In the wake of recent vulnerabilities with memcached, Distributed Reflection Denial of Service (DRDoS) is currently in the focus of public attention. Using this technique has generated some of the largest attacks seen to date. This blog will cover how you can use Flow Analytics to detect this behavior in your environment.
Imagine if one day you hear a knock on the door. You answer and it is a pizza delivery person. “But I didn’t order pizza!” you tell the pizza person. He replies, “I’m sorry but we had an order from your phone number listing this address.” Suddenly another delivery person pulls in, then another… then another… until the road is backed up with cars as far as you can see. With each person it is the same story: “We got a call from your number and were told to deliver to this address.” Meanwhile, a postal worker who is bringing your Amazon order is stuck in traffic and unable to deliver. This situation is analogous to a reflection denial of service attack.
Distributed reflective denial of service (DRDoS) attacks focus on taking down the availability of an asset through an overwhelming volume of UDP responses. In these cases, the attacker would send a DNS, NTP, etc. request with a spoofed source IP, with the intention of a larger response being delivered to the host who actually resides at the address that was faked.
UDP is the protocol of choice for this type of attack, as it does not establish connection state. For example, a spoofed source IP in the SYN packet of a TCP connection would cause an immediate termination because the SYN/ACK will go elsewhere. This behavior makes reflection possible. When coordinating these attacks at scale, the concept of distributed reflection becomes clear: numerous endpoints sending spoofed UDP requests, generating responses that will be focused against a target. Once these response packets begin to arrive, the target suffers a loss of availability.
A recent exploit, “memcrashed,” took advantage of publicly exposed memcached instances, ultimately resulting in some of the largest volume denial-of-service attacks in history. Memcached is a program meant to store recently accessed data for quick retrieval in the event of high frequency queries. Attacks found that a large value could be stored in memcached and then served over UDP. A very small request to memcached can create a very large response. This is typically referred to as amplification.
How can we detect Distributed Reflective Denial of Service attack on our networks?
Using a tool like Scrutinizer gives deep insight into your network traffic. Events like a DRDoS become easy to identify and take action against when using the Flow Analytics functions in Scrutinizer.
Navigate to “Alarms > Configuration > Flow Analytics Configuration,” then select DRDoS from the list of algorithms. This will open the configuration menu for this detection method. There are 3 tabs in this menu: Exporters, Exclusions, and Settings. Under Exporters, you can define which NetFlow-exporting devices you want the detection algorithm to consider. Exclusions allows for host-level exclusions from this process. At times, the normal business conduct of a host may appear to qualify as a violation of an algorithm, and therefore needs to be removed from the pool of hosts considered. Finally, the Settings tab offers parameters for us to better shape how this function is applied against the traffic.
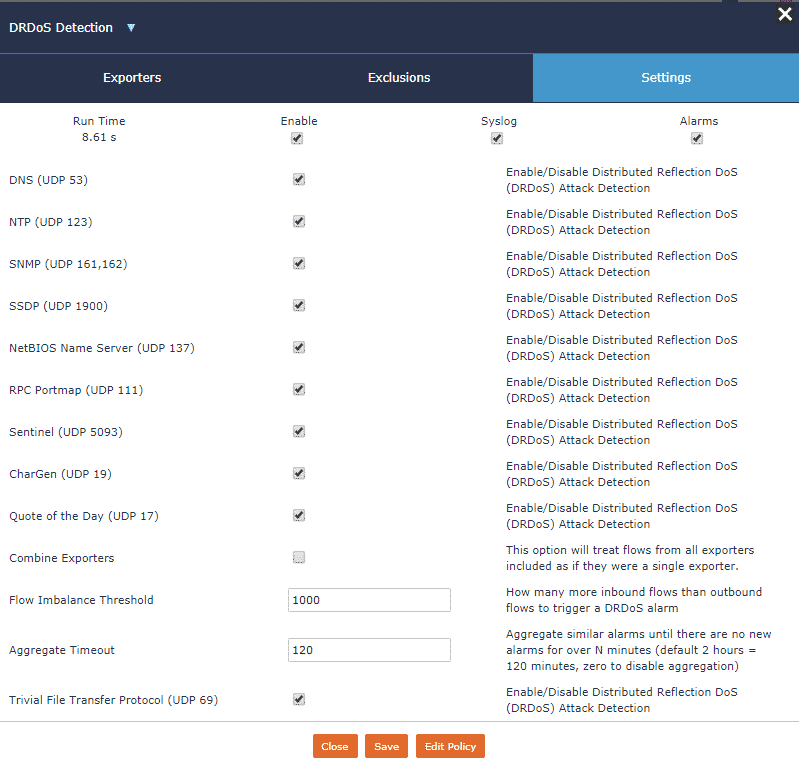
From this menu we can select which UDP applications we wish to monitor. The listed options account for the most commonly used response types in DRDoS attacks.
Selecting the “combine exporters” option lets Scrutinizer look at all of the devices listed under Exporters as one large group. This helps account for detection with multiple vectors from edge to target.
Lastly, we can select the imbalance value. This is used to set the threshold point for inbound UDP without corresponding outbound UDP.
Once configured, the detection method will begin running in the background with any positive result appearing under the Alarms tab. Our Flow Analytics suite can detect many other types of malicious activity. Reviewing the tooltips when browsing the Flow Analytics configuration list will help explain how the parameters available can be used to tune the detection functions.
Now that you know Scrutinizer is looking for DRDoS behavior in your traffic, you can count on being notified if and when your network is targeted. Whether you are interested in detecting availability attacks on your assets or just looking for better visibility into your network to improve performance, NetFlow and Scrutinizer are the best tools for the job. If you’re new to Scrutinizer, give our free evaluation a try with your network data.

