The “Internet of Things” is a buzz phrase that has been thrown around a lot in the last few years. With more and more devices becoming internet-connected (more than just phones and cameras) we are starting to see a lot more IPs on the network. This has its own problems, such as IP address spaces becoming exhausted or perhaps needing a new segregated VLAN put in place, but it’s also causing alarm for the security teams, since these often embedded devices are introducing vulnerabilities and new exploits are being found. This blog aims to cover some ways of monitoring this traffic.
Using NetFlow for IoT Monitoring:
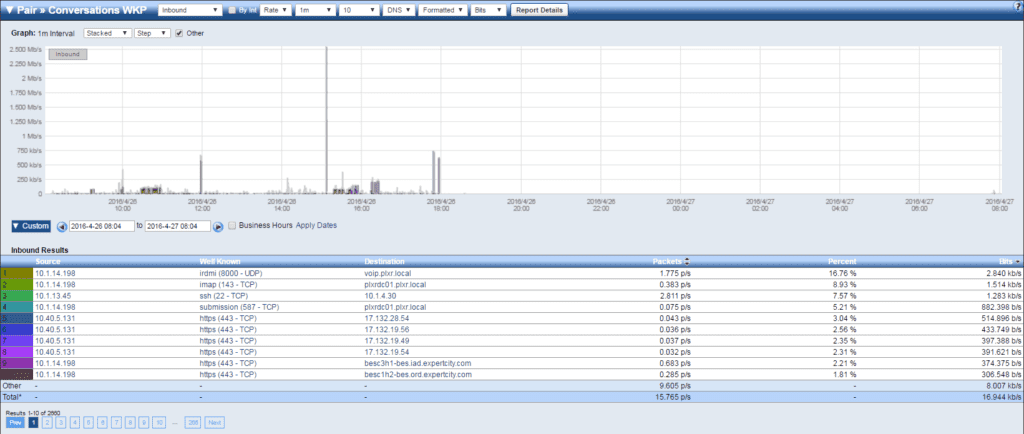
NetFlow, as we know, is great for giving us conversational metrics on all of our network traffic; this remains true for IoT devices. With the advancements in NetFlow version 9 and now IPFIX, we can also get metrics like what application is in use, the MAC address of the source/destination, and even the QoS tag. Using these elements will help you figure out who and what is talking on the network and, maybe more importantly, who they are talking to.
BYOD and IoT:
A big convergence we are starting to see is that BYOD and IoT devices are starting to blend together. An example of this could be a set top box (i.e. Chromecast or Roku) that an employee brings into the office during March Madness to stream the games on the big screen. This new device now has an IP address and internet access. Without proper monitoring and ACLs this could act as a simple backdoor into the network that would most likely go unnoticed.
As your network expands and more of these devices show up on the network, make sure you are using IP Grouping to help identify when new devices are showing up or when leases are expiring. This in conjunction with NetFlow/IPFIX monitoring will make your job easier and make remediation of security incidents a lot faster.
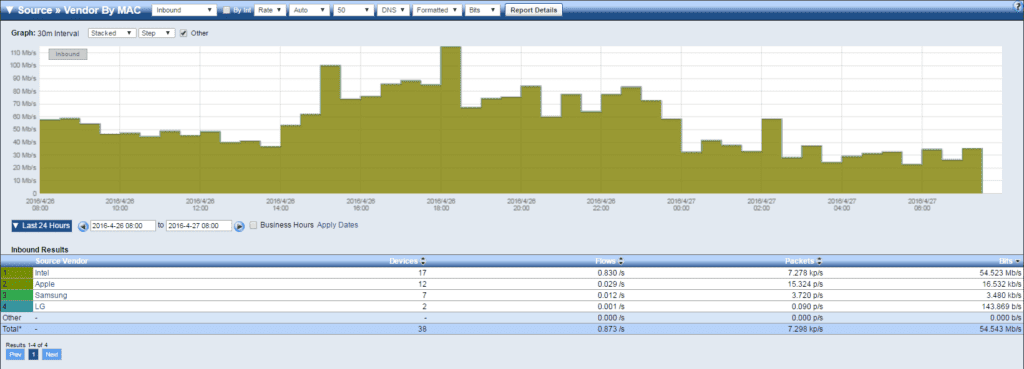
You can see in the image above that I am looking at all of the different vendor MAC addresses that are showing up on the network. Using this information, I can get an idea of the type of device as well as the number that are currently in communication or have been in communication. Furthermore, if needed, I can drill into each vendor and see what their devices are doing–maybe a large update simply caused saturation.
In closing, I hope you have a more informed outlook on Internet of Things devices on your network and are more comfortable with monitoring them moving forward. As always, feel free to reach out to me or any of our engineers with any questions you might have!