When supporting a product, you often hear patterns across the support cases you take.
Today, I wanted to give you a short list of features that appear to be underused, but that I receive the most support cases for. These features allow users to receive automated reports in their inbox, speed up report building, and allow for the fastest troubleshooting in a network environment.
Thresholds and Email Alerts
Scrutinizer can define a value against any of the nearly 5000 data elements it ingests and send an automated email if that value is met or exceeded. Once we save a report, we can set up a threshold by clicking the Filters/Details button and then navigating to the Threshold tab.
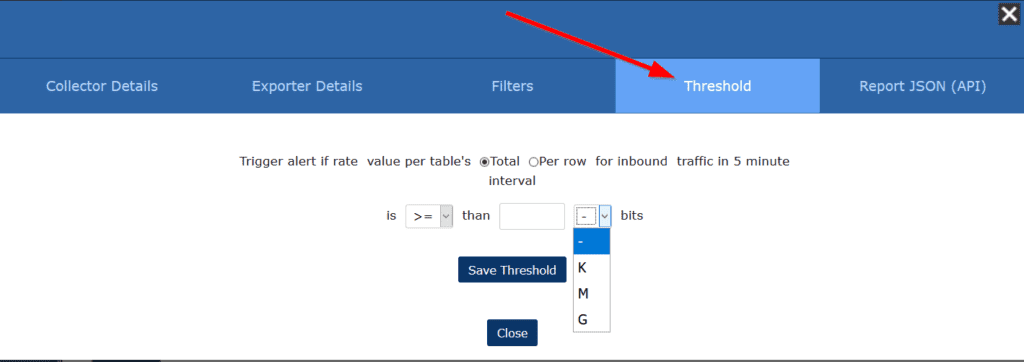
From here, we can set the value and whether the threshold is on a single communication. For example, we can have an email sent if a single IP address exceeds 5 Mbps. We can also set a threshold for when the total traffic exceeds or drops below a certain value.
Thresholds can be a warning system that informs you of an oversaturated interface. It can also be used to notify you if there is less traffic than expected. No matter how you use thresholds and email alerts, they can be a powerful feature to automate the monitoring and alerting of unwanted network activity.
Alarms Tab
Scrutinizer has a whole tab of useful data that some of our customers overlook.
The Alarms tab contains different alerts and alarms on everything from threat detection to Scrutinizer’s overall health. From here, you can quickly gauge how critical threats are, all in one location. If you set up a custom threshold, you will also see the policy violations show up here.
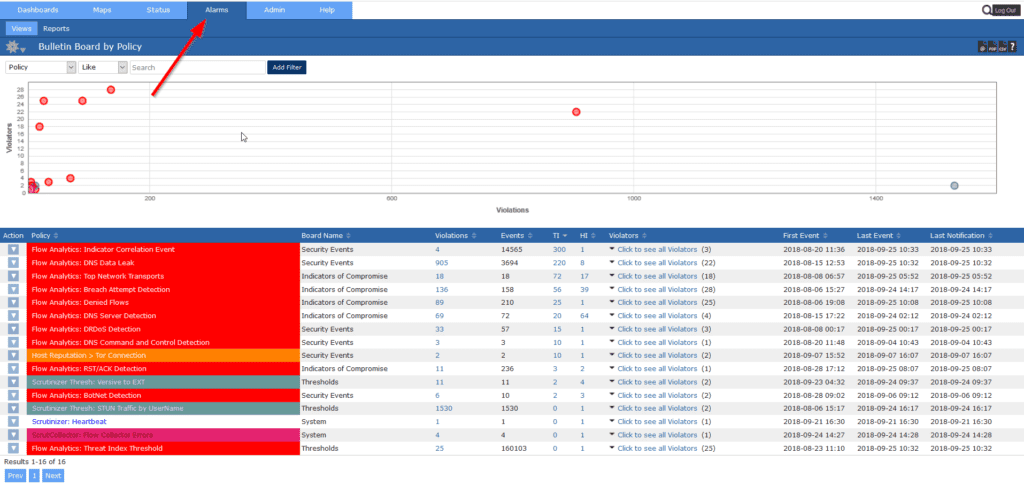
For example, this screenshot is from our test environment. As you can see, Scrutinizer has detected some DNS leaks, DR-DoS attacks, and some BotNet traffic.
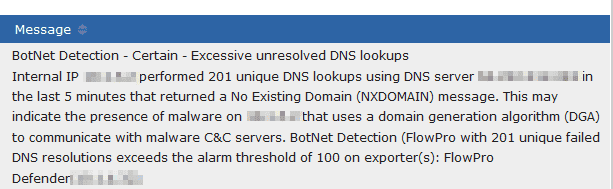
This is something that your SecOps team would want to review. Moreover, it’s a good way to introduce them to Scrutinizer.
