Do you know how to define your own Cisco NBAR applications?
In today’s networks, application recognition is no longer one of those ‘nice to have’ options when it comes to traffic monitoring, it is a necessity.
Many vendors are now exporting application definitions in their flow exports.
Using NBAR, applications like H.323, Telnet, RTP, Exchange and Skype can all be identified. Additionally, if you are running IOS release 15.1 or higher, can be exported in NetFlow exports.
On a call last week, a customer was looking at various NBAR reports, and seeing a significant amount of traffic showing up as “unknown”, and was wondering what this traffic was and what was the best approach for handling it.
The best way to reduce the amount of “unknown” traffic is twofold.
- Make sure you have the latest possible IOS version. Cisco seems to add support for various PDLMs with various releases of IOS. With the newer versions of IOS, I have seen quite a bit of new apps defined in NBAR. So upgrading the IOS seems like the best way to increase the overall accuracy of NBAR.
- Try and identify unknown traffic using WKP(well known port) reports, then create custom NBAR application definitions on the router.
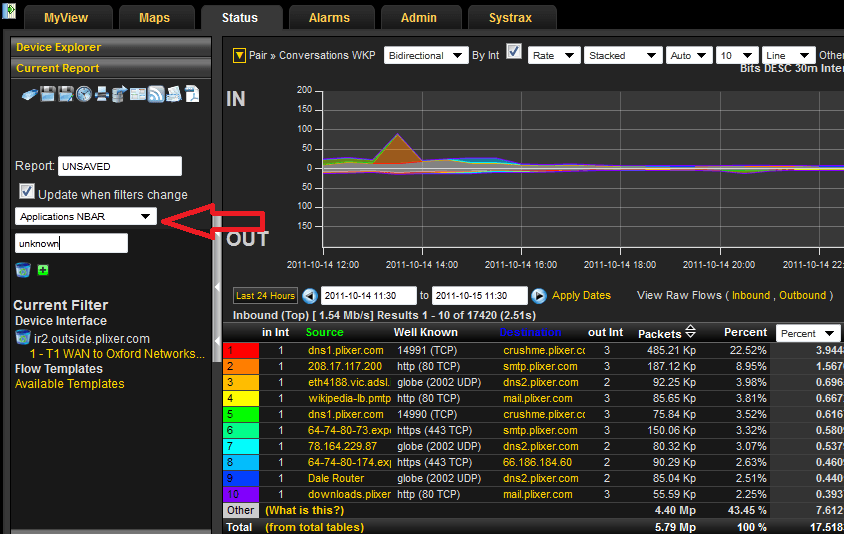
