‘Twas the night before Christmas and all through support
Phone queues were empty, no issues to thwart.
The servers we racked in the center with care
In hopes that the network would not need repair.
The switches were working, all lights showing green,
Exporting NetFlow which is all nifty keen.
When out of my email arose such a clatter,
I checked my collector to see what’s the matter.
I punched in my username and password in a flash,
And clicked my alarms, praying there wasn’t a crash.
Yet what to my wandering eye did appear
But a bright red alarm that caused me great fear.
“What does it mean?” I asked myself in fright.
I opened up my browser and went to Plixer’s website.
Since the Holidays are upon us, I thought it would be a good time to discuss Xmas Scans, also known as Christmas tree scans—the only network scan with a name that invokes thoughts of cookies, gifts and holiday joy.
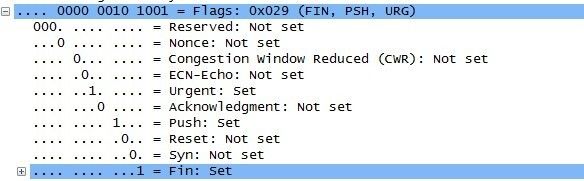
Xmas scans derive their name from the set of flags that are turned on within a packet. These scans are designed to manipulate the PSH, URG and FIN flags of the TCP header. When viewed within Wireshark, we can see that alternating bits are enabled, or “Blinking,” much like you would light up a Christmas tree. This is the humor we techies love.
Even with the non-threatening name, we should treat Xmas scans with caution just as we would any network scan. This scan uses a loophole with the TCP RFC to differentiate between open and closed ports.