IP Groups
Scrutinizer can set custom groups of IP addresses for fast queries. This also gives us much-needed context. For example, you could check for social media traffic by custom-defined departments, because there may be different usage expectations between departments (e.g. you would expect a lot of social media traffic from marketing).
This will allow you to quickly build new reports on the fly that can target certain subnets or IP addresses in your environment.
Navigate to Admin>Definitions>IP Groups. From here, we can name the IP group and add the IP addresses we’re looking to group.
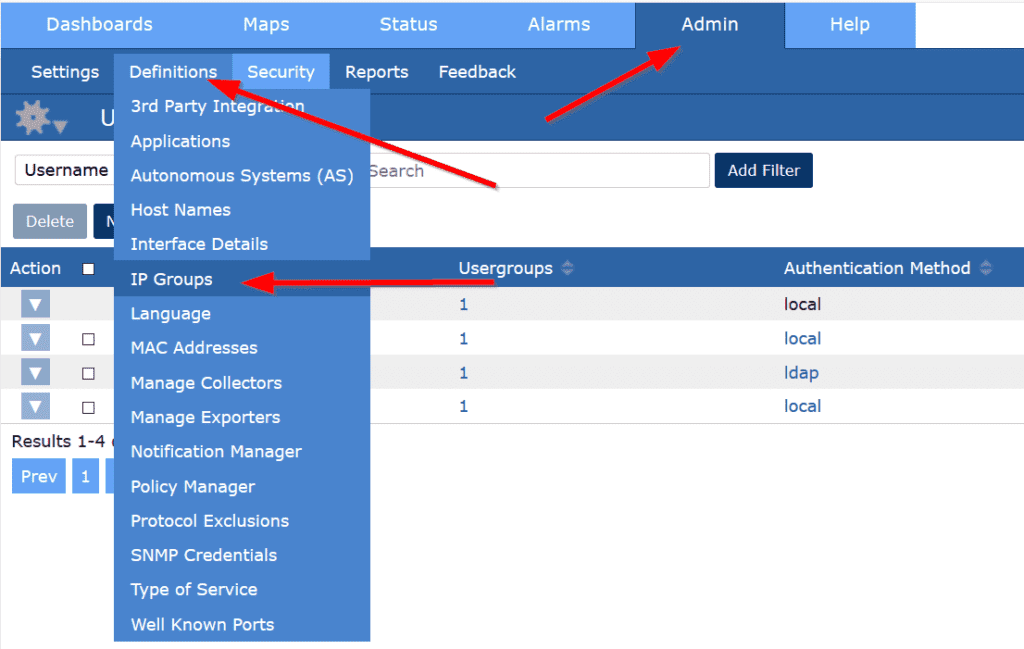
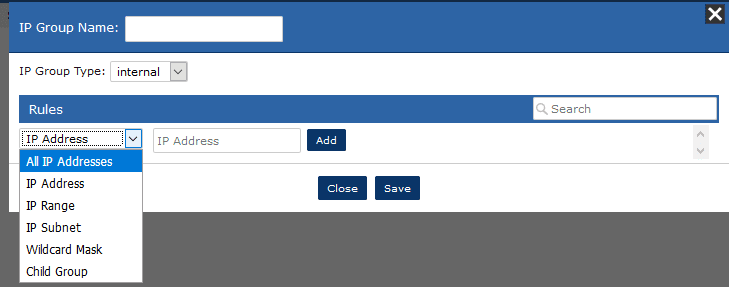
Once we define subnets or individual IP addresses, we can add filters to our reports for faster report building.
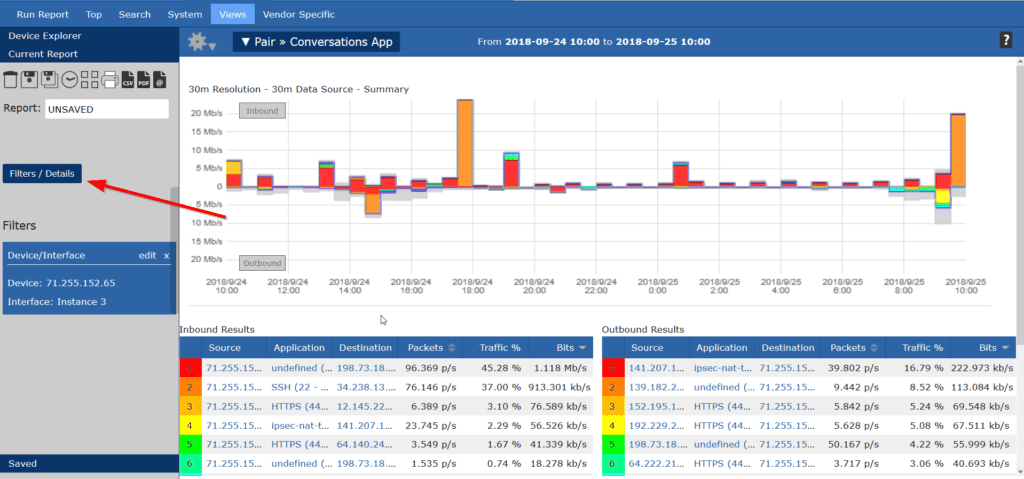
After this, go to Filters/Detail and add an IP Group from the drop-down menu. We can find the newly added IP Group and quickly make a report with use from our custom groups.
