Supply chain attacks have become a greater risk as businesses grow more interconnected. Rather than directly targeting an organization, attackers gain access by exploiting vulnerabilities in that organization’s trusted vendors, suppliers, or partners.
What Are Supply Chain Attacks?
A supply chain attack occurs when cybercriminals infiltrate an organization by exploiting weaknesses in its supply chain network. Instead of directly attacking the target organization, attackers leverage the trust and connections established within the supply chain to gain access to sensitive data or systems. These attacks are also known as value-chain or third-party attacks, occurring when someone breaches a system through access to a supplier or service provider.
How Supply Chain Attacks Work
All businesses have some degree of trust in their vendors when they install software, use third-party services, or establish contractor agreements. Attackers identify the weakest link in this chain—often a smaller vendor with less robust security—and use that access point to reach their true target.
The attack methodology typically follows one of several paths:
- Exploiting networking vulnerabilities
- Leveraging unpatched software
- Social engineering
- Compromising software updates from trusted sources
What Makes Supply Chain Attacks So Dangerous?
This type of attack can happen to any business regardless of size or industry, from critical infrastructure to financial services, because every organization connects to supply chain partners in some way.
Furthermore, these attacks leverage legitimate connections and trusted relationships. When malicious code comes through an authorized channel or trusted vendor, it often bypasses traditional security controls. This exploitation of trust makes detection particularly challenging.
Supply chain attacks often provide attackers with a significant multiplier effect. By compromising a single vendor that serves many clients, hackers can potentially access numerous organizations simultaneously.
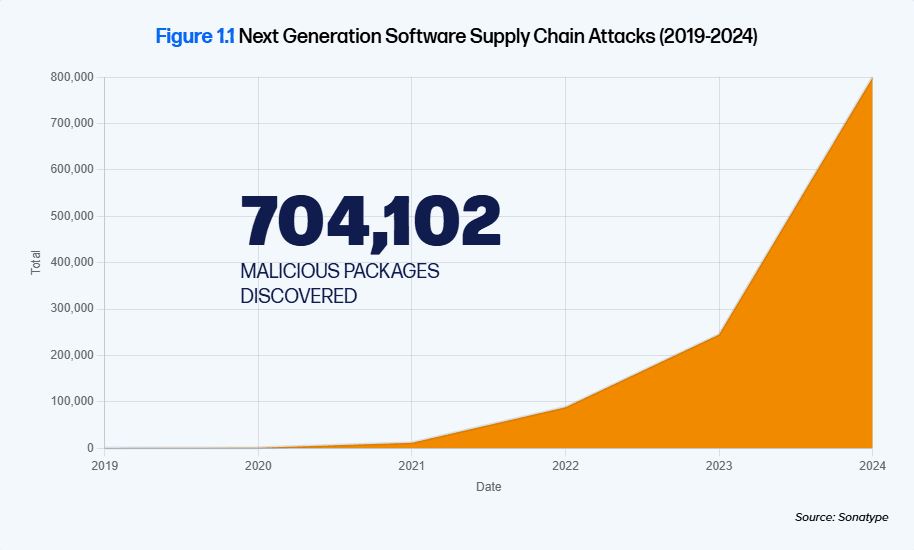
This may be why there has been an increase in supply chain attacks in the past few years. According to Sonatype’s State of the Software Supply Chain report, the number of supply chain attacks nearly tripled from 2022 to 2023, and then more than tripled from 2023 to 2024.
Types of Supply Chain Attacks
Software supply chain attacks occur when attackers target software vendors to introduce malicious code into legitimate applications. When organizations download and install these compromised applications, they inadvertently introduce vulnerabilities into their own systems. Modern application development often relies on open-source components, making vulnerabilities potentially exploitable across many different scenarios once discovered.
In hardware supply chain attacks, on the other hand, cybercriminals tamper with physical components during manufacturing or transportation. This can involve installing malicious firmware or backdoors that allow remote access to devices once operational. The Stuxnet worm that targeted an Iranian nuclear plant is a notable example, delivered via a removable thumb drive.
In a service provider attack, attackers compromise third-party service providers, such as cloud services or IT support companies, to access the data and systems of their clients.
What Are the Major Cybersecurity Threats to Supply Chains?
Organizations face several common vulnerabilities in their supply chains:
- Lack of visibility over third parties: Many organizations have limited awareness of how external supply chain entities interact with their critical systems and data.
