UPDATE 8/9/17: We have written a more recent blog on this topic, which can be found here.
Back in February at CiscoLIVE! in Berlin Germany we demonstrated our new Cisco ASA FireSIGHT reporting. Since then, I have had many customers asking me how to make this integration possible.
What is FireSIGHT?
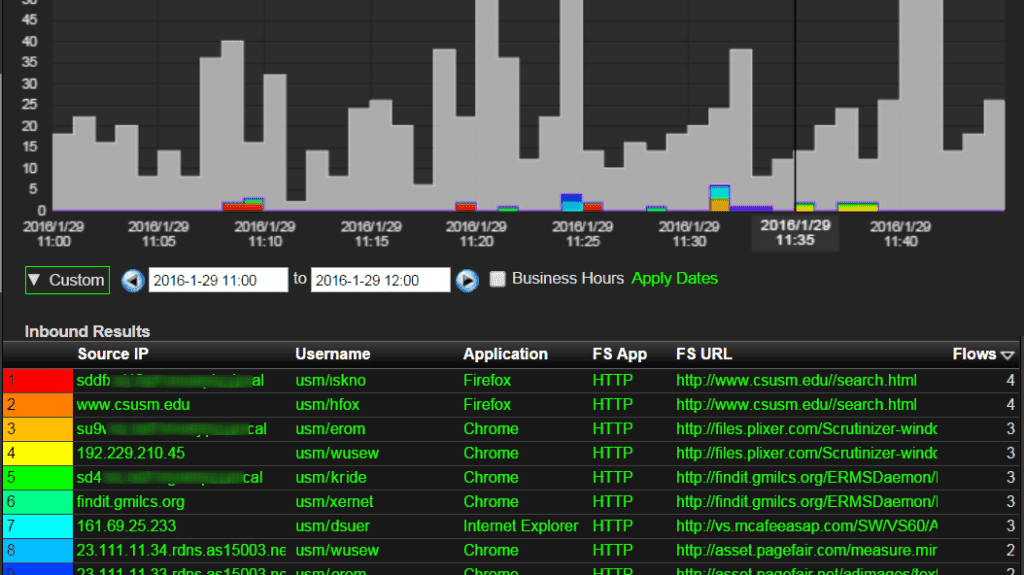
Cisco FireSIGHT Management Center manages network security and features for Cisco ASA with FirePOWER services and network security appliance. FirePOWER provides administration over firewalls, application control, intrusion prevention, URL filtering, and advanced malware protection. By configuring the FireSIGHT eStreamer Client to send flows to Scrutinizer, you’ll have access to 11 new reports that will make threat detection easier and drastically reduce your mean time to know.
Things to Keep in Mind Before Starting
Before we get started on this integration, there are a couple things we need to keep in mind. First, this integration is not available on our Windows platform. If you are currently using our Windows platform we encourage you to consider our virtual appliance or hardware appliances. Second, you should be on version 5.4 of FireSIGHT which would be the latest version. If you currently are on an older version of FireSIGHT an update can fix that. In order to migrate to version 5.2 and then upgrade to 5.4 you must be running software version 4.10.3.5 or higher. You can learn more about this migration here. Lastly, this integration also requires an advanced reporting license for Scrutinizer.
Let’s Get Started
First thing is first, we’re going to need your Scrutinizer collector’s public IP address and the FireSIGHT eStreamer IP address. Now that we’ve got that information we can start the client configuration in the FireSIGHT defense center.
