Are you building an incident response system? Does it include tools that allow for attack investigation and recovery? Earlier this year I wrote a three part series on constructing a Cyber Incident Response Plan and outlined two ways Scrutinizer can be an important part of this endeavor. After reading the latest BBC article on how Website-crippling cyber-attacks are to rise in 2016 , I figured that I would talk a bit more on how our Flow Analytic intelligence can assist with attack investigation and recovery.
What is Flow Analytics™?
Built into Scrutinizer is intelligence that uses network behavior analysis to detect abnormalities on your network. By implementing Network Behavior Anomaly Detection (NBAD) intelligence on your network, you can detect and trigger alarms for behaviors such as worms, network scanning, and known compromised internet hosts. It can also alert you if any DoS attacks are happening. By complimenting your NetFlow collection with our FlowPro Defender™ you can also obtain layer-7 analysis of your DNS traffic to immediately alert when malware uses DNS for information exfiltration or command and control.
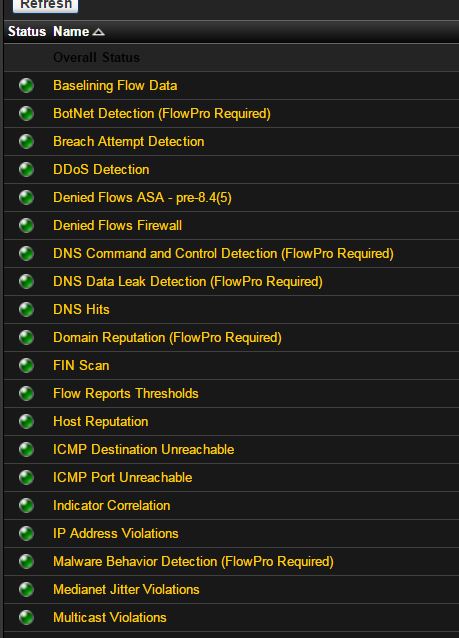
When planning your system you need to make sure that the intelligence behind your NetFlow system can detect advanced cyber threats and will also provide you with the information needed to answer these questions.
- Where did the event take place?
- When did the incident first begin?
- Which specific user was involved?
- Were multiple devices compromised?
So how do you use something like this for attack investigation and recovery?
Lets use a real-world example. We were alerted by Flow Analytics that a Bot Net was detected. Matter of fact, due to detection of various patterns against that host, the alert was escalated to a “high level” security concern by Scrutinizer.
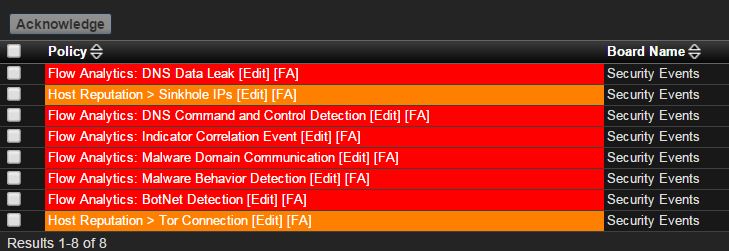
From here we can start to investigate the issue and determine if further action is required. At this point, we click on the Flow Analytics: BotNet Detection link and quickly see all of the detected instances of this behavior. Now, the descriptions for each instance gives quite a bit of detailed information, but we need to dig deeper. On the left hand side of that message we see a small downward facing triangle. When you click on this you are presented with multiple ways to investigate this specific incident. If you click on the link for Default Flow Report you are presented with the exact conversation of the incident that triggered this alert.
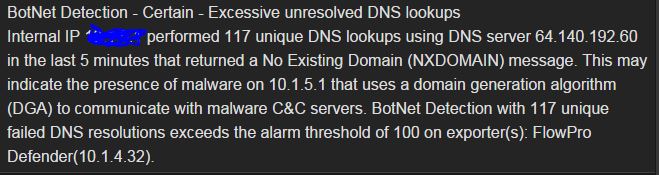
At this point we can start to answer the qualifying questions I outlined earlier. We now know when and where the incident took place. We were also able to identify the offender by IP address and user name.
Why full visibility is so important.
The last question we need to answer is, were other devices compromised? When you click on the alert under the security view of the alarms tab, more than likely, there were multiple violators reported for this incident. Remember, this does not mean you are completely safe. You need to make sure that no one else has communicated with the compromised host. This is why it is so important for you to have historical data. So, again, we click on the small downward facing arrow and scroll down to click on the “Other” option and then select “Search”.
You now have the ability to search for conversations related to the selected host. Even if the host is dormant, you have the resources to find their conversation history via Scrutinizer’s data retention abilities.
In the end it is all about having multiple layers of security and complete visibility into your network traffic. If you would like to learn more about how Scrutinizer can help you stay vigilant and be a valuable asset in your Cyber Incident Response System, give us a call and we will be more than happy to help you.

