In a previous blog I introduced you to the malware detection capabilities of Plixer’s intelligence product. I would like to circle back to some information shared in that blog to talk about its ability to detect behaviors like lateral movement across the LAN segments of the network related to data accumulation.
Before I get started, I want to talk about strategies used for network visibility and why flow technologies should be at the top of the list.
Using flow exports from network routers, switches, and firewalls, administrators can realize across-the-board network visibility. Every conversation that traverses a switch, router, or firewall is collected, analyzed, and available for forensic investigation.
Flow technologies use a configurable option that already exists on most vendor network devices. There is no additional cost associated with deployment of capture appliances; you already own the network equipment and the flow option.
Deploying packet capture technology in the network can get very costly. You end up picking and choosing where you get visibility from. Ultimately, you will rarely achieve anything close to the network visibility that you are looking for.
Instead, flows give you top-to-bottom visibility from anywhere in the network. When flow data is collected, the fingerprints/conversations involved in the propagation and/or lateral movement within the network are available for forensic investigation. The flows provide verification and evidence of movement.
The use of flow technologies for network behavior analytics is something that Plixer has done for years. In fact, Plixer has been recognized as the Most Innovative in Network Detection & Response. This award validates our efforts to lead, innovate, and shape the NDR market space.
Running the flows collected through a suite of analytic algorithms looking for suspicious behaviors has been a solid way to bring attention to possible suspicious traffic that might be occurring on the network. But today the bad actors are very good at hiding their trail. Attacks are carried out in strategic phases. It’s the lateral movement across the network from private addresses that need your focus. The analysis of traffic from all network segments provides an immediate notification if a host exhibits new or suspicious traffic behaviors.
Time to investigate a data accumulation alert
A data accumulation alert is triggered when an internal network asset is seen collecting data from another internal asset.
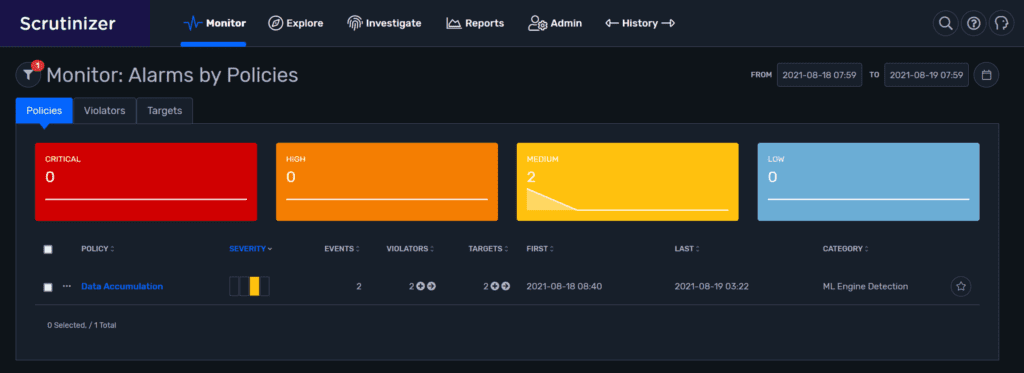
Checking the Alarm Monitor, we see that we have detected a data accumulation traffic scenario.
The alarm tells us that we have seen two violators and two target IPs involved in the alarm. We also know the time frame as in first seen, last seen.
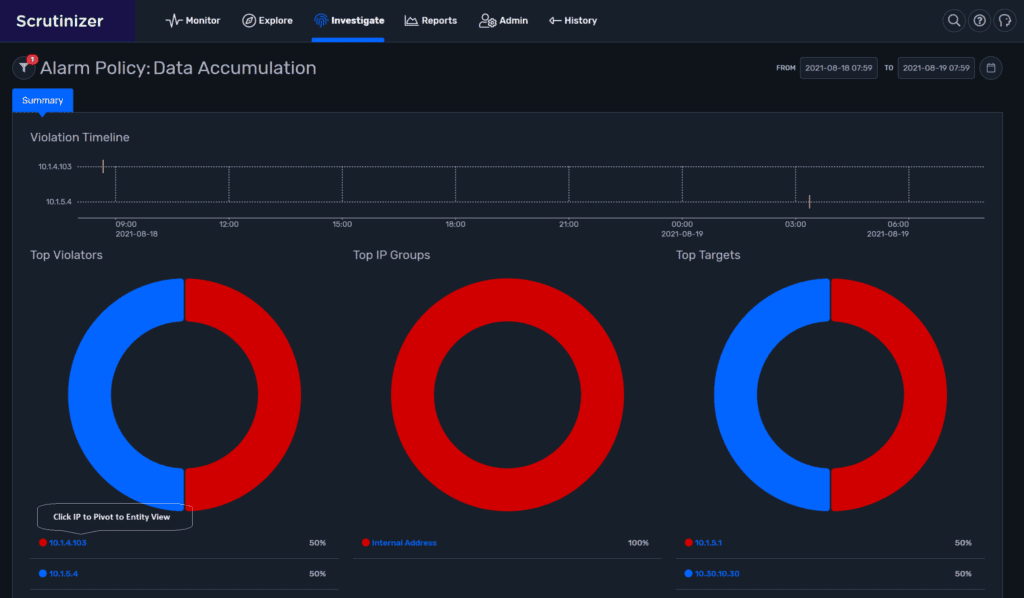
Drilling into the alarm shows us its timeline, the IP addresses of both violators and targets, and the IP segment the violator is a member of.
