In the retail world, users at numerous branch locations, warehouses, and headquarters need access to information about products and the customers who buy them. As a result, these networks are geographically diverse and experience high traffic. All the while, many of the hosts/devices must maintain the strict measures of PCI compliance. These constraints are in place to protect the sensitive consumer information used to process card payments. Access-control lists on routers and firewalls are a good place to start. These could be configured to prevent crosstalk between devices in the “Payment Card Environment” and other segments of the network. But as one Security Affairs article highlights, point-of-sale-oriented malware commonly leverages lateral traversal techniques to avoid detection. Sure, your ACL will stop someone at the home office from trying to skim card track data, but what if the POS on the next counter over is compromised?
Your business has security cameras to prevent loss, and your network should too!
With NetFlow and Network Traffic Intelligence, we can go a step further and monitor the interfaces participating in payment transactions using the header information without accessing the data carried by the traffic. NetFlow reports on activity without further spreading information that is subject to PCI standards, unlike a packet capture solution. With a NetFlow collection and analysis tool like Scrutinizer, you can gain deep insight into the activity on your network.
Modeling your network with IP groups
With Scrutinizer Advanced Reporting, you can organize network hosts into IP groups. You can then use these groups to construct reports, thresholds, and alarms that watch all traffic moving in and out of the groups’ hosts.
- In Scrutinizer navigate to the Admin tab > Definitions > IP groups
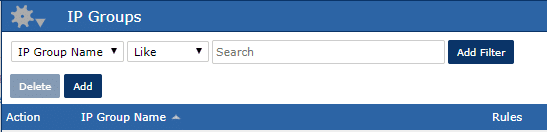
- On the IP Groups page, click ‘add’
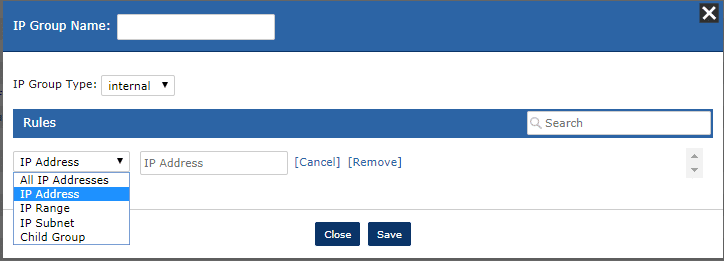
The next window that opens allows for IP groups to be defined by multiple rules. These rules can select explicitly defined addresses, a range of IPs, subnets, or other IP child groups.
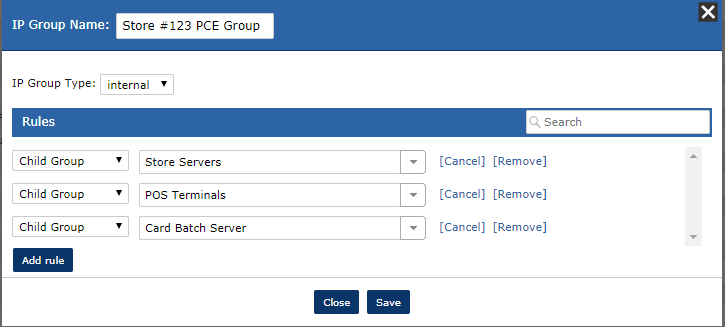
For example, we could create a group that describes all of the devices in a particular location that handle payment card information using child group building blocks such as POS terminals, store servers (these provide customer and product information to the POS) and the card processing servers.
Now from the Status tab in Scrutinizer, we can start building reports that will both give us great visibility into our network activity and allow us to alert on traffic.
On the left of the screen, you can select your NetFlow exporter from the Device Explorer. Clicking on the device will allow us to open the ‘Default Report,’ which will give us information about SRC host, DST host, and the transport information.
