How safe is your personal information? Well, several celebrity clients of a New York law firm have discovered that it’s only as safe as the weakest link. These high-profile victims became the most recent targets of the REvil ransomware attack. REvil (also known as Sodinokibi) is a network of cybercriminals who offer RaaS (Ransomware-as-a-Service). After stealing the data, the attackers began leaking the clients’ personal information to pressure the firm into paying the $42 million ransom.
COVID-19 and the ransomware relationship
The global pandemic has caused a record number of remote workers. While companies have rushed to provide remote access to their workforce, some have inadvertently overlooked adequately securing these new resources. As a result, the number of brute force attacks targeting RDP (Remote Desktop Protocol) accounts has increased dramatically, now numbering in the millions per week. RDP is a common attack vector for cybercriminals, who often target poorly configured servers and systems running old, unpatched OS versions. Attack methods on these servers include brute-force and credential stuffing. Recent breaches and credential dumps have exposed many users’ access credentials. Compromised RDP installations are also being sold to cybercriminals. Lastly, there’s the issue of guessable credentials (guest/guest, user/user, admin/admin, etc.) used on external-facing systems.
Can network traffic analysis help prevent the next attack?
With the work-from-home trend likely to continue for the foreseeable future, it’s important to understand how we can leverage network flow data to detect and possibly even prevent a brute-force RDP attack. For example, we’ve seen these patterns from recent ransomware attacks:
- After compromising RDP, attackers leverage credential theft, lateral movement, and data exfiltration
- Several attacks have been short-lived (smash and grab style)
Plixer Scrutinizer can serve an integral layer within an organization’s defense-in-depth security strategy. The latest release leverages machine learning to provide advanced threat detection. Using one of our standard Flow Analytic algorithms, Breach Attempt Violation, security teams can isolate many small flows from one source to one destination. This pattern can indicate a brute-force attack against RDP. Then you can set up an alarm that will automatically notify you when a brute-force attack occurs.
Attackers often scan IP address blocks for hosts that respond and then establish unusual inbound and outbound RDP connections to and from other countries in order to facilitate data exfiltration. Security teams can use Scrutinizer to report on RDP traffic by source and destination countries, identifying potential geographic irregularities.
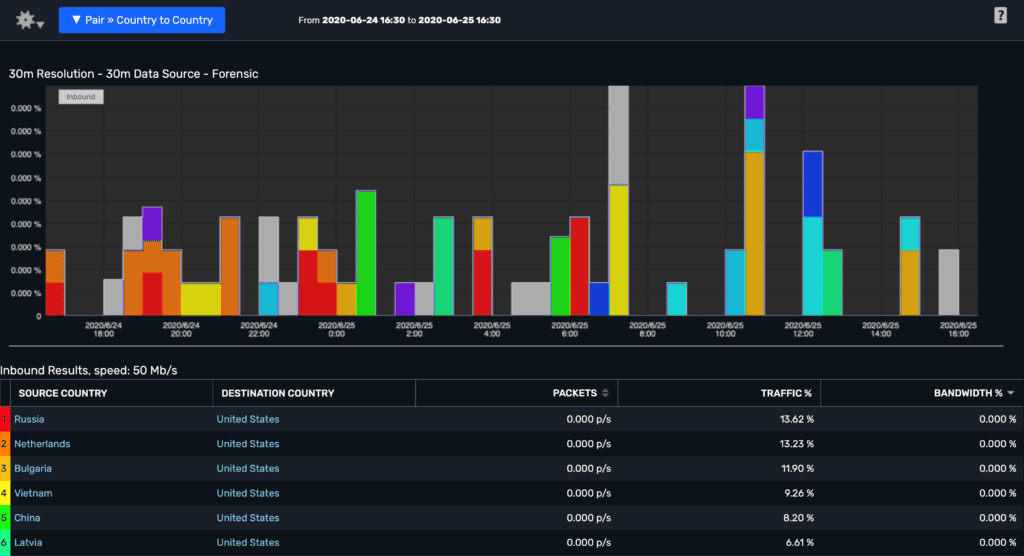
Some attacks have shown a high number of requests for the same file, indicating a possible trial-and-error pattern. We sometimes also see mismatched port-application traffic as part of the attack. Plixer Scrutinizer’s powerful network and security intelligence features can help users pinpoint anomalous traffic and quickly alert the incident response team.
What’s next?
It looks like there’s no end in sight for ransomware attacks, as cybercriminals continue to evolve and invent new ways to infiltrate the IT systems used by remote workers. But Plixer Scrutinizer can help provide the much-needed visibility. Plixer stands out as the market leader in metadata analysis, visualization, and reporting. Download Scrutinizer and test it out on your own network here.