Defined Applications
Scrutinizer has many predefined applications. We try our best to include every application we come across, but there are too many programs out there to be all-inclusive. So we’ve developed a method to custom-define applications. This means that no matter what application you have on your network, you can add it to Scrutinizer.
By going to Admin>Definitions>Applications, we can define an application by its port number and/or IP address.
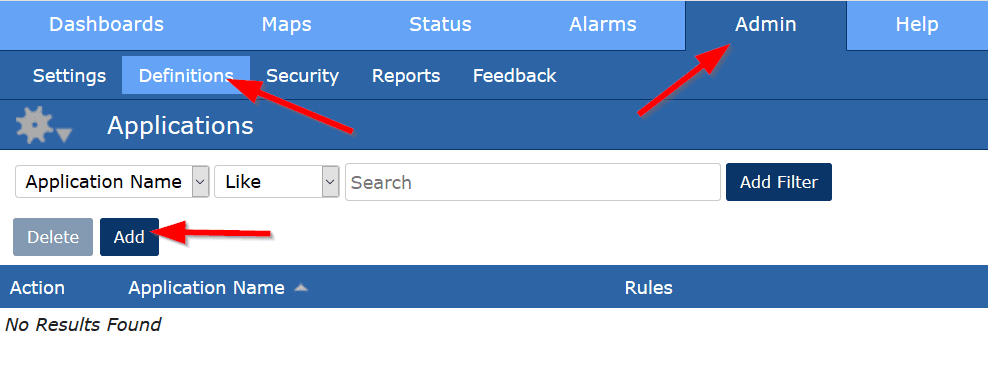
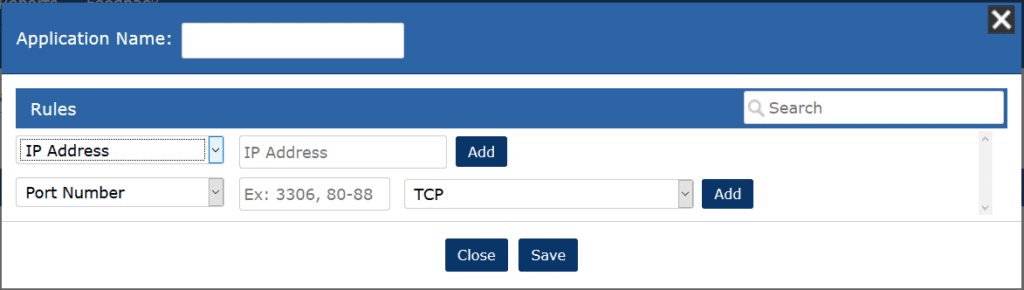
 For example, if I were in a college IT department and I wanted to see how much of the campus traffic was going to people hosting multiplayer games, I could define that.
For example, if I were in a college IT department and I wanted to see how much of the campus traffic was going to people hosting multiplayer games, I could define that.
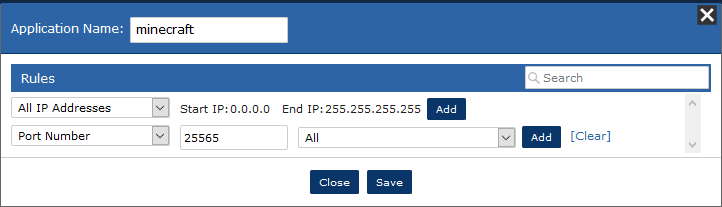
In the example below, I’m using Minecraft as an example because I know that it uses port 25565 TCP/UDP. I also don’t know what IP addresses I’m looking for, so I left it as all IP addresses. This can be done with any application that has a defined set of port numbers.
For more information on Scrutinizer features, I would suggest visiting Joanna’s blog on setting up LDAP authentication.