Yesterday, it was disclosed that a currently unknown amount of data has been leaked from websites using the web performance and security company Cloudflare’s services. The issue quickly earned the name “Cloudbleed.”
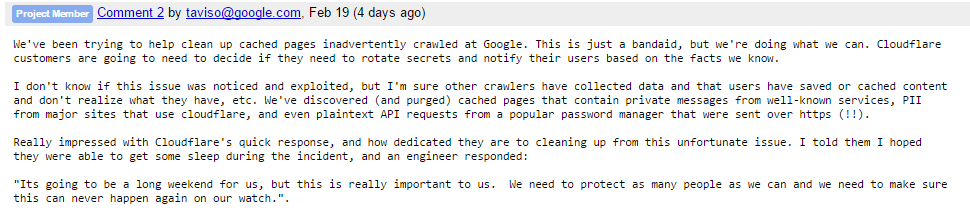
Tavis Ormandy, who works for Google’s Project Zero, first uncovered the leak on February 17 and immediately reported it to Cloudflare. Cloudflare, to their credit, responded with urgency and killed the affected services within an hour. Cloudflare released a public notification on February 23 and published a very detailed, transparent blog about the issue.
The problem is that data has been leaking constantly due to Cloudbleed since September 2016. Cloudflare has a network of 2 million websites, including big clients like Uber, OKCupid, and FitBit. In just a 5-day period in February, the vulnerability leaked across 3,438 unique domains.
According to Tavis’s log of the issue, he found “private messages from major dating sites, full messages from a well-known chat service, online password manager data, frames from adult video sites, [and] hotel bookings… We’re talking full https requests, client IP addresses, full responses, cookies, passwords, keys, data, everything.”
What Caused Cloudbleed?
It seems that a single incorrect character in Cloudflare’s code (a ‘= =’ instead of a ‘>=’) caused the vulnerability. Cloudflare had recently decided to use the new HTML parser, cf-html, but they had trouble when formatting the source code and its former parser, Ragel, to work with its own software. The single-character error caused a buffer overrun vulnerability.
Essentially, the software tried to save user data to a buffer—a temporary place—as it was meant to do. But the buffer became full, so the software started saving data somewhere else, like other websites. To compound the issue, the leaked data was then cached by Google and others. Cloudflare and the Project Zero team, including Tavis, have spent the last week hunting down and cleaning up all the data before hackers could find it.
Thanks to their quick work, the impact currently looks to be minor, though it will take some time to truly understand Cloudbleed’s full implications. Still, both teams deserve a huge kudos; they gave up personal time and spent long hours cleaning up the leak.
How Should I Respond to Cloudbleed?
This is one heck of a good opportunity to change your passwords—all of them. Don’t forget to change your password to your password manager (e.g. LastPass) as well. It’s also a good idea to sign up for 2-factor authentication wherever it’s offered, since hackers won’t be able to use your account even if they have gotten ahold of your password.
If you manage a site and use Cloudflare, you may consider forcing a password reset for all of your users. At the very least, your team should seriously evaluate this security issue.
For more cybersecurity articles, follow @Plixer on Twitter.


