Using Cisco Application Visibility and Control (AVC), network administrators can manage network application performance and BYOD traffic by setting up a wireless policy to prioritize, control, and bring visibility to the BYOD applications traversing their network.
There are many challenges IT managers face on a daily basis. As the number of user devices and the business, personal and collaborative applications continue to grow, these challenges only make the job of an IT manager harder.
Today’s networks support a mixed use of guests, employees and vendors. Without classifying and prioritizing applications on the network, employees risk losing productivity and response time to critical applications that they use.
Imagine what goes through the mind of an IT administrator who is responsible for getting a handle on device and application growth and usage on their network:
- Is a guest downloading movies using Bit-Torrent – in other words, stealing valuable airtime away from my mission-critical applications?
- What are my top users and applications?
- Can I prioritize business-class applications and de-prioritize the applications such as Netflix?
- Do I need more Access Points?
So how is Cisco AVC going to help on your wireless network access points?
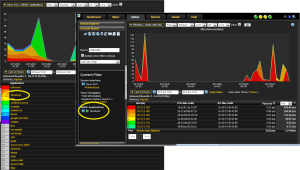
Client traffic coming up stream or down stream is parsed through the NBAR2 packet library. This is a deep packet inspection (dpi) library that includes over 1000 application signatures that look deep into layer 7 to understand what the application is, what it is doing, and how much of your airtime wireless bandwidth it is taking up.
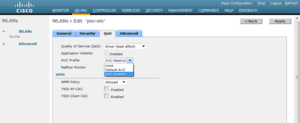
Based on the visibility we get for each flow as we understand it from the client or the server, we can remark those different flows into different quality of service queues.
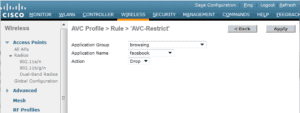
We can then take action (drop, classify, and prioritize) based on how the application flows are marked.
The ability to identify and remark right down to a sub-category level allows the IT administrator to differentiate between users using Google video vs Google mail, Skype Voice vs Video, and place them in different QoS queues. Even when a guest is using encrypted applications, the IT administrator will still be able to identify it, because NBAR2 supports heuristics based classification.
You can see how Cisco AVC provides unprecedented network application control and visibility into the traffic traversing the network. Now you are going to need a NetFlow analyzer that is already offering the leading edge reports that support these new flow exports. We are the first to report on Cisco Wireless NetFlow exports.
What are you doing to control the applications on your network? Do you even know what applications are on your network?