- Log into your FireSIGHT Defense Center
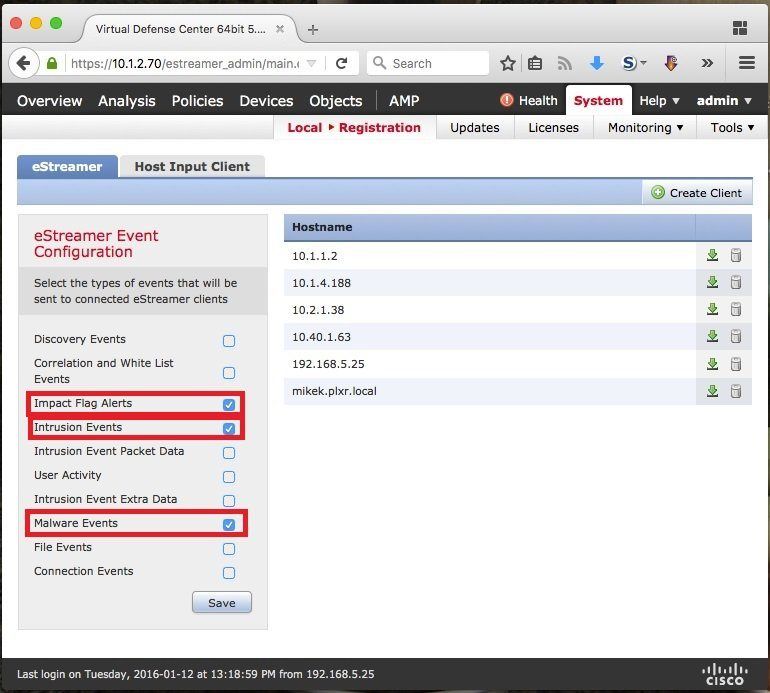
- Go to System > Local > Registration
- Enable eStreamer events and then save by clicking the save button at the bottom of the list. Below is the image where you can check off the events you want Scrutinizer to get. Do not check them all off. Rather, I suggest checking off the ones shown below else, too much data will be sent.
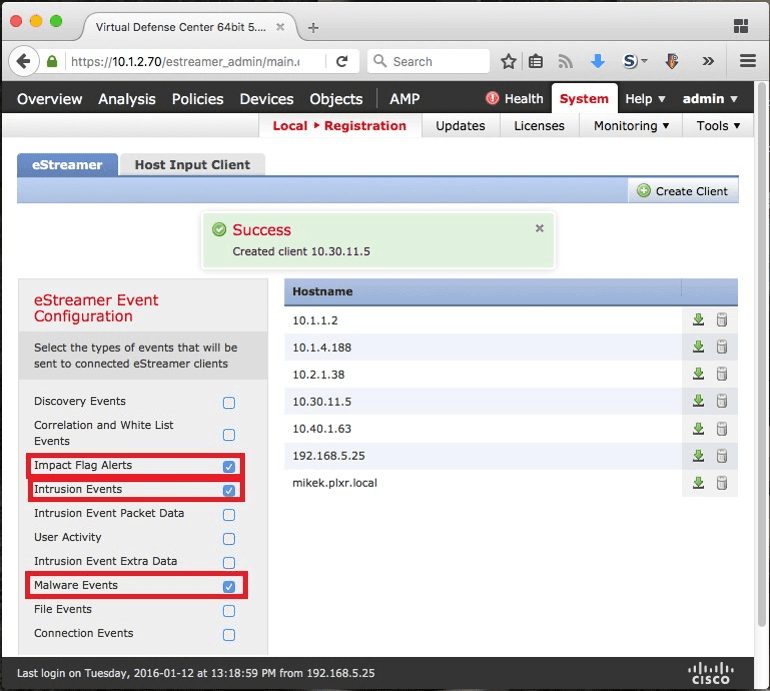
- Click the “(+) Create Client” button on the right.
- In the new window, enter the public IP address for your Scrutinizer Collector
- Enter a password (optional). If you do wish to use a password, remember it since we will need it in a later step.
- Find the new client on the list and click the download button to the right of the client IP. Download and save the certificate.
- Now you’ll need to license Scrutinizer’s eStreamer Client by uploading the client certificate.
- Ssh into the Scrutinizer appliance and navigate to the directory /home/plixer/scrutinizer/files
- Place the newly downloaded certificate in this directory. This can be done by using a client such as WinSCP or by using a tabbed SSH client such as MobaXterm.
