According to Gartner, when it comes to context-aware security, the most commonly cited context types are location and time. However, there are multiple types of context that can be used to glean information about your network. If you are a security professional who feels that they are losing visibility with NetFlow, there are ways to add insightful context-aware security information such as device names, FQDNs, URLs, application names, countries, and even authenticated usernames.
Visibility is getting lost
While we can learn a great deal about our network traffic with flow data, we’re not seeing everything. Sure, we can see when and where a network issue may arise, but there is a great deal of information missing that can help make security decisions easier.
Initially, NetFlow was being used to troubleshoot network issues such as excessive bandwidth consumption. Today, NetFlow can also be used to turn your network devices into sensors, which add to your cyber defense tool chest. By using the granular flow data from your network, you can see not only the where and the when, but also who, what URLs they visited, who they may have communicated with, and what fully qualified domain name (e.g. netflix.com) they are reaching out to. This is especially helpful as more and more traffic is leaving the network as encrypted traffic.
How can Scrutinizer help?
This is where Scrutinizer comes in. With our system, we can drill into network traffic and view the context-aware security information needed.
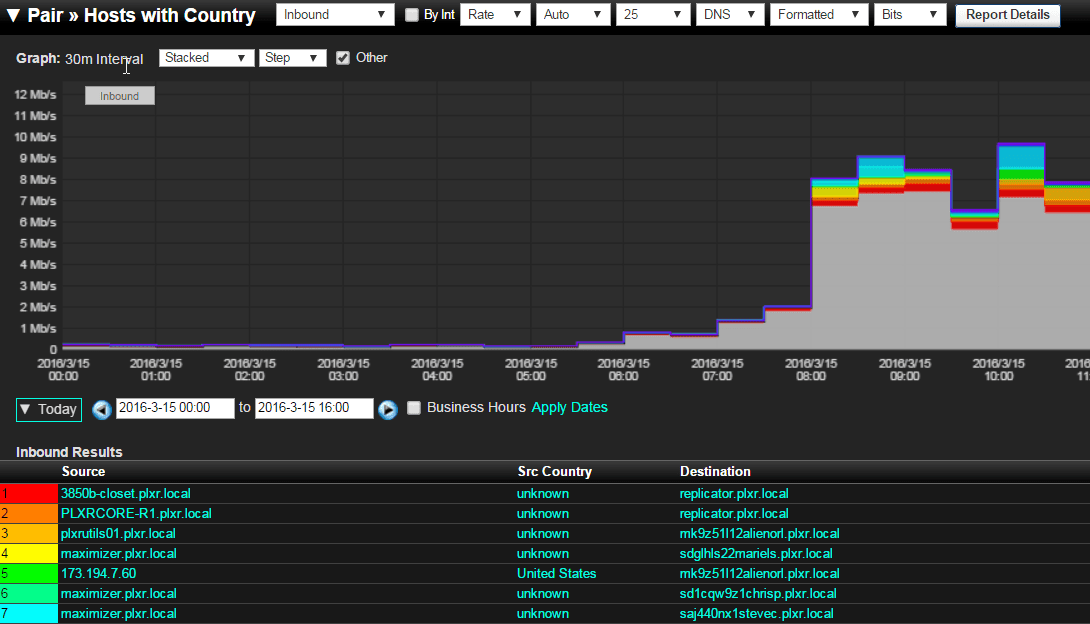
First, we can view the countries that usernames on the network are reaching out to. And by running a pairs report, we can choose to view the host username, the source country, and the destination. While communicating with foreign countries is not always a bad thing, this context may be an important clue while investigating malicious behavior.
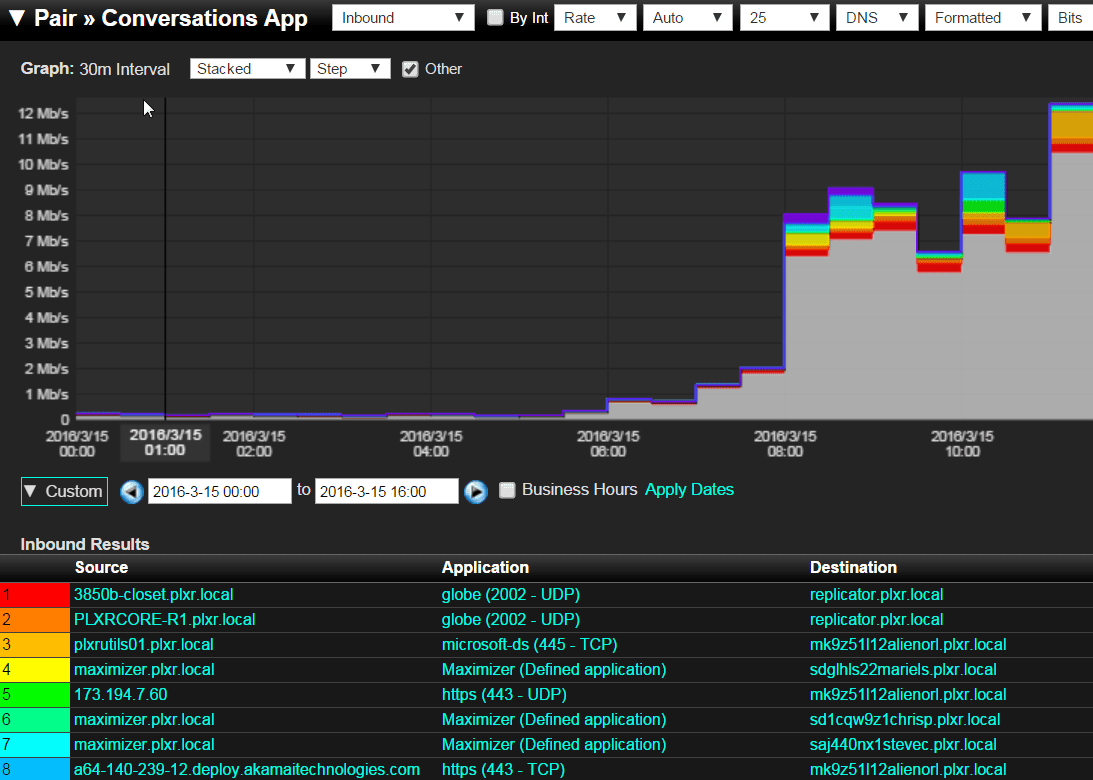
Scrutinizer can also view traffic on applications, their users, and their destination. Insert a FlowPro Defender and get the actual websites the users are reaching out to, even if SSL is involved. FQDNs are especially important when so much traffic today is headed to Akamai and Amazon AWS.
