Insider threat detection has become one of the most critical aspects of modern cybersecurity. Unlike external attacks, which originate from outside an organization, insider threats stem from individuals with legitimate access to sensitive systems, data, or facilities. This makes them harder to detect and often more damaging.
What is Insider Threat Detection?
Insider threat detection refers to the process of identifying threats posed by trusted individuals—such as employees, contractors, or partners—who misuse their access either maliciously or negligently. These threats may include data exfiltration, system sabotage, espionage, or unintentional data leaks.
These threats are challenging to combat because insiders bypass perimeter defenses. For example, a malicious employee might exfiltrate intellectual property using encrypted channels, while a negligent contractor could accidentally expose sensitive data through unsecured cloud storage.
Common Types of Insider Threats
Insider threats are broadly classified into three categories:
- Malicious Insiders: Individuals who intentionally sabotage systems, steal data, or leak information for personal gain, revenge, or espionage. A classic example involves disgruntled employees selling trade secrets to competitors.
- Negligent Insiders: Employees who inadvertently compromise security through careless actions, such as falling for phishing scams or misconfiguring access controls. For instance, an engineer might accidentally publish proprietary code to a public repository.
- Compromised Insiders: Users whose credentials or devices are hijacked by external attackers, enabling unauthorized access. This often occurs through credential-stuffing attacks or social engineering.
The financial sector, healthcare, and government are particularly vulnerable due to their handling of sensitive data and high-value assets.
Key Indicators of Insider Threats
Unusual Data Movement Patterns
Sudden spikes in data downloads, transfers to external devices, or uploads to personal cloud storage are red flags. For example, an employee exporting gigabytes of customer records to a USB drive outside regular working hours could signal malicious intent. Plixer One can monitor such anomalies by tracking data movements and flagging deviations from baseline activity.
Access Abuse and Privilege Escalation
Repeated attempts to access systems or data unrelated to an employee’s role often precede insider incidents. A marketing specialist accessing HR databases or financial records without justification may be probing for exploitable information. Similarly, frequent requests for elevated permissions—such as administrative rights to restricted servers—warrant scrutiny.
Use of Unsanctioned Tools
Installing unauthorized software or hardware, such as shadow IT applications or encrypted communication tools like ProtonMail, creates security gaps. These tools can facilitate data exfiltration or bypass monitoring systems. For instance, a developer using unvetted open-source libraries might introduce vulnerabilities into critical infrastructure.
Departing Employee Activity
Employees exiting an organization—whether voluntarily or involuntarily—can exhibit heightened risks. Pre-resignation behaviors like mass downloads of strategic documents or unauthorized access to project files are common indicators.
Mismatched File Metadata
Malicious actors may rename files to disguise their contents, such as labeling a proprietary design document as “meeting_notes.jpg” to evade detection. Forensic tools that analyze file extensions and content mismatches help identify such tactics.
Strategies for Insider Threat Detection and Mitigation
Deep Network Observability
Network observability enhances insider threat detection by providing comprehensive, real-time visibility into all network activities—including lateral movement, unusual data flows, and unauthorized device access—across endpoints, servers, and applications.
By continuously collecting and analyzing flow data, telemetry, logs, traces, and packet-level data, observability tools can quickly identify anomalies or suspicious behaviors that traditional monitoring might miss, such as unauthorized data collection or encrypted traffic from unexpected devices. This allows security teams to detect, investigate, and respond to insider threats much faster, reducing blind spots and improving incident response times.
Implementing User and Entity Behavior Analytics (UEBA)
UEBA systems leverage machine learning to establish baseline user behavior and detect anomalies. For example, if an accountant suddenly accesses R&D servers at midnight, the system flags this deviation for investigation. Coupled with real-time insights from observability platforms, UEBA enhances visibility into cross-system activities, correlating login attempts, data transfers, and application usage.
Enforcing Least-Privilege Access Controls
Restricting access to the minimum necessary for job functions reduces attack surfaces. Role-based access control (RBAC) ensures that employees only interact with systems relevant to their duties. Automated tools can adjust permissions dynamically, revoking access when roles change or projects conclude.
Building Insider Threat Detection Programs
The Cybersecurity and Infrastructure Security Agency (CISA) advocates for formalized insider threat programs that integrate IT, HR, and legal teams. Key components include:
1. Continuous Monitoring and Baseline Behavior Analysis
Monitoring user behavior across endpoints, networks, and cloud environments is essential. Security tools—especially those with User and Entity Behavior Analytics (UEBA)—help establish baseline activity and flag deviations in real time. Monitoring should include:
- Login times and locations
- File access and data transfers
- Application usage patterns
- Device connections and external uploads
Continuous monitoring allows for early detection of potential threats, particularly when users attempt to bypass security policies or access unauthorized resources.
2. Employee Education and Security Awareness Training
Most negligent insider threats stem from poor security habits. An effective program includes ongoing education initiatives to build a security-aware culture. These may include:
- Phishing simulations and secure communication training
- Clear policies on data handling and cloud storage use
- Guidance on recognizing social engineering tactics
- Reporting mechanisms for suspicious behavior
Reinforcing these practices quarterly helps reduce accidental breaches and encourages proactive reporting.