You have a couple of options in this alarm view.
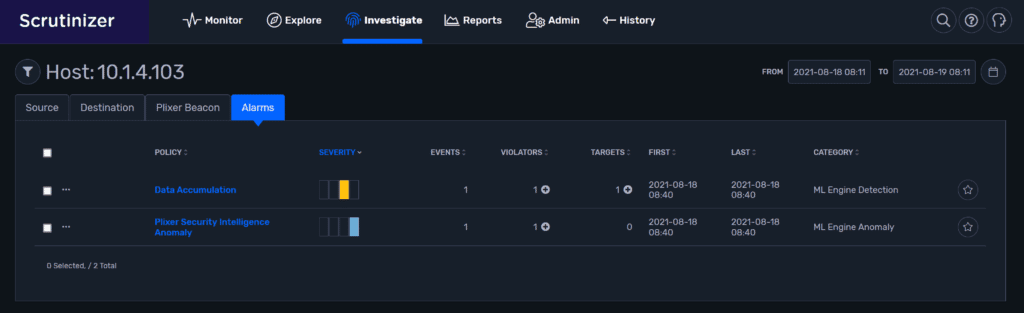
The first option is to click the violator IP to pivot to an entity view of the IP host where we can see correlating alarms, or basic source and destination information.
The second option is to click to see alarm messaging where we learn more about observations and who’s talking to whom.
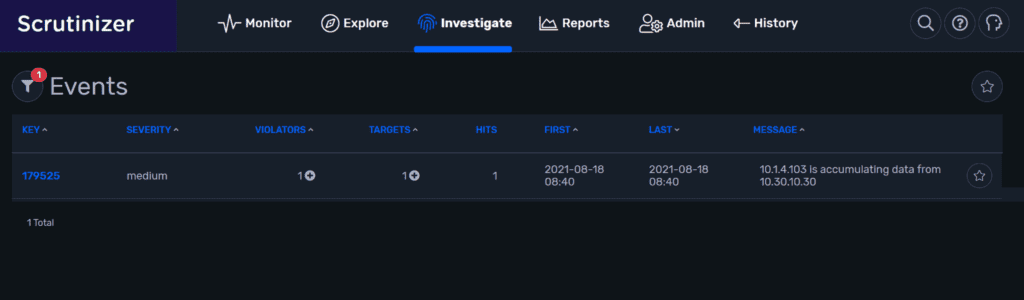
Here we can see that 10.1.4.103 is collecting data from 10.30.10.30.
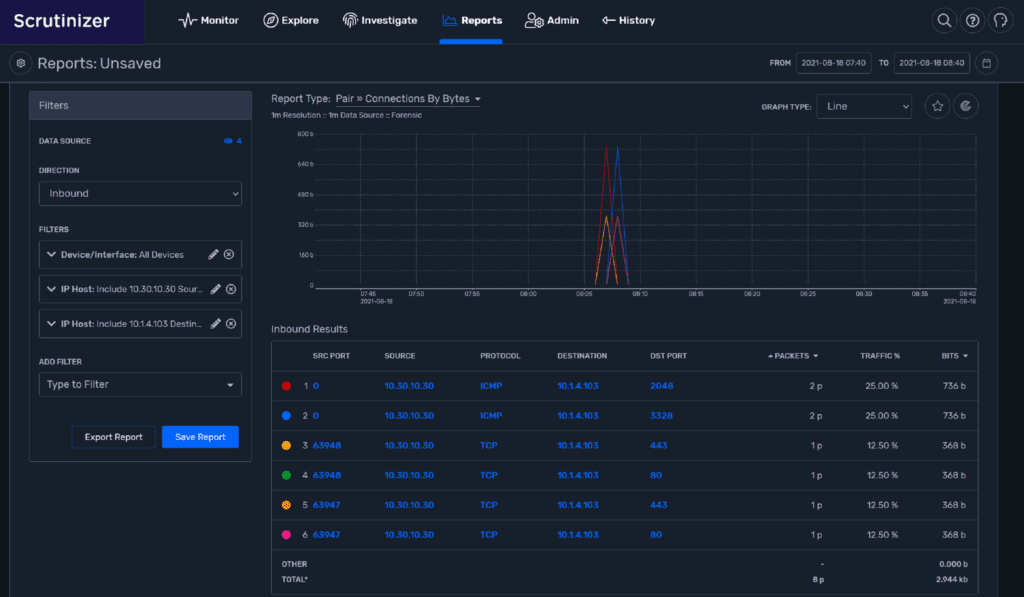
A click on the Run Report option in the alarm shows us the collected forensic data that triggered the alert.
Note that we are not talking about a large amount of data. Data accumulation is occurring in very small steps, single packets at a time.
When it comes to the detection of network traffic anomalies, fast and actionable data is enterprise intelligence. If you want to see Plixer Scrutinizer and Plixer Security Intelligence in action, book a demo today.