For security teams, early detection is the difference between a minor incident and a full-scale breach. That’s where Indicators of Compromise (IOCs) come into play. These digital breadcrumbs—ranging from suspicious IP addresses to abnormal user behavior—serve as early warning signs of malicious activity within a system or network.
Understanding IOCs is essential for building a robust security posture, enabling organizations to not only detect threats in real time but also investigate root causes and prevent future incidents.
Understanding Indicators of Compromise
Indicators of Compromise (IOCs) are forensic artifacts that signal a potential security breach or malicious activity within a system or network. These artifacts include log entries, file hashes, IP addresses, and behavioral anomalies, which collectively help cybersecurity teams identify and mitigate threats.
The primary purpose of IOCs is to facilitate investigation, enabling organizations to reconstruct attack timelines, identify exploited vulnerabilities, and strengthen defenses against future incidents. For example, an unexpected surge in outbound traffic from a server could indicate data exfiltration, prompting immediate investigation.
Historical Context and Evolution
The concept of IOCs gained prominence alongside the rise of advanced persistent threats (APTs) and targeted attacks in the early 2010s. David Bianco’s “Pyramid of Pain” framework, introduced in 2013, suggested a method of prioritizing Indicators of Compromise based on the difficulty of detection and the impact on adversaries.
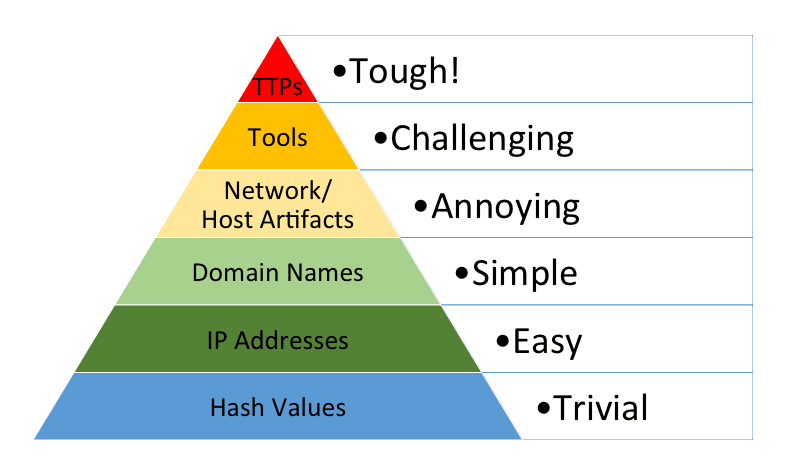
This framework categorizes IOCs into levels such as hash values, IP addresses, and domain names, with higher levels (e.g., tactics, techniques, and procedures) posing greater challenges for attackers to alter.
The evolution of IOCs reflects a shift from reactive to proactive threat detection, emphasizing the need for continuous monitoring and intelligence sharing.
Types of IOCs
Host-Based Indicators of Compromise
Host-based IOCs focus on anomalies within individual systems. These include:
- File Hashes: Unique identifiers for malicious files, such as MD5 or SHA-256 hashes. For instance, a ransomware executable might be identified by its distinct hash signature.
- Registry Modifications: Unauthorized changes to Windows registry keys, often used by malware to maintain persistence.
- Process Anomalies: Unfamiliar processes running in the background, such as cryptocurrency miners or keyloggers.
Network-Based Indicators of Compromise
Network-based IOCs involve irregularities in traffic patterns or communication with known malicious entities. Examples include:
- Suspicious IP Addresses: Connections to IPs associated with command-and-control (C2) servers. A sudden spike in traffic to a foreign IP could signal data exfiltration.
- Unusual Port Activity: Attackers may use unusual ports to bypass security measures and establish connections.
- DNS Query Anomalies: Repeated requests to domains linked to phishing campaigns or malware distribution.
Behavioral Indicators of Compromise
Behavioral IOCs center on deviations from normal user or system activity. These include:
- Privilege Escalation: Sudden attempts to gain administrative rights, often a precursor to lateral movement within a network.
- Geographical Irregularities: Logins from countries where an organization has no operational presence.
- Data Compression Spikes: Large volumes of data being compressed or encrypted, indicative of ransomware activity.