3. Incident Response Playbooks
Traditional incident response plans often focus on external breaches. For insider threats, organizations should develop specific playbooks that include:
- Immediate access revocation procedures
- Digital evidence collection (e.g., device imaging, log retention)
- Coordination with legal and HR for disciplinary or legal action
- Communication plans for affected stakeholders
Having pre-approved workflows ensures faster and more effective responses to insider incidents, minimizing business disruption.
Leveraging Threat Intelligence
Integrating threat intelligence feeds with other systems enables organizations to correlate internal activities with known attack patterns. For instance, if an employee’s device communicates with a command-and-control server linked to ransomware campaigns, the system triggers an alert.
How Plixer One Enhances Insider Threat Detection
Plixer One is a network observability & defense platform that bolsters organizations’ ability to combat insider threats in several ways:
- Granular Network Visibility: Plixer One captures and analyzes metadata across all network traffic—including east-west communications—allowing you to detect internal threats that evade perimeter security.
- Behavioral Analytics with UEBA: By profiling normal user behavior, Plixer One can instantly identify anomalies that may indicate insider attacks, like unexpected data transfers or unauthorized access to restricted systems.
- Integration with Existing Security Stack: Plixer One integrates seamlessly with SIEMs, SOARs, and DLP tools to unify data and correlate alerts, enhancing your overall threat detection and response posture.
- Automated Threat Prioritization: Our AI/ML-driven alerting system reduces noise by focusing on high-risk insider behaviors, improving efficiency and incident response times.
Addressing Accidental vs. Malicious Threats
Mitigating Negligence
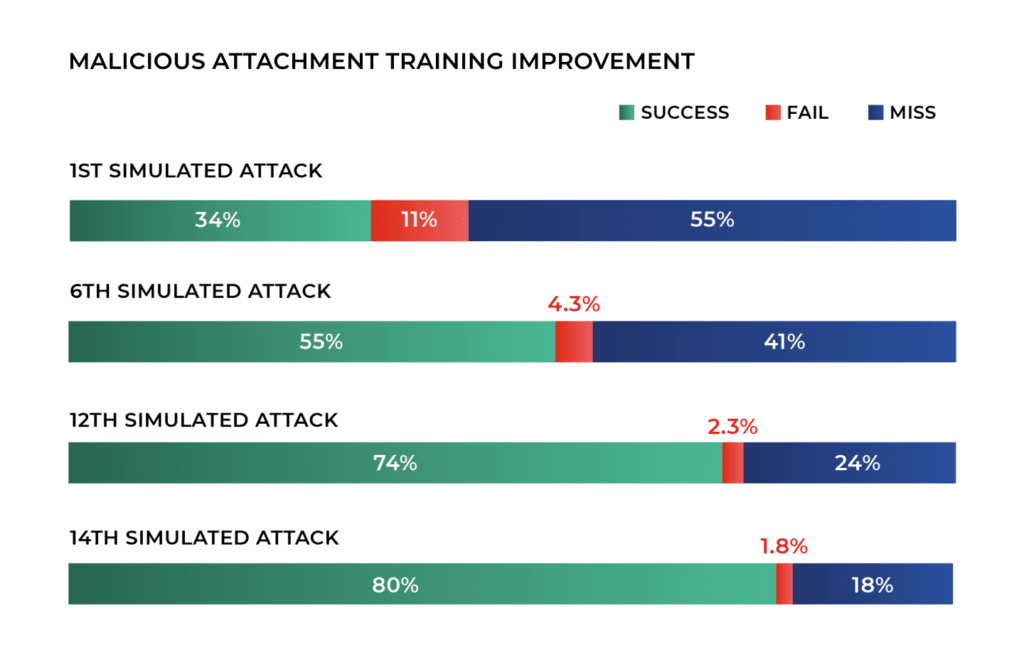
Training programs that simulate real-world scenarios, such as phishing tests or secure coding workshops, reduce inadvertent errors. For example, Hoxhunt’s 2025 Phishing Trends Report found a drastic improvement in employees’ ability to discern phishing attempts after 12 months of training. Automated policy enforcement, like blocking unapproved file-sharing platforms, also minimizes risks.
Containing Malicious Actors
Deception technologies, such as honeypots disguised as sensitive databases, can trap malicious insiders. Behavioral analytics further aid in identifying high-risk users, enabling preemptive interventions like access revocation or enhanced monitoring.
Best Practices for Responding to Insider Threats
Preparation
A crucial first step in incident response is maintaining an up-to-date asset inventory. This includes identifying and cataloging critical systems, data repositories, and all access points to ensure comprehensive visibility.
Also important is having well-defined communication plans in place. These should outline clear escalation paths for notifying key stakeholders, including executives, legal teams, and law enforcement, in the event of a breach.
Eradication and Recovery
During this phase, organizations should actively engage in threat hunting by leveraging endpoint detection tools to uncover any lingering malware or backdoors that could compromise systems.
Regularly validating data backups is also important to ensure they provide reliable recovery points.
Concluding Thoughts
Insider threats represent one of the most complex and pervasive challenges in modern cybersecurity. By understanding behavioral indicators, implementing network observability, UEBA, and least-privilege frameworks, as well as fostering cross-departmental collaboration, organizations can mitigate risks effectively. As insider tactics evolve, continuous adaptation and investment in threat intelligence will remain critical to safeguarding critical assets.
Plixer One is designed to deliver the unmatched visibility and detection capabilities that are key to insider threat detection. Book a personalized demo with one of our engineers to see how.



