Inbound traffic that is captured and exported as NetFlow by your NAT router only shows that the destination of the inbound internet traffic is your external IP address. But what if you want to know what private host initiated that traffic? Today, I’d like to go over how Plixer Scrutinizer can report on this traffic and expose the internal address of this traffic.
Plixer Scrutinizer data collection
When collecting NetFlow data from multiple flow exporters, Scrutinizer does not de-duplicate flow records at collection time. This means that the flow database contains data relating to the same conversation at each observation point. So, you’ll have conversation details behind the NAT router showing the private IP.
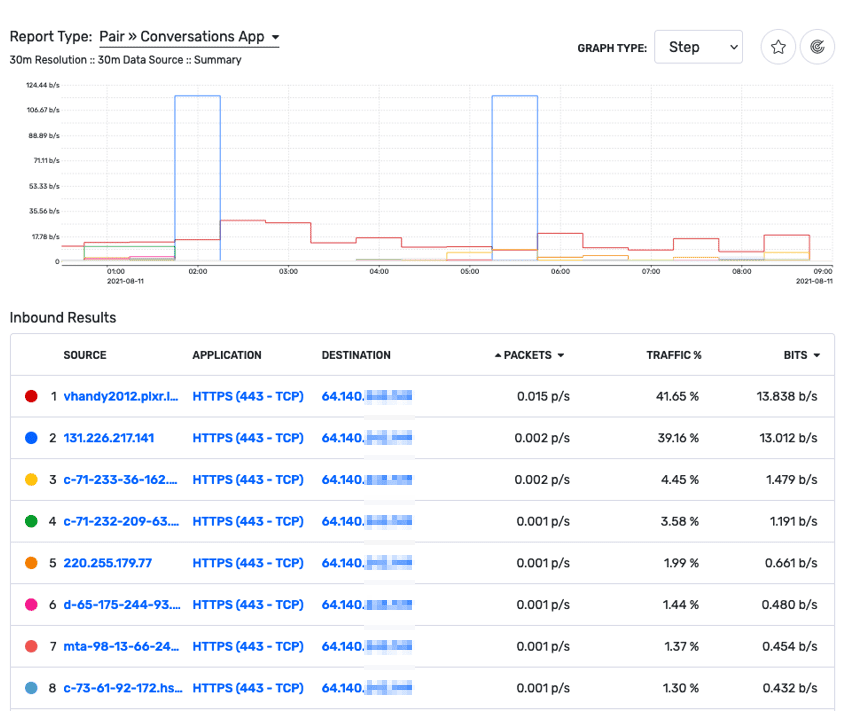
The below report of inbound traffic on our NAT router shows that all the traffic is destined for our external IP address. The conversation I’m interested in is on line 2. The connection is to 131.226.217.141, but from this report, I can’t see the internal address who initiated the conversation.
All-device reporting
Let’s switch tactics and do a search across all NetFlow-exporting devices in our network to find what internal IP address was connecting to 131.226.217.141. In Scrutinizer v19, a new report wizard was introduced to guide you through building the necessary filters to find the exact traffic you are looking for. Let’s walk through that process.
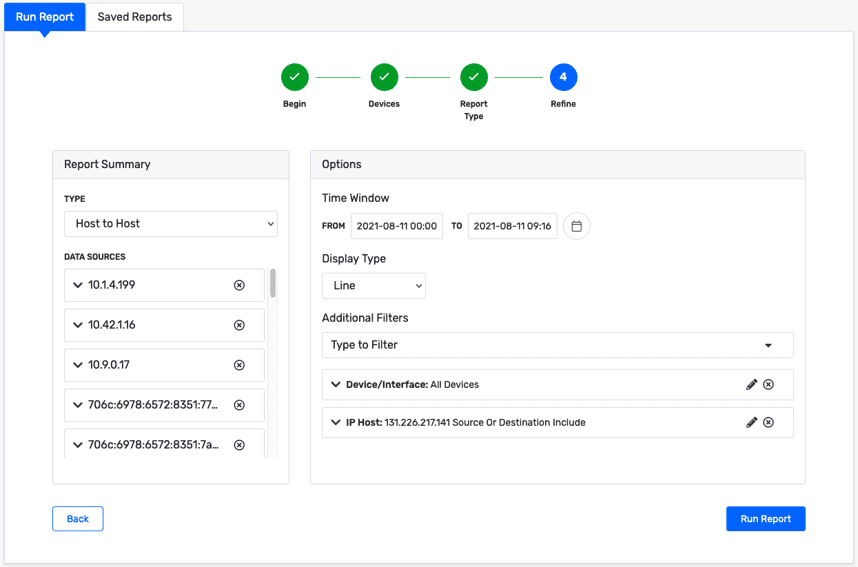
First, from the “Run Report” option in the “Reports” tab, click on “Select Devices.” Alternatively, you can select the report type first, which will limit the devices available for the report to only the ones that send the required NetFlow fields for the report type you’re looking for. But we’re only looking for a single IP host, so we don’t need to get specific here.