Configure Scrutinizer’s eStreamer Client
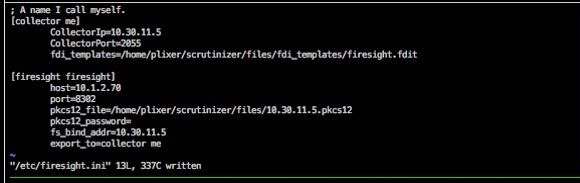
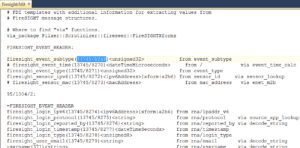
Next, you need to edit the /etc/firesight.ini file found in the etc directory and specify which events you want Scrutinizer to collect.
Editing the firesight.fdit will display a file that looks like this:
We commented out a bunch of elements by default. They have a ‘#’ in front of them.
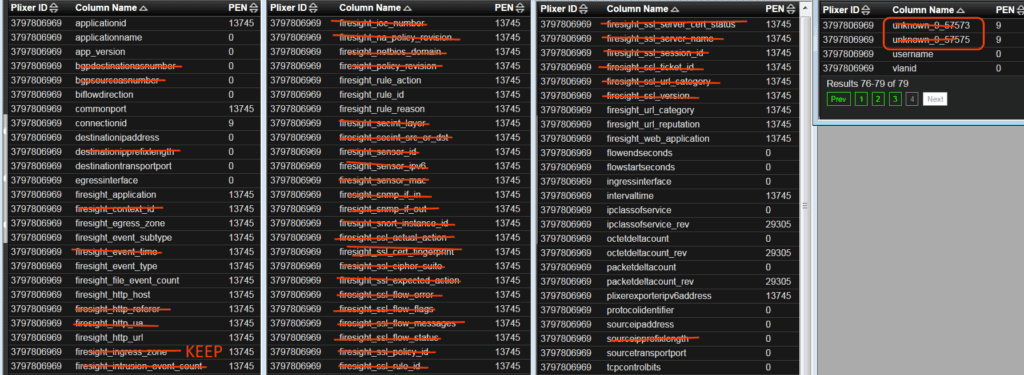
Below is all of the elements we can export and a red line is through the ones we disabled by default. In other words, we are only collecting the ones that are not crossed off.
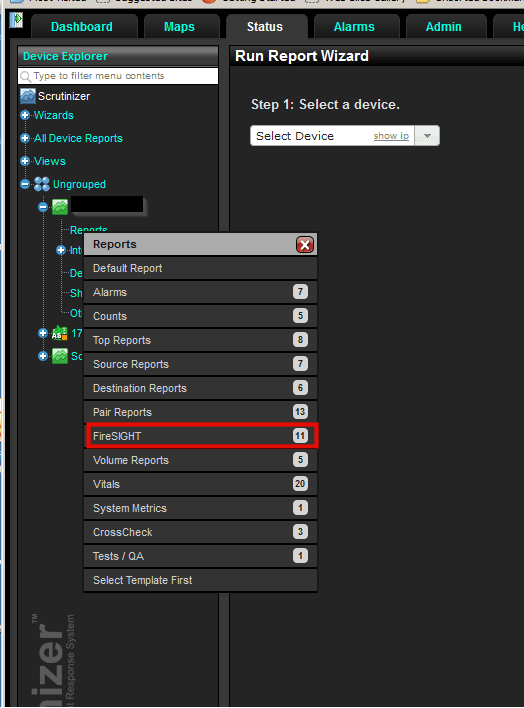
Once this is configured, you should start seeing flows into Scrutinizer within 10-15 minutes. To find these flows navigate to the status tab and under the device explorer, select ungrouped, and select the IP of the Scrutinizer server. Once you’ve selected the reports option you should see FireSIGHT appear in the menu.
And there you have it! If you have any questions about your FireSIGHT integration do not hesitate to reach out to our support team at 1-(207)-324-8805 x4. We’d be happy to help out in any way we can.
Peace, love, and NetFlow!