Today, I will be talking about the Cisco Zone-Based Firewall, including their differences and advantages compared to a Cisco ASA. I will also walk through the configuration steps, showing how to turn NetFlow on and start getting these awesome Zone Pair and Class reports!
What is a Zone-Based Firewall?
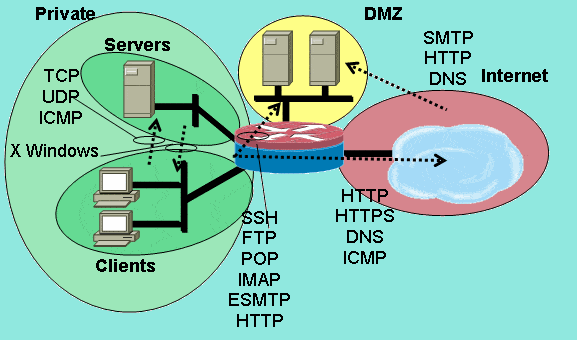
The Cisco Zone-Based Firewall is the successor of Classic IOS firewall or CBAC (Context-Based Access Control). It primarily deals with the security “zones”. We can assign router interfaces to various security zones and control the traffic between them. The firewall dynamically inspects traffic passing through zones. In addition to all the features available in classic IOS firewall, the Zone-Based Firewall supports application inspection and control for: HTTP, POP3, Sun RPC, IM Applications, and P2P File sharing.
Cisco ASA vs IOS Router with Zone-Based Firewall
Have you ever had to decide between a Cisco ASA and a Cisco IOS Router at a smaller branch office? It sounds like it might be an easy choice, but it’s not. Besides the budget, the decision depends heavily upon the engineer’s philosophy. Some prefer to have a single device do both routing and security, but others opt for dedicated security devices.
The ASA denies all traffic by default, while the IOS router starts out by allowing all traffic, even on your untrusted interfaces. You can eliminate this disadvantage, however, by hardening your router.
One of the major things to consider is the complexity of VPN features desired. If you want to leverage more advanced features like DMVPN or GET VPN, an IOS router is your only option. Furthermore, the ASA doesn’t support Policy Base Routing, since the ASA routes traffic through one active default gateway and it can’t classify packets based on source/service like routers do.
The Cisco ASA offers faster performance (especially on VPN tunnels), but that’s partially because it is not performing dynamic routing. Another advantage of the ASA is that it can operate in transparent mode; the firewall essentially acts as a Layer 2 bridge and is not seen as a router hop in the network path. This simplifies deployment, since there are no routing patterns to adjust and no complex NAT configurations to set up.
If you’re looking for an appliance just to inspect traffic, predominantly for a web DMZ or publicly accessible network, the ASA might be your best option. In a highly decentralized internal network where branch offices frequently talking to each other would benefit from something like DMVPN, you will greatly simplify your deployment by using an IOS router with a Zone-Based Firewall.
Cisco Zone-Based Firewall Reporting
In order to get Cisco Zone-Based Firewall reports from the network’s routers, we need to define a flow exporter and option templates. Then we need to attach the flow exporter to a global parameter map.
parameter-map type inspect global
alert on
log dropped-packets enable
log summary flows 256 time-interval 60
max-incomplete low 18000
max-incomplete high 20000
exporter export-to-inside
flow exporter export-to-inside
option inspect-class-table
option inspect-protocol-table
option inspect-ext-event-table
option inspect-zonepair-table
Now that we have the configuration applied, what benefits are available to you with Cisco Zone-Based Firewall NetFlow Support?
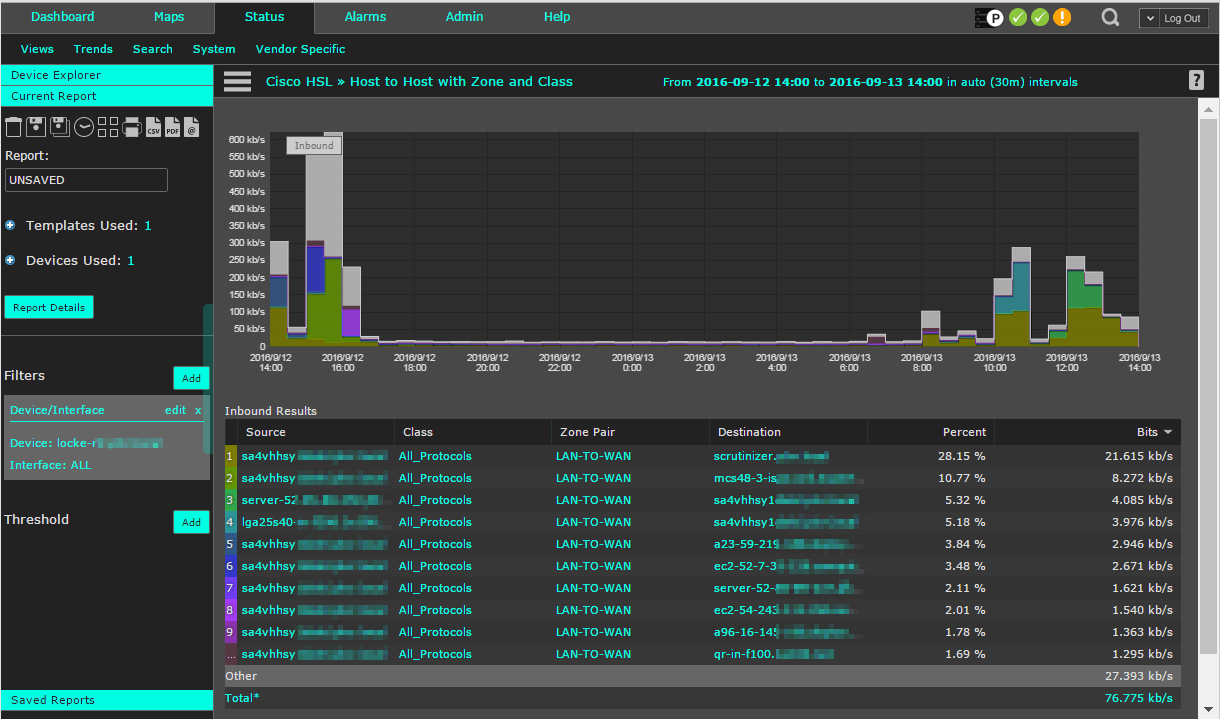
By combining the Cisco NetFlow exports with a powerful advanced flow reporting and analyzing solution, reports such as the one displayed in the screenshot below are just one of the possibilities. This particular Host to Host report provides us with the details on Zone Pair and Class. Pretty hefty, huh?
More on Cisco Zone-Based Firewalls
Check out Austin’s blog on Cisco Zone-Based Firewall Logging Support to see what event types Cisco supports and an example configuration.
If you have any questions on setting up your Cisco NetFlow exports, feel free to reach out to the Plixer Support Team at 207-324-8805 x4.