Threats today continue to endanger the security of the enterprise at an alarming rate. In fact, a recent report by Positive Technologies found that cybercriminals can penetrate 93% of company networks. And despite efforts to create robust security platforms, no single security solution will address all of the needs of the enterprise. A layered security strategy continues to be a best practice and the one most IT professionals prefer. As part of the strategy, Network Detection and Response (NDR) plays a pivotal role, as it has for many years. Before we dive into how best to implement an NDR program, let’s cover the history of this security solution.
Brief History
While the nomenclature of Network Detection and Response (NDR) is fairly new, the concept of monitoring the network for security threats is not. Since as far back as 2004, security teams have looked to the network to help solve their security needs. Back in 2004, we called this Network Behavior Anomaly Detection (NBAD). Years later NBAD became Network Traffic Analysis (NTA). NBAD and NTA used threshold and statistical baseline methods for detecting threats. While these solutions certainly detected threats, it became clear over time that these methods could be “noisy” and create false positive detections. Security teams needed a better way to raise the real threats above the noise of false positives. With the advent of Machine Learning and Artificial Intelligence, security solutions were able to process and analyze large swaths of network telemetry data to better identify and correlate unusual activity to threat tactics, and, by bringing in this technology, NBAD/NTA evolved into NDR.
Best Practices for NDR
With all of the different types of solutions out there (XDR, NDR, EDR, MDR, SOAR, SIEM, Next-gen SIEM, etc.) it can become confusing as to what to do and when. But as I look back over my 20 years working in network security, one thing hasn’t changed. Security teams need 100% visibility into the network. This is apparent by the frequency that cybercriminals are able to penetrate the network (see 93% stat above). Visibility into the network is crucial for detecting threats on the network. And the right NDR solution can deliver that visibility.
Best Practice #1
Prepare your network. By this, I mean that you need to find the right NDR solution that will afford you complete visibility without breaking your budget or time. When considering an NDR solution, it’s important to know how the solution gets visibility into the network. Does it achieve visibility via packets or flow telemetry? Does it use agents that run on critical systems/hosts? Can it decrypt traffic? And how long can you feasibly retain data given your budget? One of my co-workers wrote a blog to help you better understand the difference between a packet-based NDR and a flow-based NDR. Suffice to say you need to balance what data you can get without exceeding your yearly budget, increasing the complexity of your network, or exposing hosts to possible supply chain attacks.
Best Practice #2
Now that you have chosen the “right” NDR solution, you’ll need to Deploy it. This may sound like a trivial step, but there may be more to it than you realize. Part of your selection criteria must be the time to deploy your NDR solution, in other words getting it onto your network, fully configured, integrated into your workflows (playbooks), and detecting threats in as short an amount of time as possible.
Best Practice #3
During or just after deploying the solution you’ll need to Test to make sure the detections, notifications, actions, etc. are all working as you want them to. Often when a solution is tested in a lab or on a limited section of the network, it is impossible to know how the solution will respond to every situation, the only way to know is to test while in production.
Best Practice #4
Once your NDR solution is deployed and tested, Train your team. Certainly, your team members will need to know how to use the solution but take this opportunity to re-train the team on any changes or new workflows that the solution enables.
Best Practice #5
Make sure to take the time to Practice. Over the years the best security teams I have worked with were the ones who practice. It can be hard to think about doing this with the time and personnel constraints you may have but practicing your workflows will make your team more efficient and this will enable them to get through more alerts quickly. I encourage looking at the use of Cyber Ranges, these ranges will greatly improve the team’s skills while not burdening them in maintaining an extensive lab infrastructure.
Following these five best practices will help ensure your NDR solution is detecting threats and your team has the knowledge and workflows in place to investigate and respond to threats before they have a chance to cause damage. My sixth, and final best practice is, to take each of these steps and make it a cyclical process.
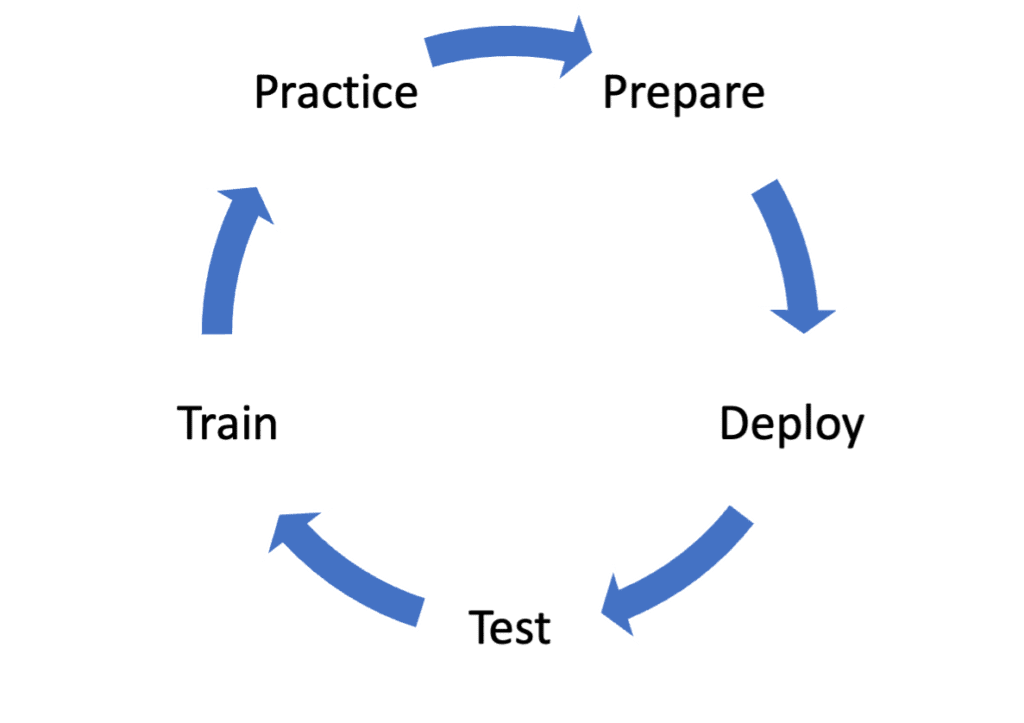
In general, I recommend this process for any of your security practices. With the way the threat landscape has evolved, enterprises need to have continual refreshers and adjustments to ensure a strong security posture.
Conclusion
For most enterprises, an NDR solution is the right place to invest your security resources. Your network traffic doesn’t lie, and attackers need the network as much as your business does. Having a solution like Plixer’s NDR platform in place will allow you to see the wake an attacker leaves as they attempt to achieve their goals. Unlike many other solutions, Plixer doesn’t add complexity to your network, use any agents, and won’t break your budget. Learn more about our NDR solution and how our advanced ML capabilities help eliminate alert fatigue in our NDR technical whitepaper.