Using an “Applications NBAR” report filter, we can look at only the traffic tagged as “unknown” . This will allow us to look at a well known port report of all the traffic the router can’t identify using NBAR.
Once applied, the report will show you the traffic that you want to identify.
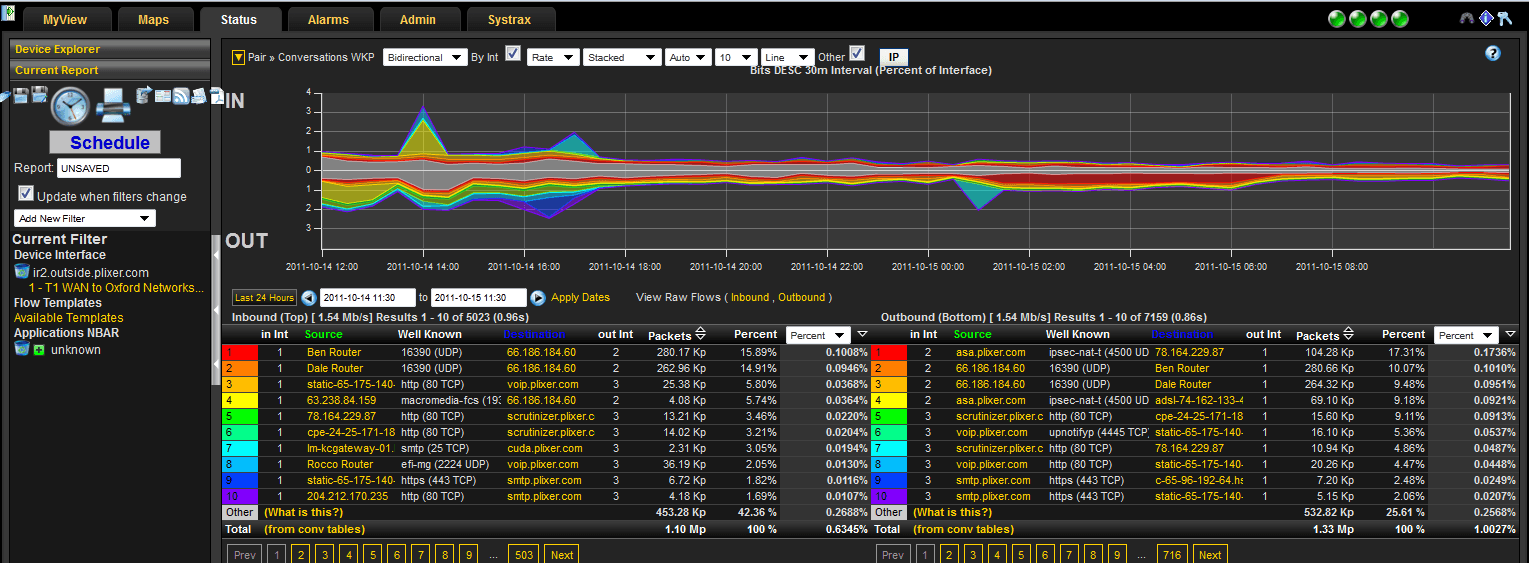
Now, I have already been through this process on this router, but I do see some outbound traffic that I can identify on UDP port 4500.
I will define this application on the router since I know what it is. IPSEC VPN traffic.
(config)#ip nbar custom vpnipsec udp 4500
Now all traffic on UDP port 4500 (source and destination) will be marked as vpnipsec by NBAR.
I also know that all my traffic on UDP 16390 is relating to PfR active monitoring.
So I’ll create an NBAR app for this called “pfractmon”.
(config)#ip nbar custom pfractmon udp 16390
If you do this with each protocol, you’ll find that most of your traffic will no longer be “unknown”.
Some of the traffic seen here looks like HTTP, but is not. NBAR already has a definition for HTTP, but it looks deeper into the packet. You will not be able to add a definition using TCP 80 since it already overlaps the “real” tcp definition.
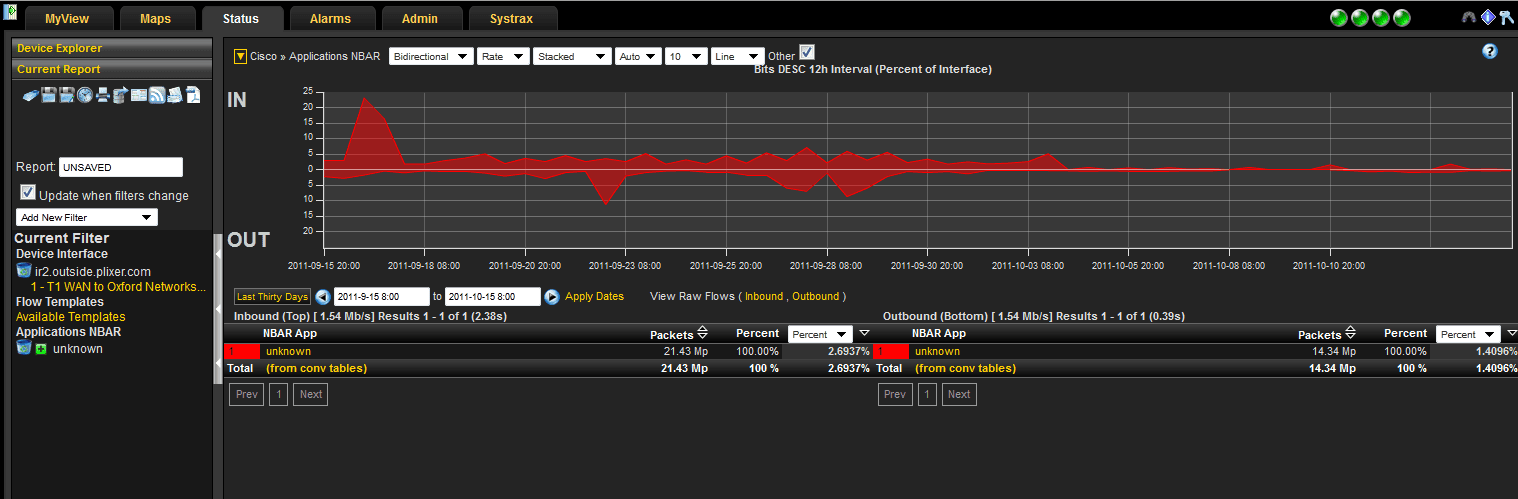
Here we can see that a report trend shows that the amount of “unknown” traffic dropped off quite a bit.
