Security Information Event Management (SIEM) platforms began to gain mainstream attention and adoption around 2008. SIEM promised to simplify and improve security as an aggregator and correlator of logs from disparate systems like IDS/IPS, anti-virus, firewalls, and many other point security products. In concept, this was intended to provide value by reducing the number of false positives, streamlining vast amounts of security log data, elevating real security events to the attention of the security team, and stack-ranking event severity. Over the years, many of these promises have been met, and organizations have have gained better security event detection, but many SIEM problems exist that hold customers back from gaining the full potential of their implementations. In this blog I will discuss what I believe are the top five problems and, more importantly, I will share how integration with NetFlow collectors like Scrutinizer can help organizations overcome these problems.
1. High Configuration, Customization, and Deployment Complexity
The fact that value is derived from SIEM is clear, but organizations should not underestimate the initial effort of getting the SIEM installed, configured, and deployed. Nor should they ignore the effort that goes into ongoing maintenance. I have seen initial implementation efforts range from 3 months to nearly a year and the deployment often includes professional services from the platform manufacturer to get the implementation off the ground.
A consideration often overlooked during initial deployment is which use cases to tackle first, and which data sources to prioritize. This is important because it establishes the scope of correlation rule definitions for the initial implementation. Once the SIEM has been deployed in alignment with the implementation plan, there can also be significant ongoing tuning of the platform to reduce false positives. By integrating NetFlow and metadata collectors like Scrutinizer, you eliminate the efforts of defining network traffic analysis rules and initial tuning, as well as ongoing maintenance.
2. Cybersecurity Skillsets are Hard to Find
When asked to identify their top challenges, CIOs often rank a cybersecurity skills gap highly. One of the big challenges pertaining specifically to SIEM platforms is the complexity of creating query strings. Security analysts must write a query string in order to use their SIEM to answer a specific question.
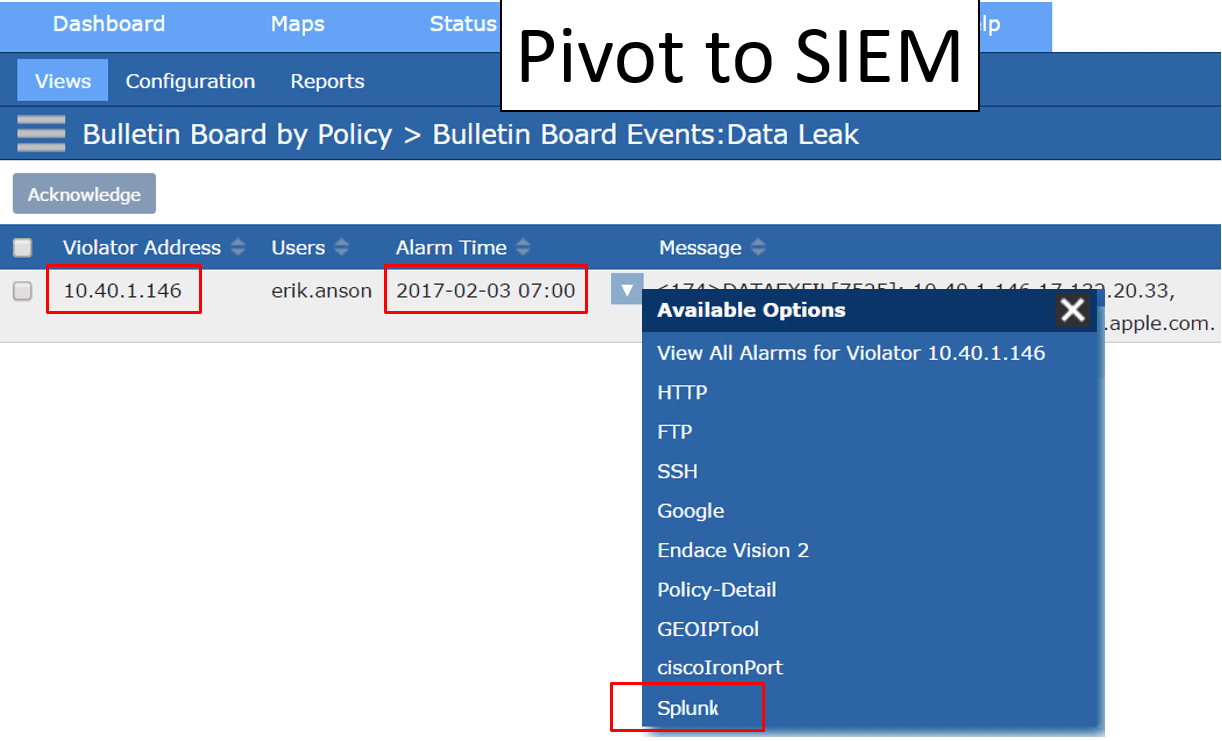
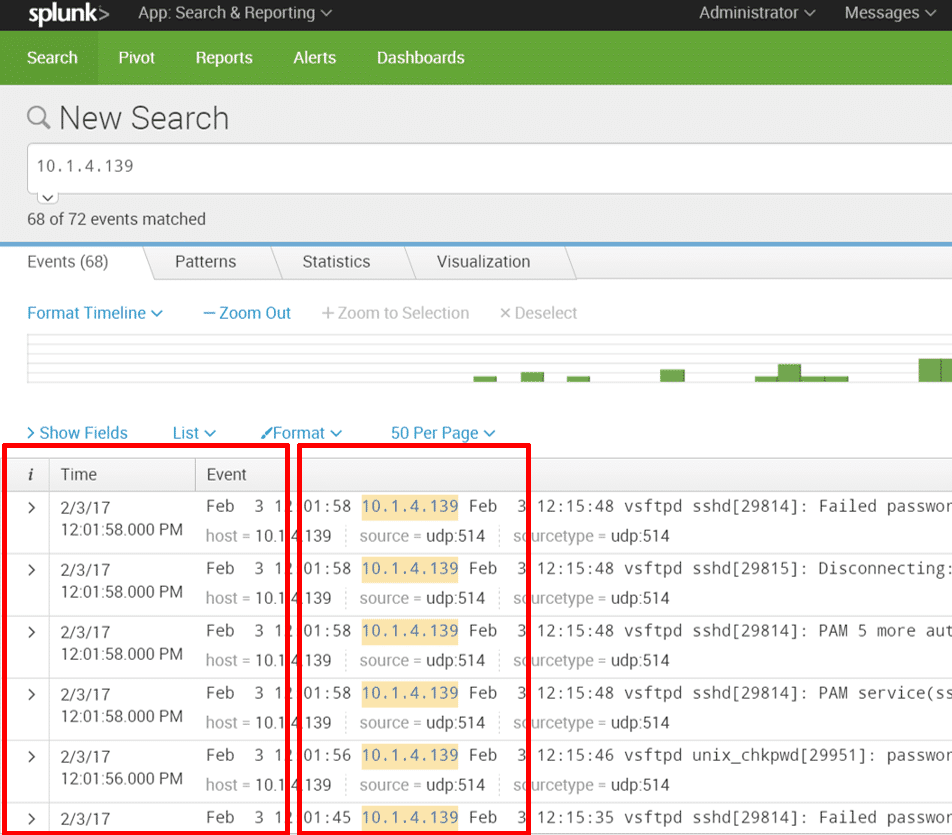
This query string defines the question, which means it also defines whether the answer returned includes the desired data. This is not a trivial task, and requires a very special skillset to accomplish. Integration with Scrutinizer is valuable here—it eliminates the need for query strings when you are looking for data related to network traffic analytics. Instead, you can use Scrutinizer to identify the root cause of an incident, including the offender’s IP address and a timestamp. From there, these data filters are dynamically passed to the SIEM. From Scrutinizer, you can pivot directly into the SIEM and all data relevant to the incident is displayed in real time.
3. SIEMs Lack Data Context
