Transform Network Insights for a Strategic Advantage
Gain unparalleled network visibility for enhanced cybersecurity and peak operational excellence.
Deploy
in Hours
Secure your enterprise in as little as an hour for faster protection with non-intrusive, agentless deployment.
Prioritize
Critical Threats
Gain a noise-free, 360° view of your network to quickly identify, prioritize, and respond to critical threats.
Scale without Compromise
Customize a dynamic platform with advanced Network Performance Monitoring (NPMD) and Network Detection and Response (NDR) solutions that adapt and grow with your business.
Risk
Mitigation
Reduce the financial and reputational risks of a potential breach with cost-effective solutions and lower Total Cost of Ownership (TCO).
Join the Intelligence Revolution
Plixer One revolutionizes NDR and NPMD in complex digital landscapes with a powerful, streamlined platform that enhances network visibility, bolsters security, and optimizes performance.
Explore Plixer One
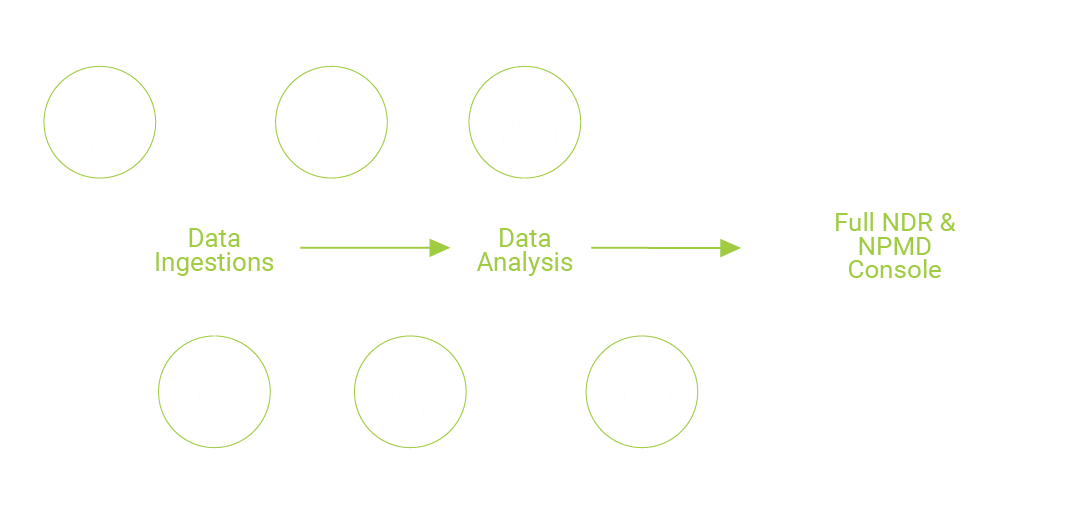
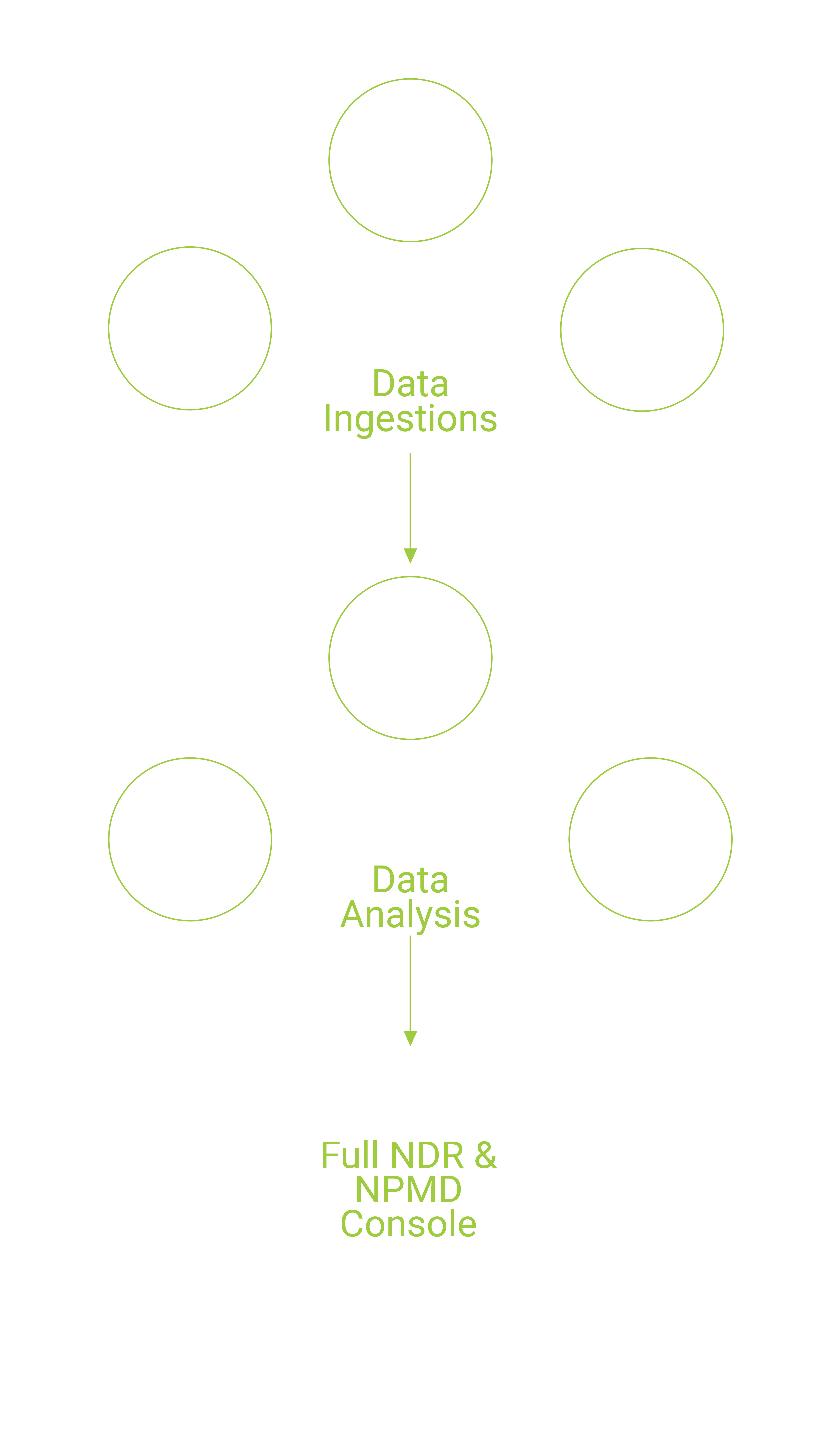
Rapid Deployment Model
Meet Our Customers
Resources & Information

Security Brief: MOVEit Vulnerability
Exploits of vulnerabilities present in the file transfer system MOVEit have been all over the news. But what is it and what can you do to protect yourself from an attack? This whitepaper walks you through the MOVEit vulnerability, how it’s being used to attack organizations, and what you can do about it.
Endpoint Visibility Gap
Despite significant progress in cybersecurity, endpoints remain a persistent concern for security professionals worldwide. Gaining visibility into and understanding endpoint activity can significantly mitigate risks and preemptively stop potential attacks. This whitepaper covers the ongoing challenges posed by endpoints in security and offers strategies to safeguard against potential threats.