- Poor data management: Companies may fail to securely use, store, and protect important data. Sensitive information may be carelessly shared across multiple supply chain members without considering potential consequences.
- Excessive third-party access rights: Organizations frequently grant vendors access to their systems but rarely implement proper access limitations, leading to privilege misuse and data theft.
Methods of Supply Chain Attacks
Supply chain attacks can be executed through various techniques.
Infected software and hardware: Attackers may infect software or implement malicious components in hardware. Once installed, malware spreads throughout the entire supply chain.
Trusted account compromise: This involves impersonating a familiar email account to appear as a trusted partner. Business email compromise exemplifies this approach, using social engineering to trick recipients into revealing critical data.
Watering hole attacks: Cybercriminals target websites frequently visited by multiple organizations within the same supply chain or industry, distributing malware across numerous endpoints.
Attacks on data storage services: Organizations often use third-party companies for data aggregation and storage. Attackers undermine these providers’ security to access valuable information and commit large-scale fraud.
Enhancing Supply Chain Security with Network Observability
Network observability enhances supply chain security by providing organizations with critical visibility into their digital environment. This enables early detection of anomalies and faster response to potential threats—both essential in today’s complex and interconnected ecosystems.
Real-Time Threat Detection
By leveraging machine learning, observability platforms establish baselines for typical network behavior. Any unusual activity, such as unexpected data transfers to third-party vendors or irregular login times, can quickly trigger alerts.
For instance, if a vendor account suddenly begins accessing sensitive data at odd hours, the deviation from the norm would be flagged as suspicious. Additionally, observability platforms can analyze encrypted traffic without decrypting it. Even in this limited view, abnormal patterns—like a sudden spike in data being sent to a supplier’s IP address—can signal a potential compromise.
Third-Party Risk Management
Observability platforms continuously monitor traffic between organizations and their external partners, helping identify poorly secured vendors. For example, multiple failed login attempts from a vendor’s system may indicate compromised credentials. These platforms also integrate with threat intelligence feeds to correlate network behavior with known indicators of compromise, such as IP addresses associated with recent supply chain attacks.
Incident Response Optimization
Network observability allows teams to reconstruct the attack timeline, visualizing how a threat may have moved from a vendor’s system into the internal network. This level of detail enables faster containment, such as isolating affected systems. Moreover, the tools provide detailed logs that support forensic investigations, helping pinpoint the root cause of an incident—like identifying the specific API exploited in a data breach.
Compliance and Trust Assurance
Retaining historical data of third-party interactions makes it easier to meet regulatory requirements, including frameworks like NIS2, which emphasize supply chain oversight.
Proactive Risk Mitigation
Network observability helps uncover shadow IT, such as unauthorized third-party services or APIs that employees might use without going through proper security channels.
It also aids in validating patches. By monitoring traffic patterns before and after a vendor update, organizations can verify whether vulnerabilities—like those related to the MOVEit platform—have truly been addressed.
Key Questions to Ask Vendors
According to the World Economic Forum’s 2024 Global Cybersecurity Outlook, 54% of organizations have an insufficient understanding of cyber vulnerabilities in their supply chain. To strengthen supply chain security, here are some questions to consider asking your potential and existing vendors:
How do you protect data at rest and in transit?
Vendors should explain their encryption technologies and how they secure data whether stored on servers or transmitted across networks.
What access control measures do you implement?
Vendors should authenticate users through various mechanisms such as passwords, biometrics, or multi-factor authentication, while enforcing least privilege principles.
How do you manage security incidents?
Understanding a vendor’s incident response capabilities helps assess their preparedness for potential breaches.
What is your patch management process?
Vendors should have systematic approaches to updating software and addressing vulnerabilities.
How do you monitor for threats?
Vendors should have effective threat monitoring and detection capabilities, essential for mitigating risks, implemented.
Concluding Thoughts
As organizations become increasingly interconnected through complex digital supply chains, the risk of supply chain attacks continues to grow. Understanding the nature of these attacks, identifying vulnerabilities, implementing preventive measures, and conducting thorough vendor assessments are all essential components of an effective cybersecurity strategy.
If you’re interested in a deeper look into an exploit that led to many supply chain attacks, check out our security brief on the MOVEit vulnerability.