“The RFC 793 expected behavior is that any TCP segment with an out-of-state Flag sent to an open port is discarded, whereas segments with out-of-state flags sent to closed ports should be handled with a RST in response. This behavior should allow an attacker to scan for closed ports by sending certain types of rule-breaking packets (out of sync or disallowed by the TCB) and detect closed ports via RST packets” – CAPEC
So in other words, the Xmas scan in order to identify listening ports on a targeted system will send a specific packet. If the port is open on the target system then the packets will be ignored. If closed then an RST will be sent back to the individual running the scan. Xmas scans were popular not only because of their speed compared to other scans but because of there similarity to out of state FIN and ACK packets that could easily bypass stateless firewalls and ACL filters. They do however run into problems with various operating systems that do not conform to RFC 793. These systems will send a RST response when any malformed TCP segment is received by a listening socket instead of dropping it. The attackers are then left guessing to which ports are open and which are closed.
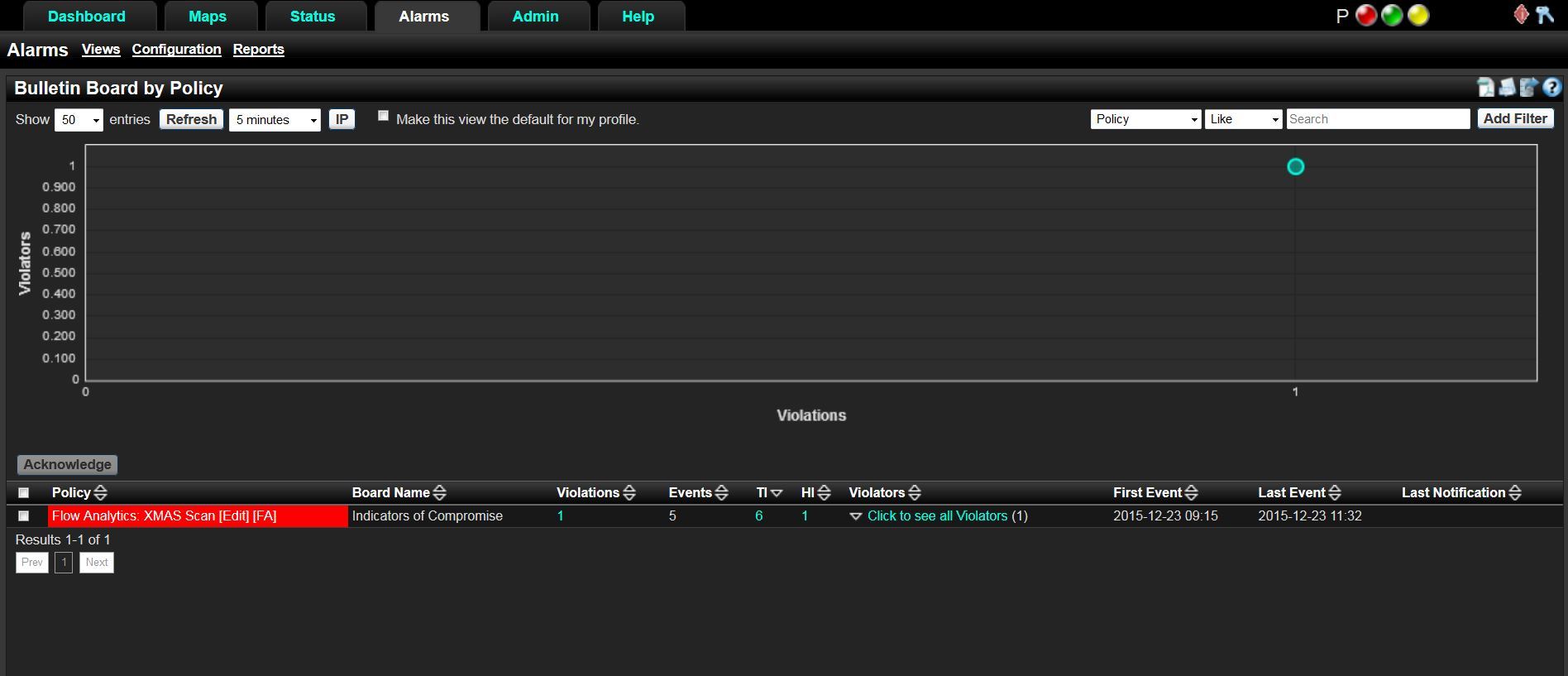
This scan actually lacks any actual holiday spirit and should be investigated. As we dig deeper into the alarms from our NetFlow collector, we can see the violator, the victim, the exporter that saw the scan and time frame. This will give us enough information to begin our investigation to find the root cause.
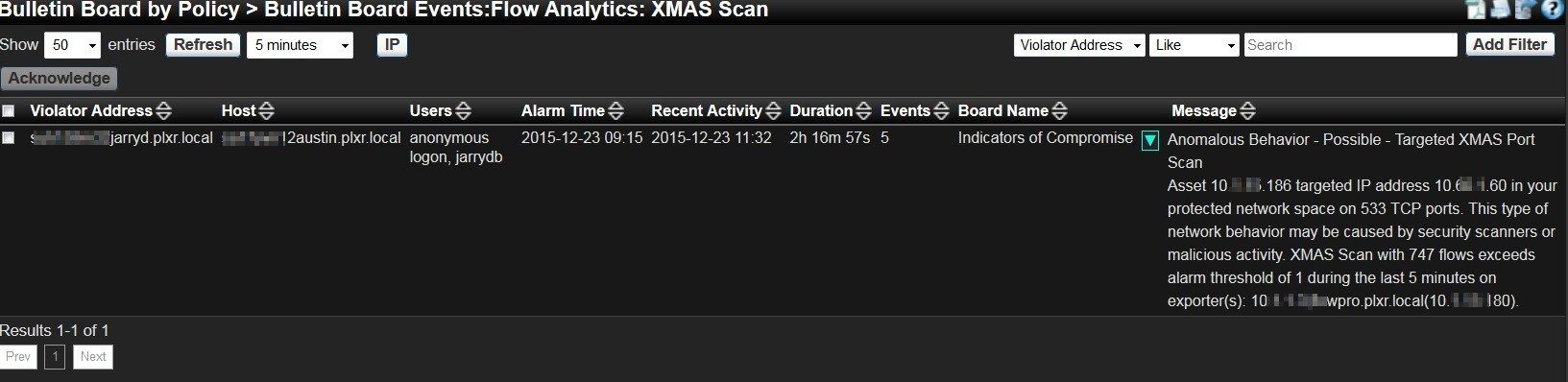
A good monitoring tool will allow a network professional to detect and respond to such incidents quickly, giving them more time to enjoy the holiday season.