In this blog, I will be continuing Part 1 of the “What is Flow Analytics™?” Series. In this blog I will be going over what the different algorithms do and how you can use them to better your network traffic analysis.
By default, some of the network behavior analysis algorithms are enabled globally across all NetFlow exporting devices. These algorithms are usually used to show the “top” domains/hosts/conversations..etc across your network. These can be very useful in troubleshooting network slowness or when trying to monitor a threat that can be going on across your network.
Most of the algorithms listed below need to be enabled on a per device basis, since certain algorithms in conjunction with certain devices (such as print servers) can trigger false positives. To get you the most accurate network traffic analysis and threat monitoring you will need to create exclusions for the IP’s triggering false positives.
- Breach Attempts Violation: Looks for many small flows from one source to one destination. This can indicate things such as a brute force password attack. A typical scenario would be a dictionary attack on an SSH server.
- Custom Reports Thresholds: Any saved reports that have an inbound threshold are executed sequentially by this algorithm. Clicking on the name of this algorithm in the Flow Analytics™ Overview gadget, will launch the Custom Filters gadget.
- DDoS Violation: Identifies a Distributed Denial of Service attack such as those that can be launched by a BOTNET.
- DNS Violation: Alerts when a host initiates an excessive number of DNS queries. This can help to identify hosts that may be infected with a mailer worm or other issues that require an inordinate number DNS look-ups.
- FIN Scan: The FIN scan’s “stealth” frames are unusual because they are sent to a device without first going through the normal TCP handshaking.
- ICMP Destination Unreachable: This is a message that comes back from the router to the requesting host stating that it doesn’t have a route to the destination network of the target host.
- ICMP Port Unreachable Algorithm: This is a message that comes back from the destination server stating that it will not open communication on the specified port requested by the host.
- Internet Threats: This algorithm goes out to an Internet site every hour and downloads an updated list of known hosts that end systems on the network should not be communicating with. Typically this is a list of compromised hosts that have a reputation for sending nefarious traffic. This list is updated by several Internet Service Providers.
- Multicast Traffic Violation: Any multicast traffic that exceeds the threshold that isn’t excluded will violate this algorithm.
- Nefarious Activity Violation: Looks for hosts communicating with many hosts with a low number of flows. An example would be a port 80 scan of an entire subnet.
- NULL Scan: The null scan turns off all flags, creating a lack of TCP flags that should never occur.
- Peer to peer: P2P (includes BitTorrent) connections are monitored by this algorithm..
- RST/ACK: RST/ACK packets are connection denials that come back from destinations to the originating hosts. This alarm can be caused by network scanning. Print servers can cause false positives with this algorithm and often need to be excluded.
- SYN scan/flood: SYN packets are sent out in an attempt to make a network connection with a target host. This alarm can be caused by network scanning.
- Unfinished Flows Violation: Executed by the Top Flows Algorithm, helps identify hosts that have a high percentage of unfinished flows. This indicates scanning, Malware or poorly configured applications on a host.
- XMAS Tree scan: The Xmas tree scan sends a TCP frame to a remote device with the URG, PUSH, and FIN flags set. This is called a Xmas tree scan because of the alternating bits turned on and off in the flags byte (00101001), much like the lights of a Christmas tree.
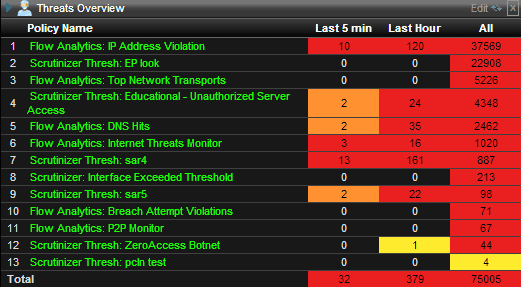
As you can see from the above Flow Analytics™ can cover a lot of different cyber attacks and violations that other network security tools cannot. Also now in our latest version you have the ability from the alarms page to quickly see who is triggering the most alarms and how many times/types of alarms have been triggered. Our network monitoring tool has the ability to send out email alerts to an administrator whenever a violation is triggered which can reduce response time.
With there being so many new cyber security threats coming out each and every day the need for traffic analysis has never been this high. With our network monitoring software you are getting 100% network visibility.
If you have any questions or need any assistance setting up Flow Analytics ™ feel free to let us know.



