A common question that has been coming up on product demonstrations over the last few weeks is, using NetFlow, is there a way to track and locate a private host IP address behind my NAT routers?

Why is this an issue in flows collected from the NAT router?
When the NAT router builds the flow records for incoming traffic, it sees the public IP address as the destination host, not the actual private IP address.
In this blog, I will talk about an easy workflow that will help gain private address insight when the flow records collected from the router only show the public NAT address.
The answer is in the hops!
Scrutinizer can do this because of the benefits of not de-duplicating flow records during the collection process.
Scrutinizer individually stores and maintains flows exported by each network device as separate observation points. This means that you can present conversations as seen at any hop along the path. Conversations seen on the hops closer to the core show the actual IP addresses, not the NAT (public) address.
Time to walk through the workflow
Looking at the report below, you can see that all the destination addresses appear to be the public-facing IP address (64.140.x.x) of the enterprise network.
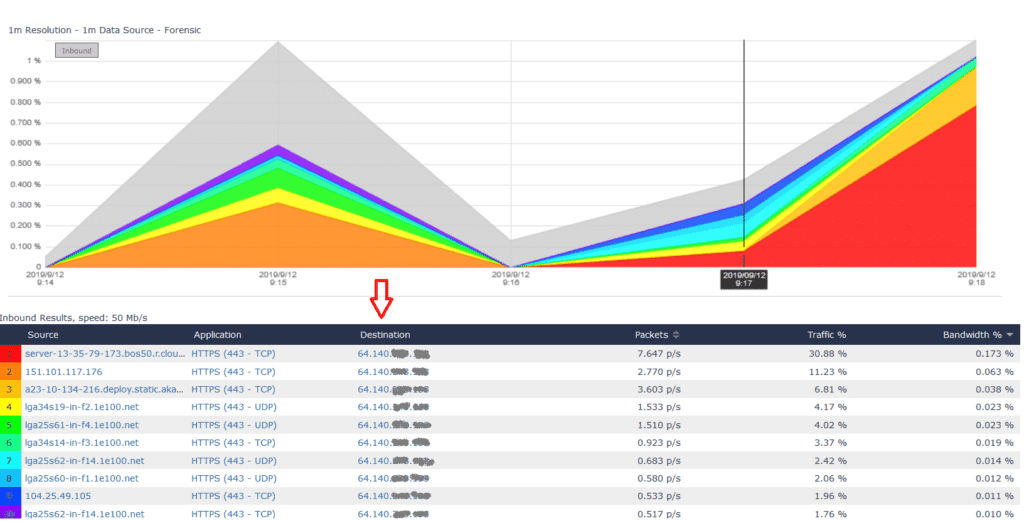
Scrutinizer has a global search function where you can search for any IP address as a source or as a destination.
Click on the magnifying glass icon in the upper right-hand corner of the WebUI to bring up the search modal.
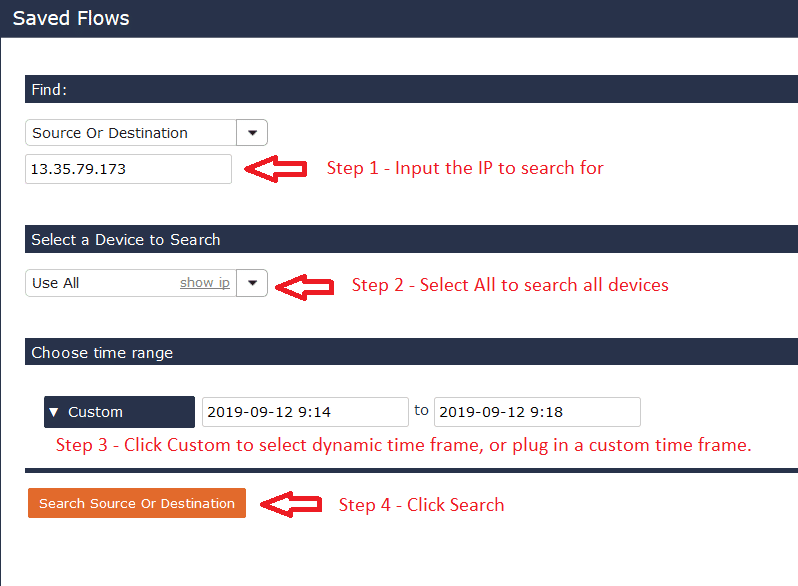
From the search modal:
- Add the IP address (as a Source or Destination) that you are looking for. In this case, add the source IP address of the incoming flow.
- Select “Use All” from the “Select Device to Search” section.
- Choose one of the dynamic timeframes from the pulldown menu, or input a custom timeframe.
- Click the “Search Source or Destination” button to run the global search.
Scrutinizer returns an All Device > Host to Host pair report filtered by the IP address input to the search.
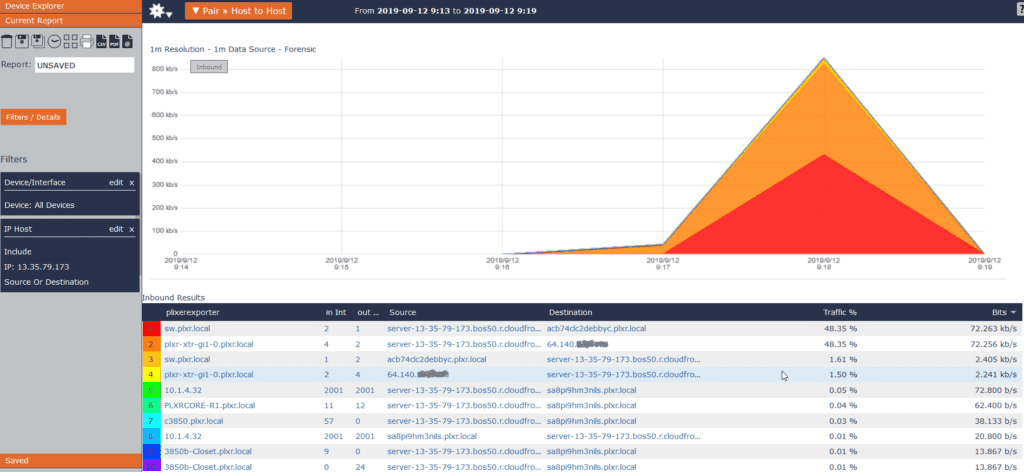
Notice that in the first two line items, we see the same flow from source IP address 13.35.79.173 going to Debby. The flow as seen on the firewall (line item #1) shows the private IP address. The flow seen from the router (line item #2) shows the public IP address.
If you look closely at line items three and four, they are showing the flow (in this case the initiator) coming from the opposite direction.
Do you have all of the network visibility that you need? Download our network traffic analysis system, configure NetFlow, and take advantage of this easy workflow.