to distribute content on servers located all over the world. This means that when you download something from one of those companies, the file will be accessed from a server physically near you, resulting in a faster download speed.
But in the interest of network monitoring, it’s not very helpful for a traffic analyzer to only be able to find users connecting to Akamai, as they are so ubiquitous. We need to be able to find the actual web page where users were sending and receiving traffic.
Luckily, our FlowPro Defender can see beyond the CDN and provide fully qualified domain names (FQDN). Let’s look at the same picture as above, but with the full capabilities of FlowPro Defender:
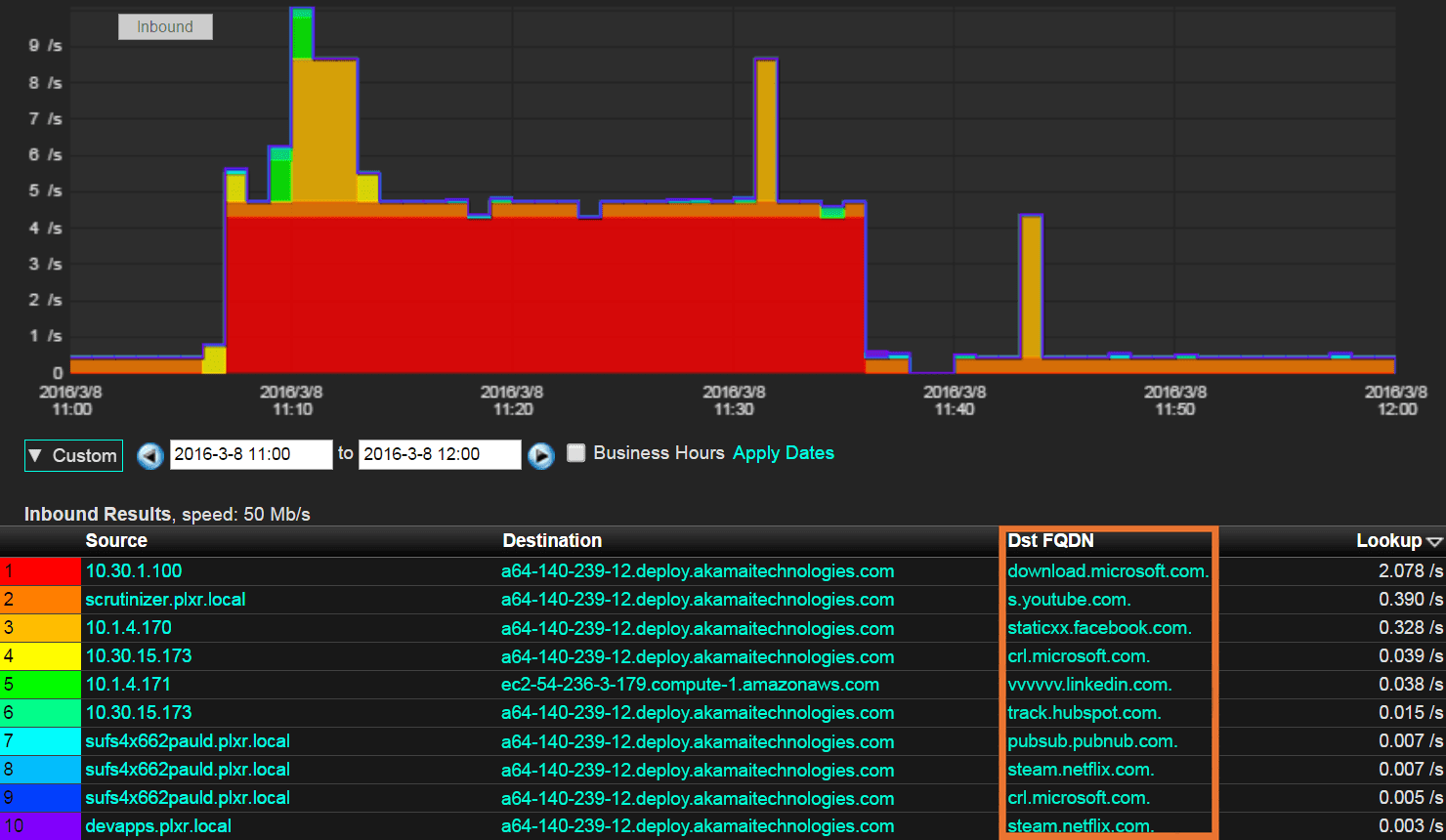
It still shows that users are connecting to Akamai, but we now have a lot of much more useful FQDNs: YouTube, Facebook, Netflix, etc.
But this example is mostly useful for knowing which employees need a slap on the wrist for spending time on websites they shouldn’t be visiting during business hours. How can this help network security teams, too?
Use FQDNs to catch malicious activity
Sometimes, you may see a FQDN that’s just a long string of gibberish, and the local DNS can’t resolve the request. When this happens, the local DNS sends the request back to the authoritative DNS.
This interaction bypasses firewalls.
Some companies like Apple and McAfee can actually use this to gain information from end users with the intent of improving their products; the gibberish-looking FQDN is really encrypted information.
Unfortunately, criminals can use this to their advantage as well. With a system like FlowPro Defender in place, though, you can receive NXDOMAIN messages when this happens—if it happens excessively, that is an indicator of an infection. Our FlowPro Defender triggers the NXDOMAIN message in Scrutinizer so that you can quickly investigate the situation and mitigate it, if necessary.
So, while you can rest assured that connecting to Akamai does not mean your computer is infected with malware, you should still put in place a system that allows you to see beyond Akamai as your traffic destination; hackers could be using a ubiquitous name to hide malicious activity.