If a particular host is moving lots of data from a website that holds important personal information, this could be a red flag. I recently worked with a customer who was able to drill in and stop a data leak before any damage was done. By using Scrutinizer, they were able to see a particular host and their username generating a lot of traffic from an application that was sending data out to the internet. After taking the machine offline, we were able to find the malicious link the user had clicked on. From there, we were able to quickly and easily make network security decisions.
How can the FlowPro Defender help?
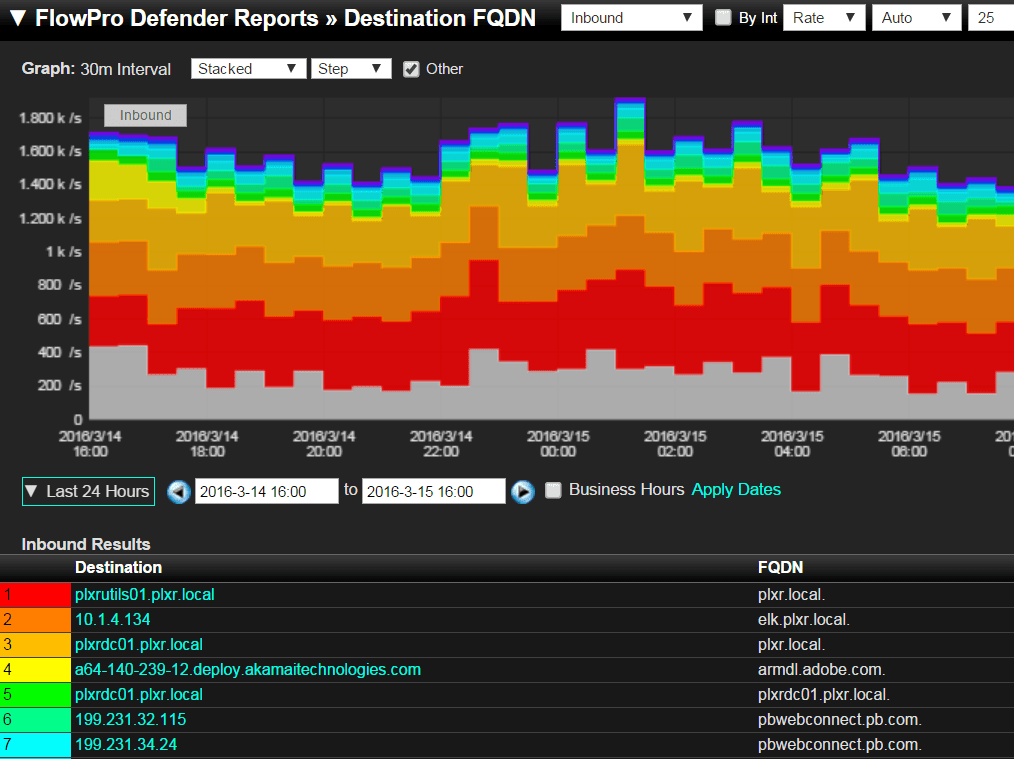
The FlowPro Defender itself comes with a plethora of amazing reports, but the one I’d like to discuss is the ability to view FQDNs. While it’s useful to be able to see that a host is using Port 80 or 443, the ability to view the FQDN helps us paint a picture of an end system’s traffic patterns. Using the FlowPro Defender’s FQDN report, we can see the website visited. This report also displays the source that’s generating the traffic as well as the username that authenticated the device onto the network.
How can I protect my network?
With context-aware security, you will be able to not only generate a baseline of your network behavior, but also verify any malicious activity with ease. If you would like to learn more about the FlowPro Defender or try out Scrutinizer, do not hesitate to reach out to us!


