With the recent news articles surrounding botnets and how they are affecting enterprise networks, I figured this would be a good time to talk about detecting Mirai botnet traffic with NetFlow and IPFIX. Since this Botnet operates by exploiting IoT devices that have default admin/root credentials, it is causing a more mainstream push from security teams to harden internet-facing devices.
Mirai Botnet DDoS Detection:
 The Mirai botnet’s primary purpose is DDoS-as-a-Service. Detecting DDoS attacks with NetFlow has always been a large focus for our security-minded customers. Simply monitoring how much inbound traffic an interface sees, however, is not enough, since it does not always relate to a DDoS. We find that monitoring the number of unique connections and their size (in terms of both packets and bytes) is an easy way to eliminate false positives and take a more proactive approach to detection and incident response. Using our security algorithms, this is a simple and intuitive process.
The Mirai botnet’s primary purpose is DDoS-as-a-Service. Detecting DDoS attacks with NetFlow has always been a large focus for our security-minded customers. Simply monitoring how much inbound traffic an interface sees, however, is not enough, since it does not always relate to a DDoS. We find that monitoring the number of unique connections and their size (in terms of both packets and bytes) is an easy way to eliminate false positives and take a more proactive approach to detection and incident response. Using our security algorithms, this is a simple and intuitive process.
Monitoring Mirai Communications:
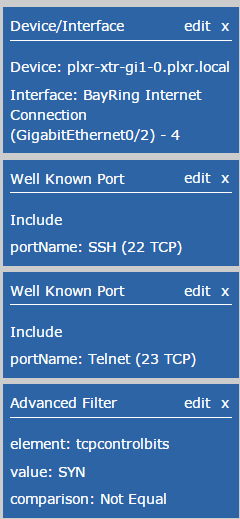
Since Mirai brute forces default credentials on Telnet and SSH services, we can simply use the filtering aspect of our NetFlow/IPFIX collector to drill into the suspicious connections and quickly tell how many times we have been hit. The filter set I typically use for this contains TCP port filters for SSH/Telnet, which are commonly abused by the Mirai Botnet. The filters are very similar to what you have seen with detecting network scans with NetFlow. I’ve also added another filter, “tcpcontrolbits.” This is a standard element that has been exported since Netflow V5. It allows us to remove the half-opened TCP connections from the report and only focus on “ACK” packets going back to the malicious hosts. Since public-IP spaces are being scanned all the time, there is no point in being alerted on it.
Botnet Detection with NetFlow:
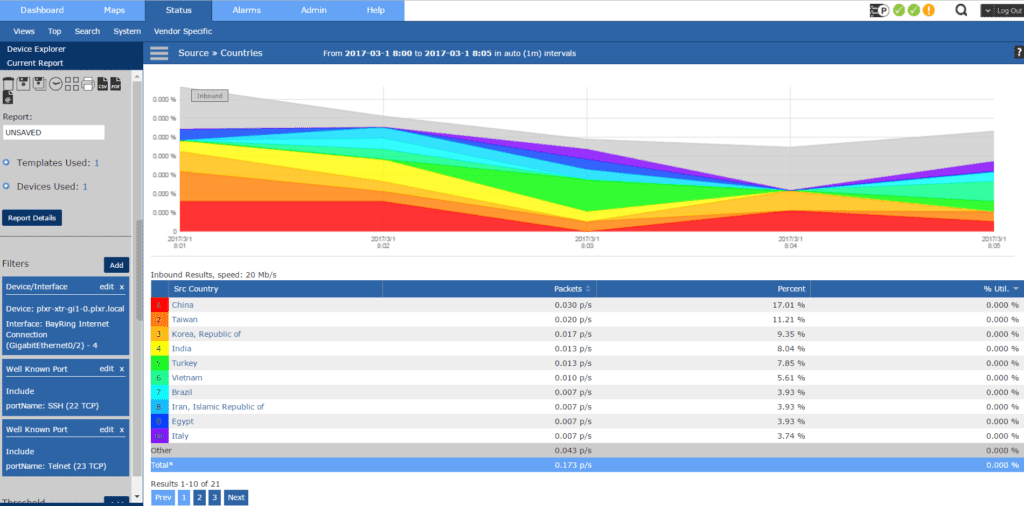
Mirai isn’t really a special botnet—it hasn’t reinvented the wheel. Default credentials are always exploited and there are even services out there that allow you to find this information through a search engine. If your company does Geo-IP blocking, we can even add metadata to the flows that allows us to view this by “highest offending country,” which gives us a nice easy-to-read view of where most of the botnet traffic is coming from.
Future of Botnet Detection:
No one really knows what the next big attack vector will be. Many credible sources believe that IoT devices will be exploited since home network security is not what most people with a residential internet connection think about. Luckily, with NetFlow/IPFIX, no matter what the attack is we will have DVR-like visibility into all of the network traffic whether it includes malicious packets or not. If you need any help in detecting the Mirai botnet feel free to reach out to our team!
