Earlier today, the newest Distributed Denial of Service attack vectors, such as memcached and CLDAP, came up during a customer’s training session. It sparked quite a few interesting discussions, and I was asked if we could monitor CLDAP traffic with NetFlow. In this blog, I will bring you up to speed on the CLDAP Reflective DDoS attack vector. Then we will dive into Scrutinizer and create a custom report to watch for the malicious activities.
What is CLDAP?
Defined by RFC 1798 and replaced by RFC 3352, the Connection-less Lightweight Directory Access Protocol (CLDAP) is an alternative to the LDAP protocol from Microsoft. It is used to connect, search, and modify shared internet directories. While both protocols operate on port 389, LDAP uses TCP and CLDAP works via UDP. As you probably already know, LDAP is one of the most widely used protocols for accessing username and password information in databases such as Active Directory, which is integrated into lots of online servers. An incorrectly configured Active Directory server exposes the CLDAP service to the internet. This makes it vulnerable to being exploited in DDoS attacks.
CLDAP is a New Reflective DDoS Vector
Since its discovery in October 2016, Corero Network Security researchers have observed 416 CLDAP DDoS attacks. Based on the signatures, a CLDAP DDoS can amplify traffic to 70 times its normal volume. This can lead to service outages or serve as a cover-up for other malicious activities, such as breaches of personally identifiable data.
Akamai recorded the largest DDoS attack using CLDAP reflection as the sole vector on January 7, 2017. The attack was characterized by a peak bandwidth of 24 Gigabits per second as well as 2 million peak packets per second.
“The attacker would ask the CLDAP infrastructure to retrieve all the users registered in the Active Directory. Because the attacker makes this query look like it was initiated by the victim by replacing the originating IP address with the victim’s, the CLDAP service will actually send the answer to the victim. Subsequently, the victim finds itself being bombarded with the information they did not request. If the attacker can harness enough power, the victim’s infrastructure will crash under a load of unsolicited information,” explains Bogdan Botezatu, senior e-threat analyst at Bitdefender.
Monitoring CLDAP Traffic with Scrutinizer
Knowing that the CLDAP protocol uses port UDP 389, we created a custom report with the following filters:
- Advanced Filter element: sourcetransportport: 389
- Protocol filter: UDP
The Destination Host Flows report provides us with the list of the destination hosts, the number of unique hosts talking to them as well as the number of packets and flows associated with each destination:
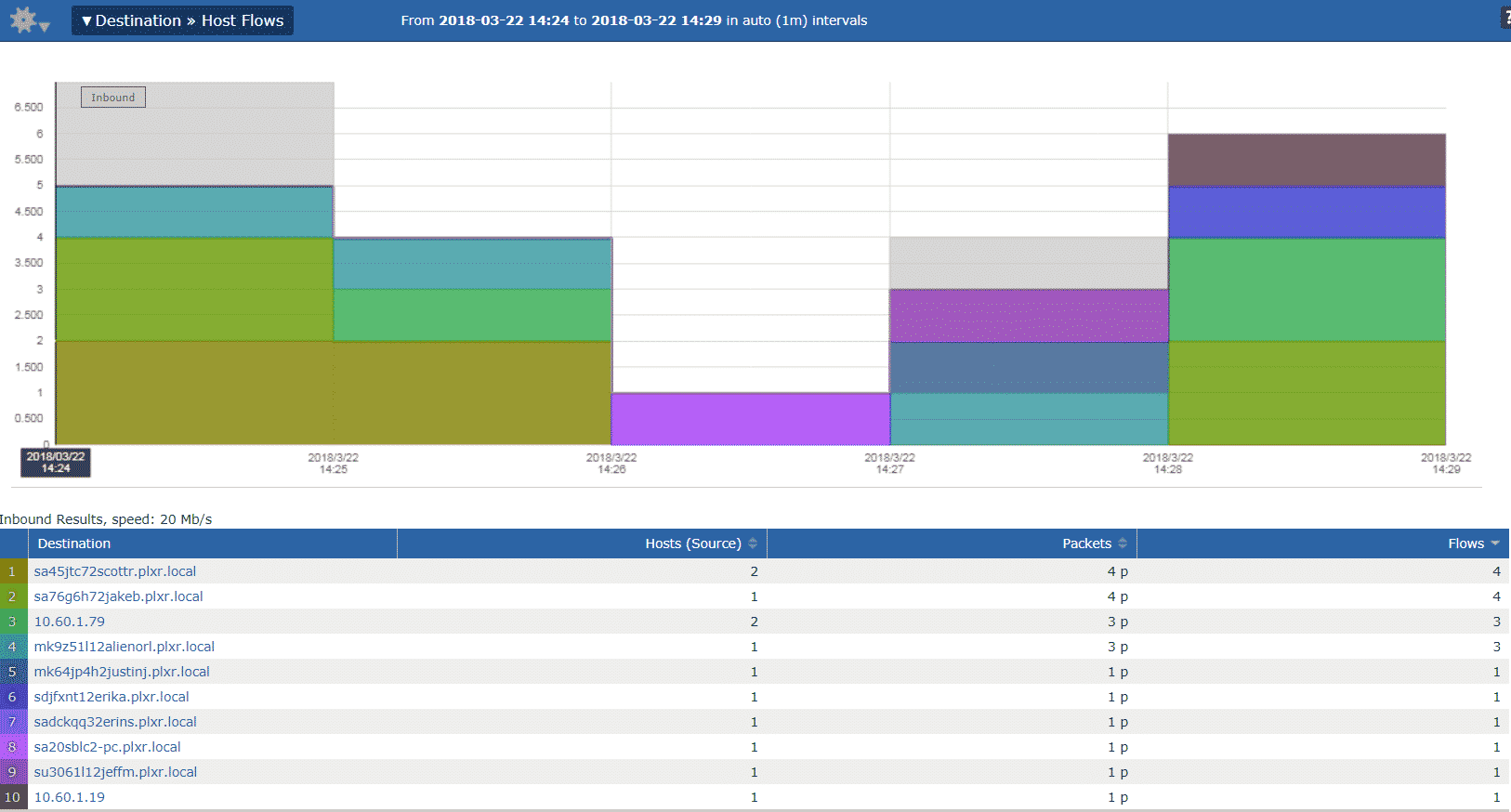
To take things to a new level, we can add a threshold to our Last Five minutes report and get alerted if the number of flows per destination exceeds certain amount.
At this point, it is a common knowledge that the complete prevention of breaches is impossible. What we all need is access to rich forensic data that supports fast and accurate incident response to quickly identify breaches and offending end stations, quarantine them, wipe the machines, and recover the data.
If you would like to see how Scrutinizer can provide insight into your own network and reduce the Mean Time To Know (MTTK), you can book a demo here.