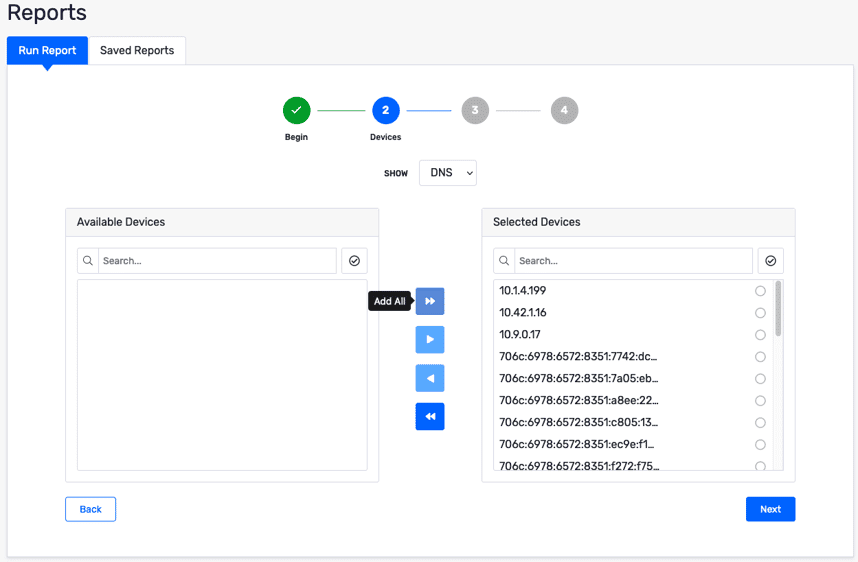
Add all of the available devices to the list of selected devices.
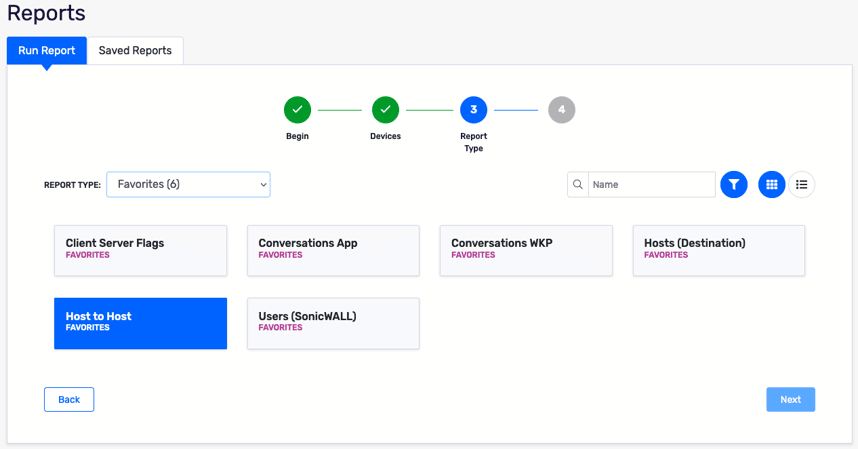
On the next page, select the Host to Host report. I use this report often, so Scrutinizer has automatically added that type to my favorites list. If you don’t have Host to Host under your favorites, you can find the report type under “Pairs Reports.”
On the next page, we will refine our report a bit more. Add a new filter for IP host, include the 131.226.217.141 address as a source or destination, and choose “Today” for the timeframe to match the first report we ran.
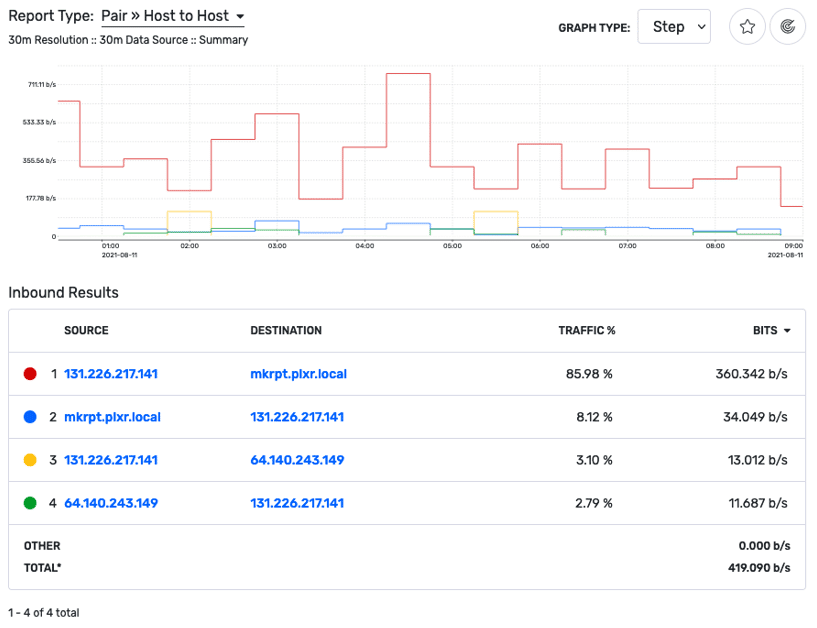
Once our report loads, we can see that the mkrpt.plxr.local server is one that initiated the conversation with the external address we were looking at. Because Scrutinizer was receiving flow data from internal devices, not just our NAT router, we can see the internal address.
Contact support today
If you are interested in seeing how Scrutinizer can help you search NetFlow data across all devices in your network, reach out to Plixer support today.