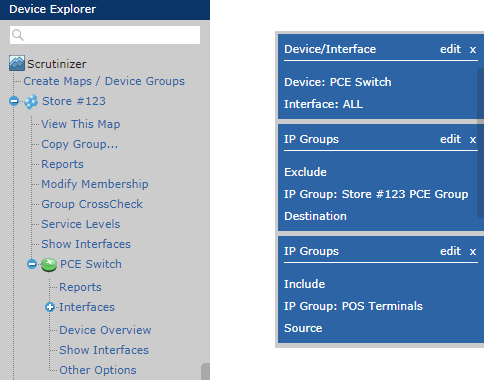
Next, we will add a filter to use our IP groups to select hosts we want to report on. There are many ways this can be applied. We could use our POS Terminals group as a source and exclude all traffic with the full ‘Store #123 PCE’ group as a destination.
If any traffic exists, like in the report below, then you have just identified information moving from your POS terminal out of the ‘Payment Card Environment.’
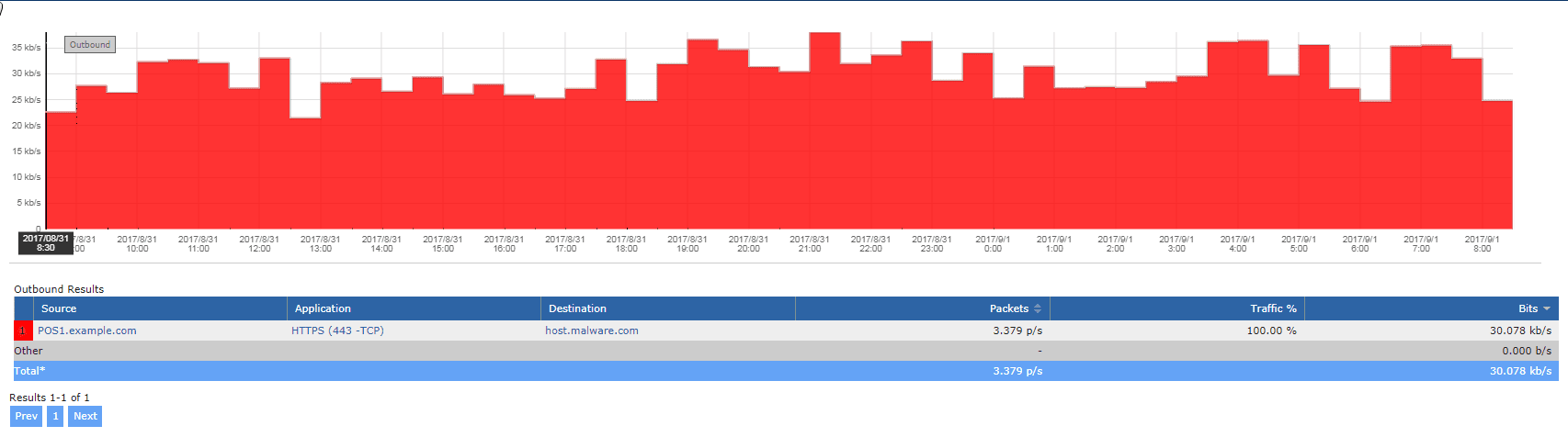
In the example above, we see a connection that has been sending HTTPS traffic to a host outside of the payment card environment. But what if the data exfiltration isn’t so obvious? A DatabreachToday article mentions a batching method for exporting data, and goes on to explain that in order to evade detection, malware will ‘save up’ data and ship it out in batches. By leveraging this method, the connection in the graph above may not have been active for the time frame we ran the report.
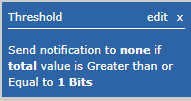 This is where Scrutinizer’s threshold feature comes into play. If we apply a threshold of 1 bit, then we will be alerted via Scrutinizer’s notification profiles. This way, you’re always watching and when the malware tries to move data, you will know.
This is where Scrutinizer’s threshold feature comes into play. If we apply a threshold of 1 bit, then we will be alerted via Scrutinizer’s notification profiles. This way, you’re always watching and when the malware tries to move data, you will know.
Not every device is capable of providing NetFlow data. But with our FlowPro solution, you can get the data you need off any device you can span traffic from. The FlowPro will generate NetFlow data and send it to Scrutinizer to allow for the type of reporting above. This means you don’t need a full hardware refresh to gain the benefit of Network Traffic Intelligence in your retail network.