Detection and Monitoring Strategies
Network Observability & Defense Platforms
To effectively detect and act on Indicators of Compromise, traditional monitoring can often fall short—security teams need deep, contextual visibility into their entire digital environment. This is where network observability platforms come into play, offering a comprehensive view of system behavior and network activity that goes far beyond basic alerting.
By continuously collecting and analyzing telemetry, logs, and traces from endpoints, servers, and network devices, observability tools provide the real-time insight needed to spot subtle anomalies. These might include unexpected data transfers, connections to known malicious IP addresses, or unusual traffic patterns that would otherwise go unnoticed.
What sets observability platforms apart is their ability to transform raw data—like an IP address or domain name—into meaningful IOCs. With enriched context from threat intelligence and behavioral baselines, an otherwise benign-looking data point can be flagged as malicious, prompting immediate investigation.
For example, an outbound connection to a rarely used port might seem insignificant… until it’s correlated with known command-and-control infrastructure.
These platforms also support early detection through automation. By defining thresholds and modeling normal behavior, they can generate real-time alerts when activity deviates from the expected. This enables security teams to respond to emerging threats before they escalate, reducing MTTR and limiting potential damage.
Human-Centric Approaches
While automation is incredibly useful, human expertise remains crucial.
Threat hunters analyze Indicators of Compromise to uncover stealthy attacks that evade automated systems. For example, an analyst might notice that a legitimate-looking PDF file is initiating PowerShell commands—a red flag for malicious macros.
Employee training also plays a role; staff educated to recognize phishing emails or report unusual system behavior can serve as an early warning layer.
Incident Response and Mitigation
- Validation: Confirm the legitimacy of detected IOCs. A suspicious IP address, for instance, might be cross-referenced with threat intelligence feeds to verify its malicious status.
- Containment: Isolate affected systems to prevent lateral movement. Network segmentation or disabling compromised user accounts are common tactics.
- Eradication: Remove malicious artifacts, such as deleting malware files or patching exploited vulnerabilities.
- Recovery: Restore systems from clean backups and monitor for residual threats.
- Post-Incident Analysis: Document IOCs to refine future detection strategies and share findings with industry peers.
Example: Ransomware Attack
Consider a ransomware attack where Indicators of Compromise include encrypted files with .locky extensions, unusual SMB traffic, and connections to a Tor gateway.
By correlating these IOCs, the response team can identify the attack vector (a phishing email), contain the infection by isolating affected servers, and restore data from backups.
Post-incident, the organization can update its email filtering rules and block the associated malicious IPs.
Challenges and Limitations
Reactive Nature of Indicators of Compromise
IOCs are inherently retrospective, often identified after a breach has occurred. For example, a zero-day exploit might go undetected until its signature is added to threat databases. This lag leaves organizations vulnerable to novel attacks, necessitating complementary approaches like behavioral analytics.
Scalability and False Positives
The volume of IOCs generated by modern systems can overwhelm analysts. A SIEM might flag thousands of events daily, with many being false positives. Tuning detection rules and prioritizing high-fidelity IOCs (e.g., those linked to active campaigns) helps mitigate this issue.
As discussed above, a network observability platform can offset this challenge with AI/ML-driven contextual insight. Plixer One users can also leverage its AI/ML engine to verify alarms generated by other platforms.
Adversarial Adaptability
Attackers frequently alter Indicators of Compromise to evade detection. Polymorphic malware, which changes its hash signature with each iteration, renders static hash-based detection ineffective. Security teams should therefore focus on higher-level indicators, such as TTPs, which are harder for adversaries to modify.
Concluding Thoughts
Indicators of Compromise are foundational to effective cybersecurity operations. By identifying the signs of malicious activity early, organizations can contain threats before they cause significant damage.
However, IOCs have some drawbacks. Their retrospective nature, susceptibility to evasion, and potential for false positives highlight the need for complementary approaches such as behavioral analytics and threat intelligence. By combining advanced detection technologies with skilled human analysis, security teams can turn raw data into actionable insights.
For more on using network data to detect otherwise stealthy threats, check out our blog on insider threat detection.