SIEM deployments aggregate syslogs, which are alerts identifying the occurrence of specific events. A single product, such as a firewall, anti-virus system, or intrusion detection platform can each generate tens or hundreds of thousands of logs per day. SIEMs consume syslogs from many different products and correlate them. The idea is that if a log event seen by the firewall can be correlated with a log event seen by IDS, the likelihood goes up of it being a real event rather than a false positive. The more correlation, the stronger the evidence the event is real. Prior to event aggregation and correlation, analysts were required to manually investigate events across disparate data silos. This was impossible given the generation of millions of syslogs. Now with correlations, SIEM does a nice job of being able to detect security risks.
The challenge for security analysts at this point is that detection is really just the starting point. Once an event has been identified, the analyst must quickly shift to incident response. Effective incident response requires contextual forensic data to be able to investigate, remediate, and quickly return to normal. This is where SIEM falls short. Remember, SIEMs aggregate syslogs, which are simply alerts that something happened. When context is missing, the data is not actionable, leaving analysts with the question of “What do I do now?” Context is gained, however, through integration with a NetFlow and metadata collector like Scrutinizer. Scrutinizer has the ability to provide historical context around every conversation that has traversed the network, such as source/destination, username, device info, application, URL/URI, DNS, and much more.
4. Even With Data Aggregation, SIEMs are Still Too Noisy
Trying to keep up with millions of logs is incredibly difficult. When problems arise, starting your investigation in a SIEM is like trying to find a needle in a needle stack. This is another scenario where NetFlow and metadata collection provides tangible and complementary value. Based on the identification of a security event, analysts can use Scrutinizer as their primary dashboard to investigate and determine root cause. Once root cause is established, incident-related data elements like offending IP addresses and timestamps are dynamically passed into the SIEM. This integration eliminates the need to create complex query strings in an effort to extract the right data from the massive SIEM database.
5. Higher Than Expected Cost of Data Storage
The long-term costs of a SIEM often exceed expectations. The upfront cost of the software and hardware is only a small portion of overall expenditure. Many SIEM platforms have additional charges based on data consumption rates. As the number of security products deployed within organizations grows, more and more logs are exported to the SIEM, forcing the business to spend more. It can be very difficult to predict data growth, leading to unpredictable increases in SIEM-related expenses. We have many customers who use Scrutinizer to aggregate, correlate, visualize, and report on flow and metadata. In this manner, they are offloading data collection from the SIEM to a platform that does not incur the same type of incremental cost for data consumption. Not only are they achieving significant savings, but they are also able to more quickly identify root cause and provide more efficient incident response.
Summary
For many organizations, SIEM is a valuable component within their suite of security products, but there are several SIEM problems that exist as well. Integration of SIEM platforms with NetFlow and metadata collectors can help overcome many of the SIEM problems end users experience. Integration enables better data context, improves visualization and reporting, reduces cost, makes security teams more nimble, and provides significantly faster and more accurate incident response for inevitable data breaches.