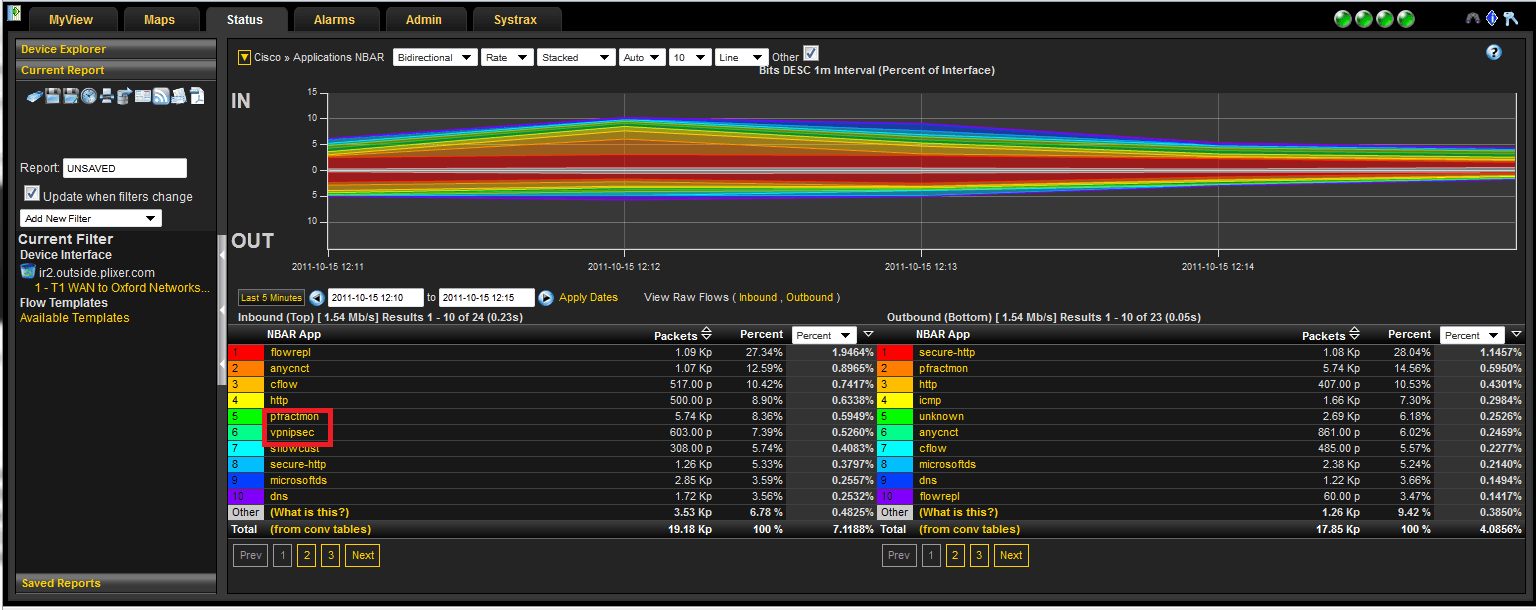
And, if you look at a few minutes of new NBAR data you’ll see that this traffic is now being marked with the new NBAR definitions.
Get visibility into the applications traversing your network. Define your custom applications and put our NBAR report filtering options to work for you.