Financial institutions operate in one of the most targeted sectors for cyberattacks. With sensitive customer data, monetary transactions, and regulatory compliance requirements at stake, NetOps and SecOps teams in banking, insurance, and investment firms face unique challenges that demand sophisticated network visibility and security solutions.
And the stakes are high. A single security breach can result in massive financial losses, regulatory penalties, and irreparable damage to customer trust. Yet traditional network monitoring approaches often leave blind spots that attackers exploit, while the sheer volume of network traffic makes it difficult to distinguish between legitimate activity and potential threats.
The Critical Need for Network Visibility in Financial Services
Financial services organizations operate complex, distributed networks that support:
- High-frequency trading systems that process thousands of transactions per second
- Customer-facing applications handling sensitive personal and financial data
- Internal communications between branches, data centers, and cloud resources
- Third-party integrations with payment processors, regulatory bodies, and business partners
- Remote workforce connectivity enabling secure access from various locations
This complexity creates multiple attack vectors that malicious actors continuously probe. Without comprehensive network visibility, security teams are essentially operating blind, unable to detect sophisticated threats until it’s too late.
Gaining Control Over Outbound Traffic Patterns
One of the most significant challenges facing financial services NetOps teams is understanding and controlling outbound traffic. Unlike other industries, financial institutions must maintain strict oversight of what data leaves their networks and where it’s going.
Network analysts need dynamic visibility that goes beyond simple traffic volumes. They require detailed insights into route availability, bandwidth consumption patterns, and the ability to identify which autonomous systems and applications their users are communicating with. This visibility becomes particularly crucial when investigating potential data exfiltration attempts or unauthorized communications with external entities.
Our network observability & defense platform, Plixer One, addresses this challenge by ingesting identity information from multiple sources, including Active Directory and firewall logs. This correlation provides security teams with a clear picture of user behavior, enabling them to quickly identify anomalous outbound communications that could indicate compromised accounts or insider threats.
The ability to visualize network maps in real-time helps operations teams understand:
- Whether critical routes remain operational
- The level of redundancy available for essential services
- Which users or applications are consuming excessive bandwidth
- Unusual communication patterns that warrant investigation
Defending Against Distributed Denial of Service Attacks
Financial institutions represent prime targets for DDoS attacks, which can disrupt online banking services, trading platforms, and customer communications. The challenge for security teams lies in quickly distinguishing between legitimate traffic spikes and malicious attack patterns.
Advanced DDoS detection algorithms analyze traffic patterns to identify both traditional volumetric attacks and more sophisticated reflective DDoS attempts. However, the initial alert is only the beginning of the response process. Security teams need detailed packet-level analysis to confirm whether they’re dealing with an actual attack or simply experiencing a surge in legitimate user activity.
When a potential DDoS event is identified, teams require immediate access to:
- Detailed packet analysis showing the nature and source of suspicious traffic
- Target identification to understand which services or applications are under attack
- Comprehensive flow records that provide context for the security event
- Actionable intelligence that supports rapid mitigation decisions
The mitigation process typically involves several tactical responses. Teams might implement traffic throttling to limit excessive requests from specific sources, establish geographic blocking for regions where legitimate users aren’t located, or route malicious traffic to null routes to prevent service disruption. The key is having the visibility and tools necessary to make these decisions quickly and accurately.
Tracking and Managing Network Host Activity
Financial services organizations must maintain detailed records of all devices and hosts that access their networks. This requirement extends beyond simple compliance—it’s essential for detecting compromised systems and understanding the scope of potential security incidents.
Host indexing capabilities enable security teams to maintain comprehensive visibility into every IP address that communicates within their network infrastructure. This includes tracking when hosts were first and last observed, identifying which network devices detected the host traffic, and maintaining historical records for forensic analysis.
The power of this approach becomes evident when investigating security incidents. Teams can quickly identify:
- Previously unknown hosts that have appeared on the network
- Infected systems and their communication patterns
- The scope of lateral movement during security incidents
- Timeline data that supports incident response activities
This visibility proves particularly valuable when dealing with advanced persistent threats, where attackers often establish long-term presence within network environments before launching their primary attacks.
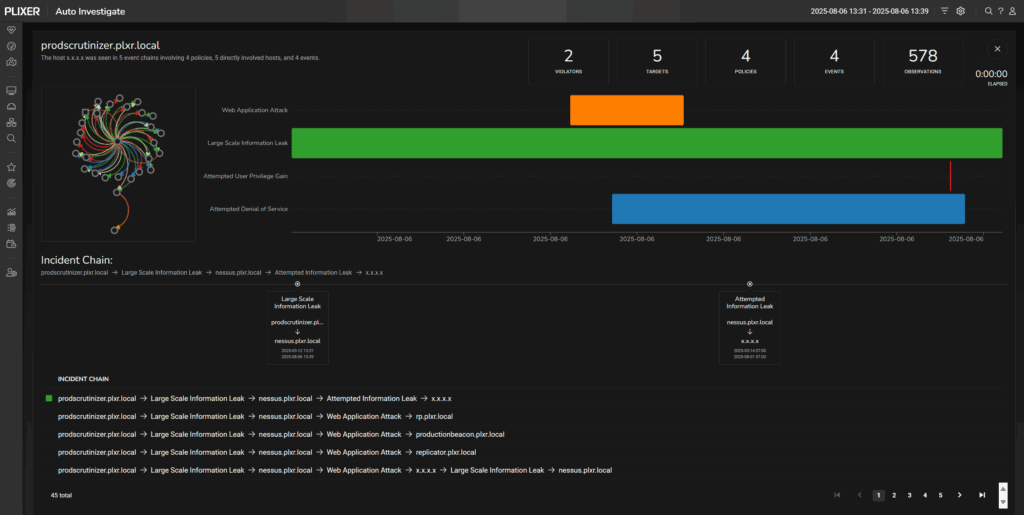
Automating Incident Investigation and Response
The complexity of modern financial services networks makes manual incident investigation both time-consuming and error-prone. Security teams need automated capabilities that can correlate events, track attack progression, and provide timeline visualization for complex security incidents.
Auto-investigation features transform how security teams respond to potential threats by providing:
Intelligent alarm correlation that identifies related security events across the network infrastructure. Rather than dealing with hundreds of individual alerts, teams can focus on comprehensive incident timelines that show the complete attack chain.
Timeline visualization that helps analysts understand the sequence of events during a security incident. This capability proves invaluable when trying to determine the initial attack vector, identify compromised systems, and assess the scope of potential damage.
Flow conversation tracking that follows malicious hosts as they move through the network environment. This behavioral analysis helps teams understand attacker tactics and implement appropriate countermeasures.
The combination of these automated capabilities enables security teams to respond more effectively to sophisticated attacks while reducing the time required for incident investigation and response.
Building a Comprehensive Security Operations Strategy
Successful network security in financial services requires more than individual tools—it demands an integrated approach that combines network visibility, threat detection, and incident response capabilities. Organizations that achieve the best security outcomes typically focus on several key areas:
Proactive monitoring that identifies potential threats before they escalate into significant incidents. This includes continuous analysis of network traffic patterns, user behavior, and system communications to detect early indicators of compromise.
Rapid incident response supported by comprehensive visibility and automated investigation capabilities. When security events occur, teams need immediate access to detailed information that supports effective decision-making and threat mitigation.
Continuous improvement based on lessons learned from security incidents and evolving threat landscapes. Financial services organizations must regularly assess and enhance their security capabilities to stay ahead of sophisticated attackers.
The combination of detailed network visibility, intelligent threat detection, and automated incident response capabilities provides the foundation for effective cybersecurity in the financial services sector.
Want to learn how Plixer One can enhance visibility into your unique environment? Book a personalized demo with one of our engineers.



